WinRAR exploit reportedly remains widely-used by China and Russia state actors despite patch — vulnerability allows malicious archives to deliver a hidden payload to Windows Startup folder
It's time to update the trial copy of WinRAR on your PC.
A WinRAR exploit that has been discovered and patched in July 2025 remains widely used by threat actors — many of them government-backed — where a malicious archive delivers its hidden payload to a critical directory like the Windows Startup folder. According to the Google Threat Intelligence Group (GTIG), attackers take advantage of the CVE-2025-8088 critical vulnerability, which has since been addressed with the latest release of WinRAR, version 7.13. However, it seems that users are slow to update their software, as GTIG says that it is still a popular vector used by attackers linked to both China and Russia.
CVE-2025-8088 describes a path traversal vulnerability in earlier versions of WinRAR, in which malicious actors create archives that have a hidden payload. When the victim opens it, the payload is then surreptitiously delivered to a critical path. The Windows Startup folder is often one of the default destinations, ensuring that the delivered malware is executed the next time the user opens or restarts their computer.
Despite the ubiquity of fast internet and cloud storage, archiving apps like WinRAR, WinZip, and 7-Zip remain popular among some users. That’s because they allow you to package multiple files and folders into one clean file and allow for encryption and password protection. Aside from that, they also compress the file size, reducing the amount of data needed to download them and helping save on data costs.
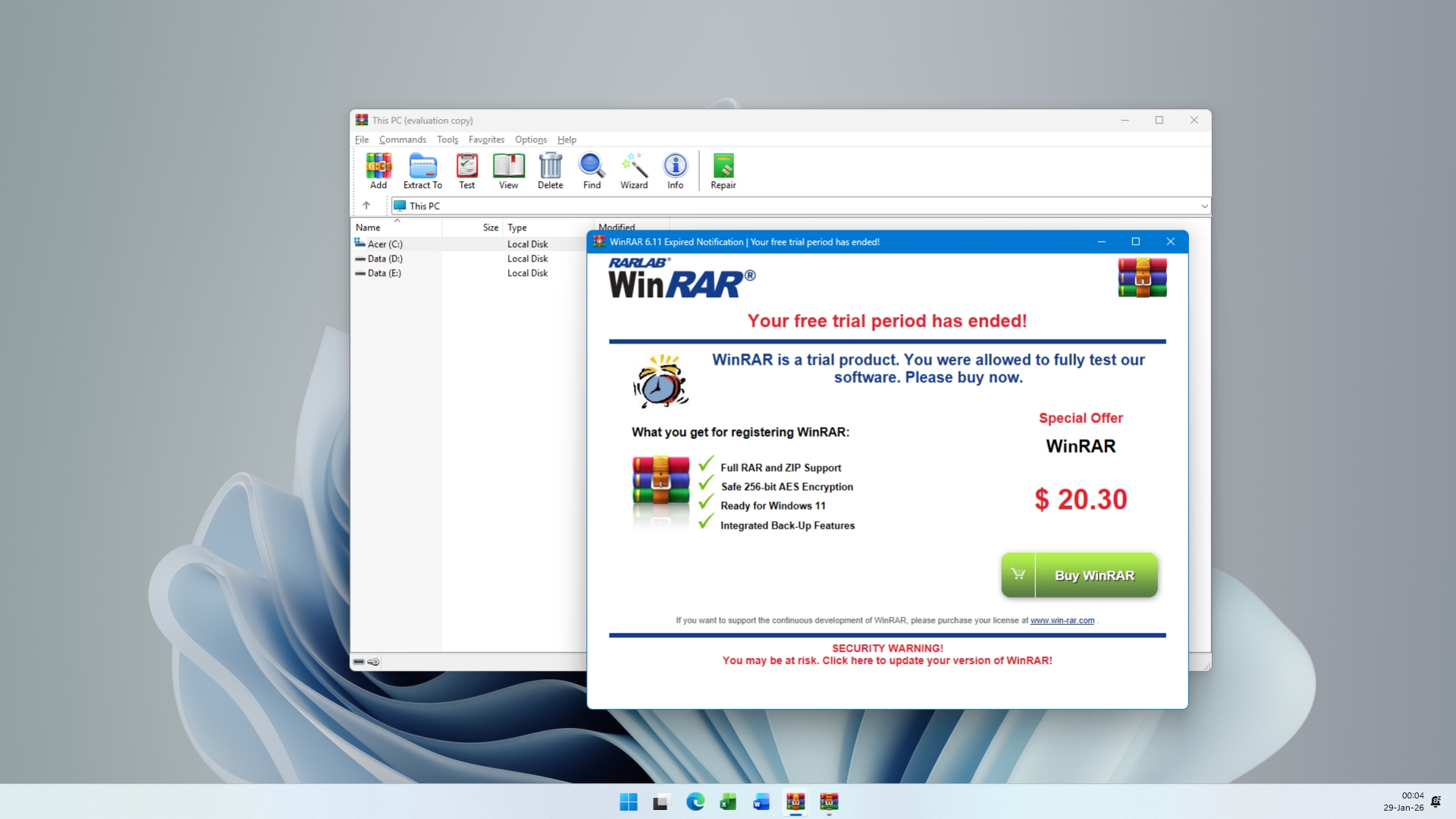
More importantly, this particular archiving app is quite popular because of how the company enforces its license. Although WinRAR comes with a 40-day trial period, you’re supposed to pay for it once that has expired. However, most people just close that window without reading it and continue using the app normally without spending a single cent, and you can do this for life. Because of this, they might have also missed the security warning that RARLAB, the company behind WinRAR, added to the bottom of the expired trial notification window.
According to GITG, Ukrainian military units and government entities are often targeted by this exploit, mostly for espionage. However, commercial entities are also prone to this attack, with victims recorded in Indonesia, LATAM, and Brazil. So, if you have WinRAR installed on your system, it’s best that you upgrade it to the latest version to avoid becoming victimized through this attack vector.

Follow Tom's Hardware on Google News, or add us as a preferred source, to get our latest news, analysis, & reviews in your feeds.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.

Jowi Morales is a tech enthusiast with years of experience working in the industry. He’s been writing with several tech publications since 2021, where he’s been interested in tech hardware and consumer electronics.
-
Li Ken-un ReplyDespite the ubiquity of fast internet and cloud storage, archiving apps like WinRAR, WinZip, and 7-Zip remain popular among some users. That’s because they allow you to package multiple files and folders into one clean file and allow for encryption and password protection. Aside from that, they also compress the file size, reducing the amount of data needed to download them and helping save on data costs.
None of these are my primary reason for using archiving solutions. I use WinRAR because most file handling products (cloud syncing, auto-backup, etc.) couldn’t be bothered to handle file metadata with care.
Windows has a “creation date” timestamp for files, which most often gets lost. “Modification date” is usually better handled, but there are no guarantees.
Inside a WinRAR archive, that file system metadata is traveling with the file no matter what happens in transit.