Heartbleed-Level Vulnerability Found In 950 Million Android Devices, Thanks To DRM
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
You are now subscribed
Your newsletter sign-up was successful
A serious vulnerability discovered by the researchers at Zimperium, a security company, allows attackers to infect the vast majority of existing Android users (over 950 million) through a simple MMS message without any action from the user.
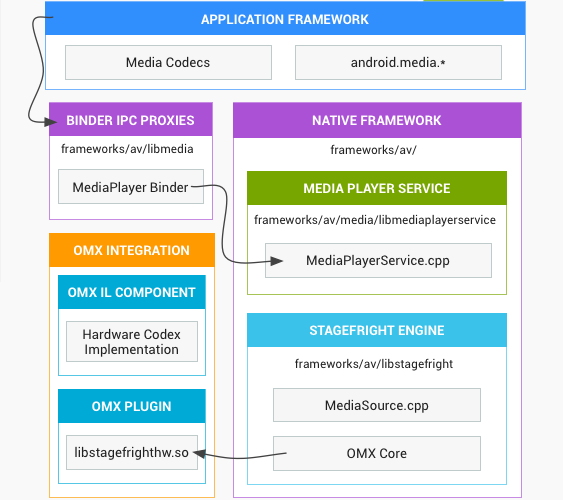
The Zimperium researchers discovered multiple vulnerabilities in the Stagefright media library in Android, which is written in C++, allowing for easy exploitation, and has almost root-level privileges and Internet access. The researchers believe that these excessive permissions in the library are due to it supporting some types of digital rights management (DRM) processing or streaming playback. However, they ultimately make the devices highly vulnerable to silent exploitation in the background.
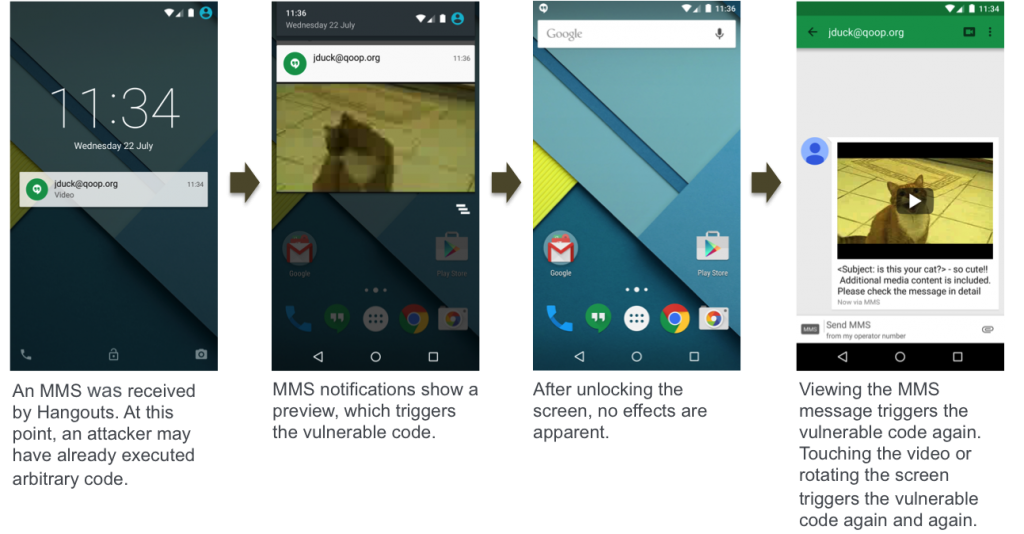
If an attacker wants to target someone, he would only need to know the target's phone number to which he could send the MMS message. The target may not have even seen the message as the attacker could delete it remotely as well, after the device was infected. An attacker could choose to do this operating during night time for the victim to minimize the risk of exposure. The only remnant of the attack could be a notification message on their screen for the MMS message, but without the MMS message itself.
If the attacker doesn't want to attack any particular target but would just want to infect random people's devices, then he could generate the phone numbers randomly or use a database of phone numbers to which he can send the MMS messages. This way he could infect millions at once.
The Stagefright and Heartbleed vulnerabilities have little in common in terms of how they work, but the level of danger here seems to be roughly as big, if not bigger for the Android vulnerability. As with Heartbleed, which was a bug that allowed malicious hackers to steal information from most OpenSSL servers, the attackers can send malware to anyone running Android 2.2 up to Android 5.1.1 (which is the latest shipping version of Android).
Although developers could upgrade their own servers to patch Heartbleed, which most did, Android users won't be able to upgrade their devices to a safe version unless the OEMs and carriers make that upgrade available. The bad news is that even if Android OEMs update all devices running Android 4.4 and up, that would still leave 48.4 percent of users vulnerable to this bug.
