Check that you're ready for invasive DRM with new feature built right into Steam — Secure Boot and TPM status now listed right in the app
A secure boot a day keeps a virus away.

Ever since the release of Windows 11, if you're a PC gamer, you've definitely heard the term "Secure Boot." It's required to play a myriad of different games these days — mainly competitive shooters — and serves as one part of the two-punch security knockout consisting of TPM and Secure Boot. These features help keep your system protected from bad actors, and now Valve has just made it super convenient to check whether you're ahead of the curve. In the latest Steam beta, you can easily see your Secure Boot status in the settings.
If you open Steam and go to "Help" in the menu bar and click on "System Information," you'll be bombarded with a bunch of stats about your PC. Just scroll down till you see the "Operating System" heading, and you should see a list item for Secure Boot, telling you if it's enabled. This makes it easier for gamers who get inundated with information to ensure they're not excluded. While you're there, you'll see your TPM status as well, which is the other big security feature of Windows 11 and a requirement for (official) compatibility with the OS.
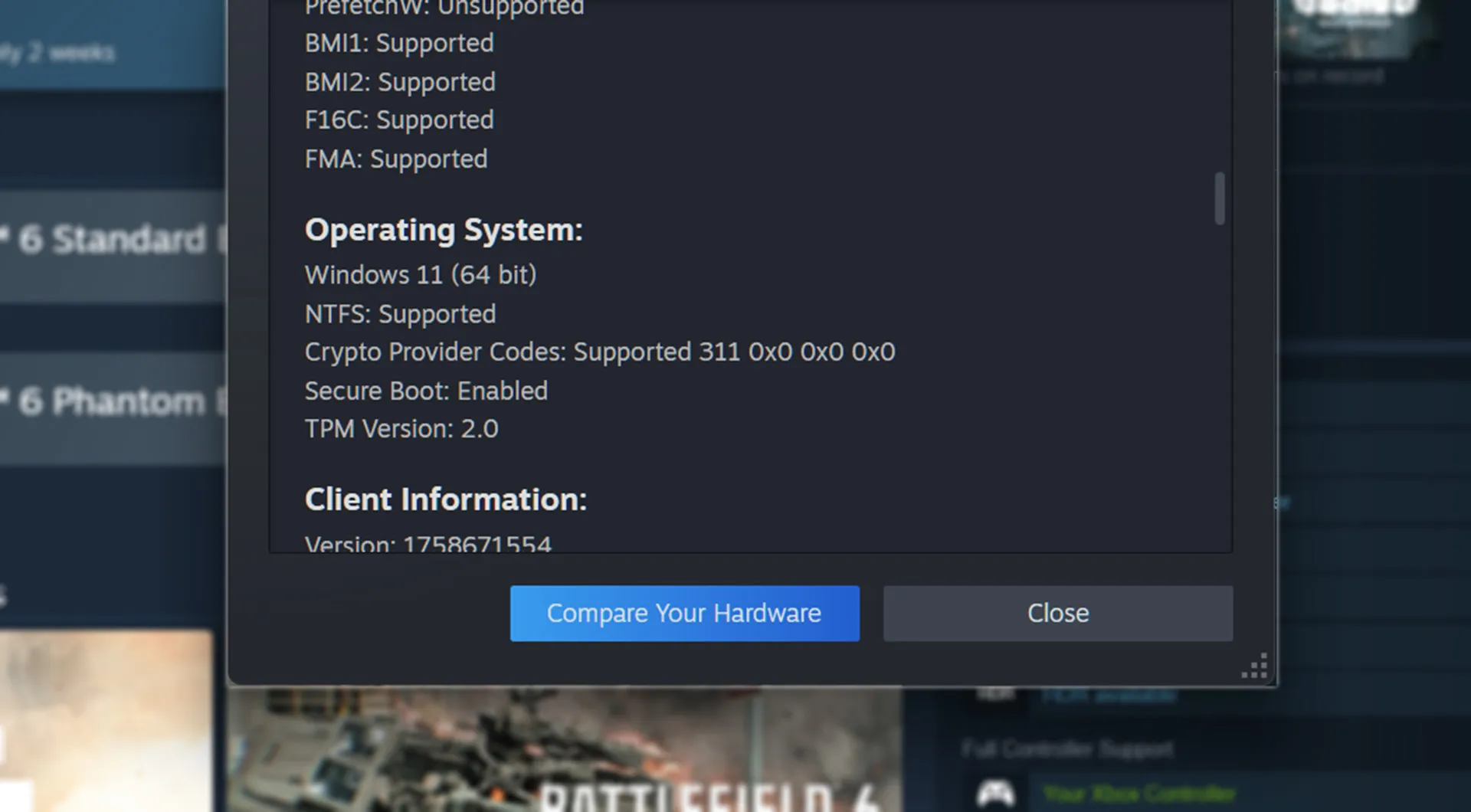
TPM stands for Trusted Platform Module, and it's a little hardware block that's cordoned off from the rest of the system because it houses ultra-sensitive cryptographic keys. It works hand-in-hand with Secure Boot to check if anything has changed since the last known good boot. It does that by recording hashes at each stage of every boot run to tally against, which is just one secret, along with many others (like BitLocker encryption keys) that are stored away in this chip. TPM is a requirement in most modern online games, just like Secure Boot.
Secure Boot works to ensure that only trusted, signed software runs when your PC starts, in an effort to sift out any shady programs. It's a kernel-level security feature, so it enjoys the highest level of privilege on your system — something that its critics often point toward as a vulnerability. Secure Boot, in essence, is a novel concept and is designed to do what it says: make your boot secure, but sometimes the amount of access it has can raise questions.
