Toshiba Reveals Self-Wipe HDDs, Hide Your Vids!
Toshiba is adding Wipe Technology to its Self-Encrypting Drive HDDs.
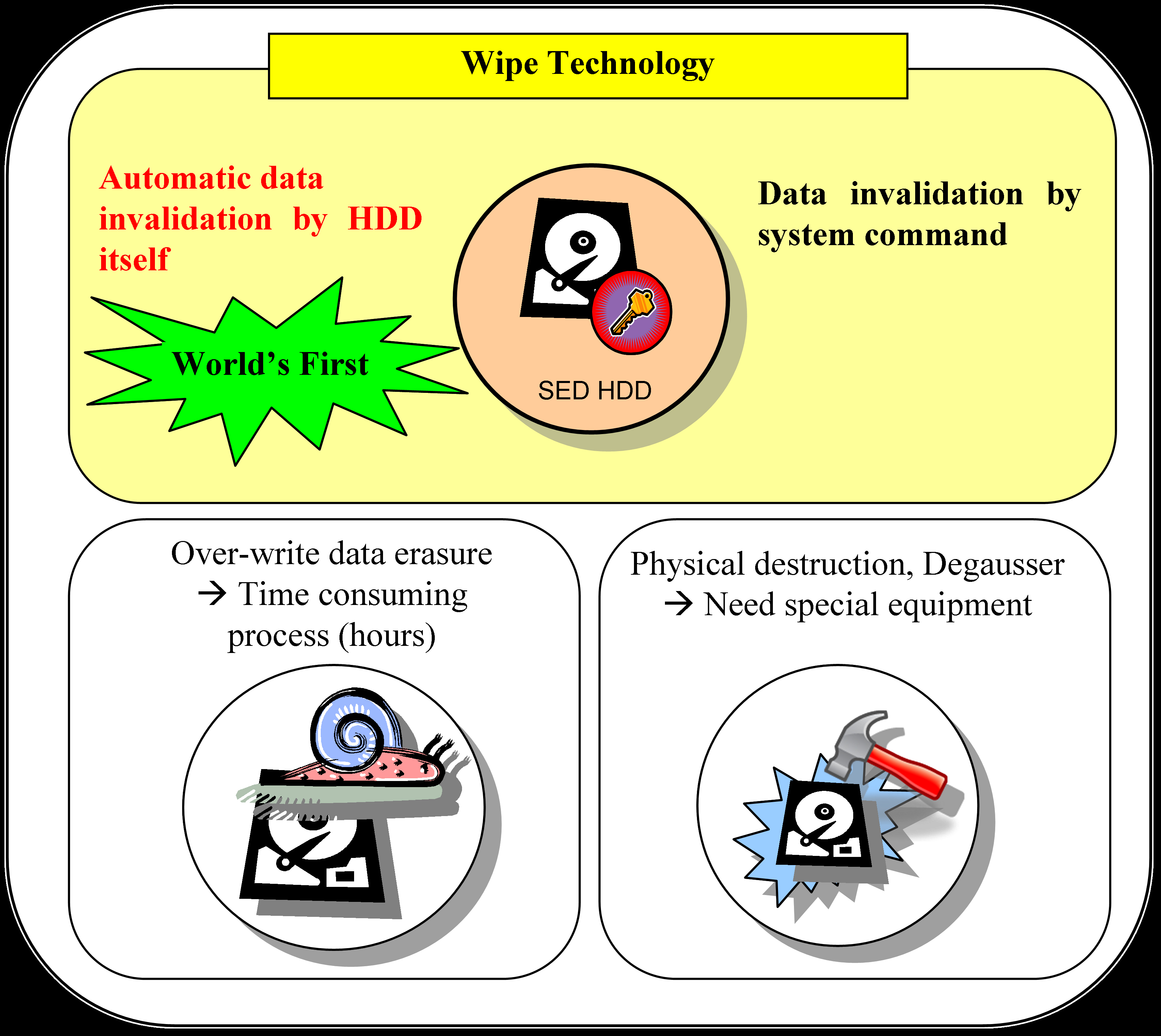
Monday Toshiba revealed a new technology for its Self-Encrypting Drive (SED) hard drives that allow for secure wiping of sensitive data when a system is powered down, or when the HDD is physically removed from a system. Called Wipe Technology, the new tech could also be used to erase user data before returning a leased system, or before a defunct system is taken out to the trash.
