Benchmark Your Spectre Vulnerabilities With Google's Exploit Page
See for yourself at Leaky.Page.
Spectre continues to go bump in the night. The vulnerability was revealed in 2018, but even though it's largely faded from public consciousness, it's still a threat. Case in point: Google has published a proof-of-concept website called Leaky.Page that shows how attackers can use JavaScript to exploit Spectre via popular web browsers.
Let's turn back the clock. Spectre was disclosed with another vulnerability, Meltdown, that vendors were quick to address despite their fixes causing slight performance drops. Responding to Spectre has proven more difficult because it requires Intel, AMD, Arm, and Nvidia to change their processor architectures.
In the meantime, it's up to other companies to limit their customers' exposure to the vulnerability, which is where this proof-of-concept comes in. Google said in a blog post that it wanted to "give web application owners a better understanding of the impact Spectre vulnerabilities can have on the security of their users' data."
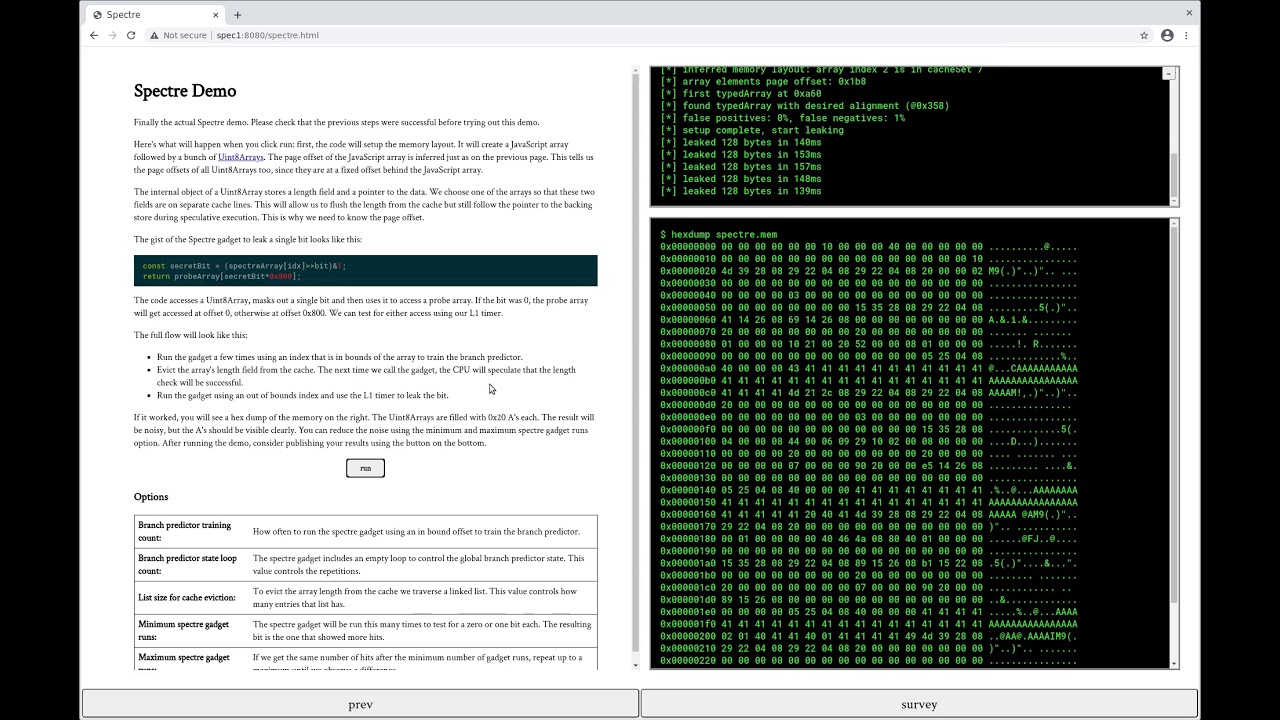
The result is Leaky.Page, which offers a summary of Google's intent before giving people the chance to see how JavaScript-based Spectre exploits could affect their systems. Google published a video of a successful test that you can watch right here:
Leaky.Page was originally configured for Chrome 88 running on an unidentified version of Linux and an Intel Core i7-6500U. Google said that its proof-of-concept could "function across a variety of operating systems, processor architectures, and hardware generations," however, "without any major changes" to the code.
The company only named one additional processor susceptible to this exploit: the M1 chip Apple introduced in November 2020. That doesn't come as a surprise—we already knew that Arm's designs were affected by Spectre—but it's a worthwhile reminder that Apple silicon can be affected by three-year-old vulnerabilities.
Google said its tests on Chrome 88, Linux, and an Intel Skylake processor leaked data at speeds up to 1kB/s. Results will vary based on the system tested, however, which is why Leaky.Page could prove useful. A list of recommendations to web developers looking to protect their users can be found in Google's blog post.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Even they aren't enough. Google noted that "while all of the mechanisms described in this article are important and powerful security primitives, they don't guarantee complete protection against Spectre; they require a considered deployment approach which takes behaviors specific to the given application into account."

Nathaniel Mott is a freelance news and features writer for Tom's Hardware US, covering breaking news, security, and the silliest aspects of the tech industry.
-
mitch074 Using Firefox on Linux on a Zen2 chip, the exploit was 100% thwarted. Using Chromium (same setup otherwise), only the memory dump failed.Reply
Stay safe, don't use Chrome/Chromium/Edge/etc.