That's because most anti-cheat software is reliant on Secure Boot as it's essentially responsible for creating a safe space for the anti-cheat right as your system is starting, from where on out the anti-cheat can catch any exploits or malicious code itself. This can get really territorial, as recently seen with EA's Javelin in Battlefield 6. Without Secure Boot (and often TPM), some games won't even launch, so it's important to enable it if you see it turned off in Steam. To do so, you need to head over to your BIOS; check your motherboard manufacturer's guides for more info.
Follow Tom's Hardware on Google News, or add us as a preferred source, to get our up-to-date news, analysis, and reviews in your feeds. Make sure to click the Follow button!
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.

Hassam Nasir is a die-hard hardware enthusiast with years of experience as a tech editor and writer, focusing on detailed CPU comparisons and general hardware news. When he’s not working, you’ll find him bending tubes for his ever-evolving custom water-loop gaming rig or benchmarking the latest CPUs and GPUs just for fun.
-
edzieba The Secure Boot status is also visible within Windows (Windows Security > Device Security) without needing to launch and log into a shop application to tell you.Reply -
Notton And if you don't like secure boot?Reply
Install steamOS (or whatever flavor of linux), I guess. -
palladin9479 Secure Boot does not protect you from malicious software. It's just a way to ensure integrity of the boot loader. The hash of the bootloader is kept in the TPM module and when the BIOS goes to boot, it'll check that the hash's match before handing off the boot process. In theory this prevents someone from using a bootable USB/DVD device and overwriting or modifying the bootloader. Of course if someone has physical access to do this, they also have access to alter the hash value stored in the TPM module. Basically this only protects against rootkits, which used to be super common but have since died off in favor of privilege escalation from phishing someone.Reply
MS does not have some sort of ultra-violet secret backdoor access to these chips, the exact same API hooks they use to upload the hash values during installation or update are the same hooks I can use when I modify the boot loader. This applies to the Full Disk Encryption that TPM was really made for, if I have access to the module then I have access to the encryption keys kept inside the module. The only way to keep me out of the module would be to use a strong passphrase that would be required to unlock the module prior to boot. So how many people here have TPM + Secure Boot enabled along with a boot passphrase? Yeah thought so, that means it's just security theatre.