But there's a catch: the data isn't really deleted. When the drive's power supply is severed, Toshiba's Wipe Technology merely invalidates the security key that was originally used to encrypt the stored data. Without the key, data becomes indecipherable and virtually "erased" to would-be snoops. Now nervous administrators won't have to worry about company notebooks loaded with sensitive info being left behind at the local bar.
Although Toshiba's Wipe Technology would be ideal for government use, the company indicated that copier and printer systems vendors would benefit by automatically erasing the SED's internal encryption key, eliminating "data at rest"--sensitive document images stored on the hard drives inside copiers and printers.
"This feature can easily be used prior to system disposal or re-purposing to ensure that private data never leaves the control of the responsible business unit or IT department," Toshiba added. Wipe Technology also reduces overall time investment to secure data, removing the need to use overwriting software to erase data or physically destroy a device.
Toshiba's new Wipe Technology will be included on the 2.5-inch 7200rpm SED HDD announced last month. The drive will supposedly offer on-board encryption and improved access security for both notebooks and desktops. It was also designed with the Trusted Computing Group "Opal" Specification in mind.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.

Kevin Parrish has over a decade of experience as a writer, editor, and product tester. His work focused on computer hardware, networking equipment, smartphones, tablets, gaming consoles, and other internet-connected devices. His work has appeared in Tom's Hardware, Tom's Guide, Maximum PC, Digital Trends, Android Authority, How-To Geek, Lifewire, and others.
-
tpi2007 Hmmm.. on another note I tried to use the Secure Erase DOS utility from the University of California a few days ago on my WD Caviar Blue 640 GB and it said the drive didn0t have that ATA feature (Built-in data shredding which is much faster and secure) implemented.Reply
So how's that for security when this subject is little talked about - and by that I mean that all modern ATA/SATA drives should have the Secure Erase command built-in, but don't, along with the fact that no company alerts the user who sells their used HDD's on ebay or disposes of them, thinking that a simple format or file overwrite is enough ?
I know that the State must love this ignorance because it makes forensic data retrieval a lot easier, but in the end ingnorance is never good for anyone. -
dextermat do you really think the government can't get into a locked hard drive lol.Reply
Im pretty sure a good hacker can get into it without you even knowing about it!! -
jerreece You mean to say that putting my credit card bills in my garbage can doesn't erase them permanently??? I might have to start shredding and then burning them all...Reply
*sarcasm*
Though deleting the key is a great feature, I'm sure someone who's really, really compelled to do so will find a way to break the code at some point. -
Onus Bad title; these drives do not "self-wipe" if all the data is still there, even if encrypted.Reply
-
bison88 nevertellStill waiting for a drive with built-in chip for AES encryption.Reply
Touche. Intel has already integrated an AES chip set into their i7 processors which TrueCrypt can see a 5x+ performance gain. However, the problem with encryption is for half the folks they are going to take any kind they get and run with it blind while the other half is constantly paranoid about it doing its job and putting all their eggs in one basket. To that effect TrueCrypt has built up such a reputation that many don't want to use the Intel design even though it's faster because they are paranoid that Intel sabotaged the design and isn't "Secure". It's really an unwinnable battle when you speak about encryption.
However if you combine both Wiping + Encryption it's a pretty solid bet that you will be safe especially if you encrypt a file before performing a DOD 3 execution wipe method. Even that is overkill when it comes to wiping data. Like a good conspiracy theory that is believable, you have to just look past the possibilities and go on living your life with caution and not getting hung up on what may be possible and what isn't, with data it's the same way. I don't think people should fear the government as some mastermind overlords that nothing isn't within their reach. -
hellwig I think many of you underestimate the effectiveness of modern encryption. Remember that guy that used PGP to secure his kiddie porn a while back, and the government tried to coerce him to give over his password cause they couldn't break it? The government might not use PGP for state secrets, but its good enough to outwit your everyday law enforcement.Reply
My point is, any businesses considering this technology (and any potential home users) don't have enemies powerful enough to break this encryption, and thus, wiping the key is good enough for the foreseeable future. Sure, someone, someday will be able to decrypt the data, but by then, will anyone care (will the data be relevant, will the drive still even exist)? -
digitalgriffin I know someone who recovers lost hard drive data for a living. You would be surprised how many times something can be overwritten and still recovered. Luckily encryption is previous data dependent. Meaning if you can wipe just 1 character in the current block sequence effectively, then the data is reasonably protected because it will yield vastly different data for the rest of the block, even if all those bytes are successfully recovered.Reply
I cringe everytime I know millions upon millions of dollars of secret research and data is being thrown out on an unsecure drive.
Wipe the key, then wipe the disk. (Or degauss it or destroy it!)