However, chances are that not all Android 4.4+ devices will be patched, so most Android users could still remain vulnerable until they replace their phones. Versions that are older than Android 4.2 are in even greater danger, because they lacked exploit mitigations that were added to newer versions of Android, as well as a way to disable automatically receiving an MMS.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
The Zimperium researchers have already told Google as well as Silent Circle and Mozilla, who also use the Stagefright library, about the vulnerability, and the companies have prepared fixes for their own operating systems (Android Open Source Project, PrivatOS and Firefox OS, respectively).
Silent Circle already fixed the vulnerability in version 1.1.7 of PrivatOS, and Mozilla fixed it in version 38 of Firefox OS. Although Google has pushed the patch to the AOSP, it's up to carriers and OEMs to send those fixes to their users. However, Google will likely release a patch for supported Nexus devices soon, and Android M should come with the bug patched by default (or even with an overhauled media library).
Zimperium hasn't mentioned it, but disabling the automatic retrieval of MMS messages in all messaging applications that support it (which includes Hangouts and IMs) could protect users against this type of exploit. It's not clear whether that would completely work, because the researchers said they found half a dozen vulnerabilities in the Stagefright library. The company will reveal more about them at the Black Hat and DEFCON hacking conferences on August 5 and 7, respectively.
Otherwise, the company said that short of an Android upgrade, its own zIPS application for enterprise customers can also protect against the Stagefright vulnerability.
Follow us @tomshardware, on Facebook and on Google+.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
dstarr3 Any reason a mobile carrier couldn't just intercept text messages containing the necessary code?Reply -
InvalidError Reply
What motivation would they have to go through the extra hassle and expense?16338411 said:Any reason a mobile carrier couldn't just intercept text messages containing the necessary code?
You are afraid to get hacked on your no longer supported phone? The carrier offers you to upgrade to a new phone for a fee. You do not upgrade your phone, get hacked and get screwed by bandwidth, LD and other charges? The carrier most likely won't let you get away from it without spending some cash either way.
The carrier patches their servers to intercept malicious SMS? They have to eat the cost of those server tweaks, they lose one reason to nudge customers to upgrade their phones regularly and they may expose themselves to additional privacy inquiries about their SMS interception. Lose-lose-lose for them. -
JOSHSKORN ReplyAny reason a mobile carrier couldn't just intercept text messages containing the necessary code?
Privacy concerns? Would you want your carrier intercepting your texts at any given time? Just a thought. -
targetdrone I think the Note II will be my last android device. This is getting ridiculous. Not that there are security flaws in Android, every computer system has them. It's the fact it's impossible to fix them without buying a new device because an affect device is no longer supported for OS updates. Oh yeah maybe I could install a a custom rom(assuming the boot loader isn't locked) but if something goes wrong I'll end up with a $500 brick. No thank you. I think I'll go super retro and get a car phone once my Note II dies.Reply -
razor512 Another reason to avoid android devices which go out of their way to make it difficult to root and install custom ROMs. With the major companies dropping support for older devices after about 18 months, there are millions of devices that will simply never receive an official update to fix this security issue.Reply
Those with easy access to 3rd party ROMs (easy is the key, larger user base = more attention from devs and faster updates), will get the security fix sooner. I bet within a few hours to a few days, you will see 3rd party ROMs with the DRM disabled until updated code for those libraries are released. -
kenjitamura ReplyAnother reason to avoid android devices which go out of their way to make it difficult to root and install custom ROMs. With the major companies dropping support for older devices after about 18 months, there are millions of devices that will simply never receive an official update to fix this security issue.
Those with easy access to 3rd party ROMs (easy is the key, larger user base = more attention from devs and faster updates), will get the security fix sooner. I bet within a few hours to a few days, you will see 3rd party ROMs with the DRM disabled until updated code for those libraries are released.
The only android devices that are difficult to install a custom ROM on are the ones manufactured in China because they don't make the source available to developers. Just don't buy Android devices with Rockchip, Allwinner, Mediatek, or Amlogic hardware and you'll be good.
-
alextheblue ReplyPrivacy concerns? Would you want your carrier intercepting your texts at any given time? Just a thought.
They already do that and store them for the NSA to peruse later - and that's not even a tinfoil hat statement. They're compelled by law to store and share with the NSA and likely other agencies.
-
dstarr3 ReplyPrivacy concerns? Would you want your carrier intercepting your texts at any given time? Just a thought.
They already do that and store them for the NSA to peruse later - and that's not even a tinfoil hat statement. They're compelled by law to store and share with the NSA and likely other agencies.
Indeed. There is no privacy with SMS in the first place. So, them intercepting malicious code would just be a good use of systems already in place. But yeah, I understand why it'll never happen.
Though, secondarily, I wonder how effective these attacks are for people that use encrypting messaging apps. -
mrmez Hardly surprising. The result of highly fragmented hardware and software.Reply
Much easier to conquer an already divided platform.
A massive advantage for IOS/OSX.
88% of apple users are running iOS 8.x
Meanwhile 50% of android users are running Jellybean or older.