The real reason for game publishers wanting to use the TPM is that they can use it like a thumbprint for DRM.
And just to hammer home how much TPM is just security theatre, I present the PCIe DMA card.
https://www.amazon.com/Model-35t-DMA-Card-Compatible/dp/B0DJWGZ1NJ
Anything on the PCIe bus can access memory directly via DMA, this is how you load stuff into and out of your GPU's VRAM and how we can use CUDA to crunch data. This device allows a second PC to directly scan through and modify any value in memory without any intervention from the OS or kernel. It can be used to extract any encryptions keys that were loaded during boot, modify any code or data stored in memory, and pretty much do anything on the computer. The card costs, drum roll, $139 USD. -
edzieba Reply
And the fall in rootkit and bootkit-based attacks as Secure Boot was adopted is just a coincidence?palladin9479 said:Basically this only protects against rootkits, which used to be super common but have since died off in favor of privilege escalation from phishing someone.
Like with OS security patches, just because attackers have moved on from targeting those exploits because they were patched, that is not a good reason to remove the patches.
Also, TPM != Secure Boot, the two are entirely different things and can both be implemented independently. Vulnerability to local hardware attacks (let alone memory snooping) is also irrelevant for Secure Boot, as it was never designed to defend against those attacks in the first place. -
hotaru251 Replycreating a safe space for the anti-cheat right as your system is starting, from where on out the anti-cheat can catch any exploits or malicious code itself.
let me edit this bit:
"can ATTEMPT to catch any exploits"
If this worked like the statement claims there would be no cheating (and we all know that isnt the case) -
Joomsy I'm just gonna leave this here. Not arguing against the use of Secure Boot outright, but making anti-cheats reliant on it is going to be ineffective when things like this are possible. Commercial cheat makers salivate over this kind of stuff, and they already employ tactics used by malware controllers to gain kernel access. They use vulnerable drivers that they can bundle with their cheat. I can bet one of them will eventually incorporate a bypass for Secure Boot.Reply
https://www.darkreading.com/vulnerabilities-threats/hybridpetya-ransomware-bypasses-secure-boot -
palladin9479 Reply
Yes, the fall off happened before secure boot was standard. It's security theater because of how easy it is to bypass. It only really protects against the meme of booting off a random usb stick or cdrom you found. The OS kernels already has the ability to update the boot loader and code signing key.edzieba said:And the fall in rootkit and bootkit-based attacks as Secure Boot was adopted is just a coincidence?
TPM is involved because TPM 2.0 allows for the TPM module to hold the code signing verification key. TPM itself is only secure if you are using a safe passphrase provided at boot to unlock it. Anything less and it's not protecting squat.
The important part is that MS doesn't have any double secret access to your BIOS or any other firmware. Anything they can do, the device owner can do and therefore any code that owner is tricked into running can do.
In other words, your motherboard ask Microsoft for permission when you change something. I don't need some clever hack, I just need to trick you. -
Amdlova The best way to keep your protection it's to have two computers. One system you only do good things and another to do bad things.Reply
How many times I get infected because I need to test something. Virus.exe I need to double click to really check if my system will got the flu. -
snemarch I wouldn't go as far as saying that Secure Boot is security theater – most people's threat model doesn't include evil maids attacks, or protecting against three letter agencies kicking in their door and extracting bitlocker decryption keys. For normies, it removes the "easily drop boot/rootkit payload" attack vector, which is good.Reply
Of course it doesn't protect against social engineering "run this .jpg.exe as administrator", but nothing really does ;)
The nasty thing about secure boot is that it's a critical piece of remote attestation chain of trust. If we normalise secure boot being a requirement for games, when will lockout based on driver allow-list attestation be added? Slowly boiling frog, etc.