Finalized FIDO 1.0 Spec Will Rid The World Of Passwords

Today, the FIDO Alliance announced that its version 1.0 specifications are now published. Thanks to these specifications, passwords could become obsolete for all devices and services in the coming years, as adoption ramps up.
"Today, we celebrate an achievement that will define the point at which the old world order of passwords and PINs started to wither and die," said Michael Barrett, president of the FIDO Alliance. “FIDO Alliance pioneers can forever lay claim to ushering in the 'post password' era, which is already revealing new dimensions in Internet services and digital commerce."
The FIDO Alliance was formed in February 2013 with six founding members: Nok Nok Labs, Lenovo, Infineon, PayPal, Agnitio and Validity. Since then, more companies such as Google, Samsung, Microsoft and Yubiko have joined it. The FIDO specifications have seen the fastest growth in the history of identity management solutions. Not even two years have passed since the FIDO Alliance's inception, and version 1.0 of the specifications is now finished, with large adoption from the technology industry.
"The fact that the FIDO Alliance was able to develop complete specifications so quickly and with such broad support is evidence that they are tackling a pervasive industry pain point," said Steve Wilson, Vice President and Principal Consultant at Constellation Research. "No consortium in the identity management (IdM) industry has every grown so fast, with such strong representation from the technology buy side. What's most impressive is the FIDO Alliance’s focus on the authentication plumbing. The protocols enable trusted client devices to trade just the right data about their users. FIDO specifications aren't tangled up in messy identity policy decisions. It's an elegant breakthrough, and, going forward, it should drive a lot of the classic complexity out of the IdM space."
The two main specifications that were published today are the Universal Authentication Framework (UAF) and Universal 2nd Factor (U2F). We've discussed the U2F specification before, when Google announced its "Security Key" protocol in partnership with Yubiko, which created the USB keys that could be used as a second factor in authenticating to Google services.
Now that the U2F spec is finalized, more online services can adopt it, and you'll be able to use either Yubiko or some other company's two-factor USB key as long as it's FIDO U2F-compatible.
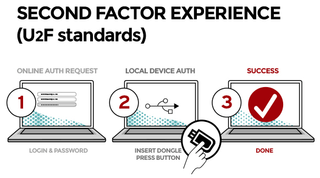
The way U2F works is like this:
Stay on the Cutting Edge
Join the experts who read Tom's Hardware for the inside track on enthusiast PC tech news — and have for over 25 years. We'll send breaking news and in-depth reviews of CPUs, GPUs, AI, maker hardware and more straight to your inbox.
- User carries U2F device with built-in support in web browsers
- User presents U2F device
- Website can simplify password (e.g., 4 digit pin)
The UAF specification will provide the actual password replacement (U2F is a replacement for other two-factor authentication methods), making logging-in to devices or services passwordless.
Instead of using a password, the user will be able to login using fingerprint, voice or facial recognition, depending on what the service chooses to provide. With UAF even PINs can be used, or a combination of all of these methods, to strengthen the security of the authentication. Optionally, web services may continue to ask for a password as well.
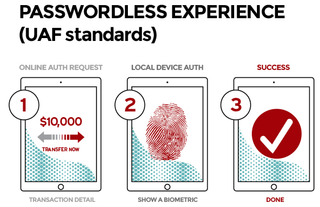
Here's how it should work:
- User carries client device with UAF stack installed
- User presents a local biometric or PIN
- Website can choose whether to retain password
The FIDO specifications will be updated next year to support NFC and Bluetooth as extensions. For instance, you can't insert the typical USB key into a smartphone to authenticate it, but you could do it wirelessly through NFC or Bluetooth. Users could also have a FIDO-ready smartwatch, but not a FIDO-ready smartphone, and then they can authenticate to services on their mobile device through the smartwatch's NFC or Bluetooth connection.
Now that the FIDO specification is finished, we should see more devices supporting such authentication methods next year. Samsung's Galaxy S5 already supported it in order to allow fingerprint authentication into the PayPal app, so we can at least expect the Galaxy S6 and Galaxy Note 5 to support it, as well.
Follow us @tomshardware, on Facebook and on Google+.
-
Scott Baylor U2F device? Hasn't USB been found to have a "fatal flaw"? Yeah that's more secure than passwords.Reply -
Anonymous333 How does the second WIFI signal affect the data cap? Meaning I believe Comcast provided a cap on data per month, if you go over this they will want you up to 3 times then charge you extra for the extra data you use. Will this second WIFI signal eat into the customers data cap?Reply -
jrl657 What does a flaw in USB have to do with U2F? USB just carries the data created by the device plugged into it. The Data is a OTP or a short lived key to allow you to login to a site. Similarly bluetooth or NFC can carry the data. The data itself is only valid to the end app to prove you have the device it expects you to have and carries no info about you.Reply -
seabeebrian I've had a Yubico key for about a month now and use it exclusively for authentication with Google. I know it will work with lastpass but I have not yet set it up. So far I am impressed. I would love to see a list of services and websites that support it.Reply -
sathen07 Oh good, so now hackers WILL gain access to my home address, my financial information and now my personal biometric information . . .Reply -
InvalidError I might use such a device IN ADDITION to passwords for two/tri-factor authentication but not as a replacement since that would make it a potential single-point-of-failure in the whole security chain.Reply
If you still have to remember a PIN, then that sounds like a failure to actually remove passwords since you still need to remember one in the form of a PIN. If the PIN is per-site, then this is about as annoying as passwords and if it is a global PIN, then you are boned if someone who knows your PIN steals your dongle. -
serendipiti (man in the middle attacks).Reply
Let's suppose you get a phone call from your mother.
The voice is so bad you aren't able to recognize it. How can you assure she is your mother ? just ask her something only she will know. No matter if someone else can listen or talk, only your mother will know the correct answer. -
ChronosVRdS ReplyU2F device? Hasn't USB been found to have a "fatal flaw"? Yeah that's more secure than passwords.
And that's what happens when you only read the news highlights, USB has no "Fatal Flaw", yes there is a new attack and yes most of USB devices are vulnerable especially mass storage with upgrade firmware feature, but it doesn't affect every single USB device.
Most Popular







