Pegasus 'Lawful Intercept' Spyware For iOS Used To Target Activists, Journalists
Citizen Lab (Munk School of Global Affairs, University of Toronto) and Lookout have uncovered three critical vulnerabilities in Apple’s iOS software that have been used to target human rights activists and journalists, including those from the New York Times.
Hacking Activists And Journalists
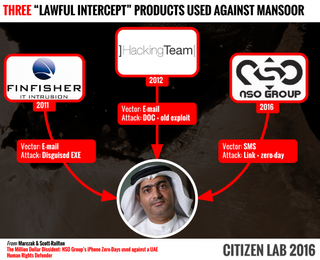
Ahmed Mansoor is an internationally recognized human rights activist and a “Martin Ennals Award Laureate,” which is sometimes called the “Nobel Prize for Human Rights.” He has been targeted for the third time by what is usually called “lawful intercept” spyware, which is malware purchased by governments to supposedly help them catch the “bad guys.”
Mansoor was first targeted with the tools of two infamous hacking groups that tend to sell their spyware to governments around the world, such as Gamma International (in 2011), and Hacking Team (in 2012).
More recently, Mansoor was targeted with spyware from the NSO group. This company has so far tried to stay under the radar, but it is otherwise well known to governments looking to purchase surveillance tools.
Mansoor received one strange text one day, from a number he didn’t know, which contained a link and the words “New secrets about torture of Emiratis in state prisons." Being a previous target of similar attacks, he sent the text and link to Citizen Lab and Lookout for analysis.
Upon reviewing the malware, Ronald Deibert, Citizen Lab Director, said:
“That a country would expend millions of dollars, and contract with one of the world’s most sophisticated cyber warfare units, to get inside the device of a single human rights defender is a shocking illustration of the serious nature of the problems affecting civil society in cyberspace," exclaimed Ronald Deibert, the Director of Citizen Lab.“This report should serve as a wake-up call that the silent epidemic of targeted digital attacks against civil society is a very real and escalating crisis of democracy and human rights,” he warned.
Stay on the Cutting Edge
Join the experts who read Tom's Hardware for the inside track on enthusiast PC tech news — and have for over 25 years. We'll send breaking news and in-depth reviews of CPUs, GPUs, AI, maker hardware and more straight to your inbox.
Citizen Lab found that NSO’s exploit infrastructure was also previously used against a Mexican journalist. The New York Times was recently hacked, and the attacker seemingly used NSO's spyware tools, as well:
“Investigators discovered that a company called the NSO Group, an Israeli outfit that sells software that invisibly tracks a target’s mobile phone, was responsible for the intrusions. The NSO Group’s software can read text messages and emails and track calls and contacts. It can even record sounds, collect passwords and trace the whereabouts of the phone user,” wroteNicole Perlroth in the New York Times.
Pegasus And Trident
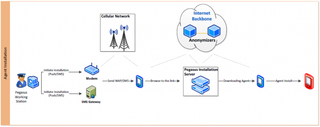
According to Lookout, the NSO’s “Pegasus” spyware, which is exclusively sold to governments as a “lawful intercept” tool, is the most sophisticated the company has ever seen deployed on an endpoint system. That’s because it can take advantage of how integrated mobile devices have become in our lives. They are always connected and have features such as voice communications, camera, email, messaging, GPS, passwords, and contact lists.
The Pegasus malware exploited three zero-day vulnerabilities in Apple’s iOS, which have been called “Trident:”
CVE-2016-4654: Memory Corruption in Webkit – A vulnerability in the Safari WebKit that allows the attacker to compromise the device when the user clicks on a link.CVE-2016-4655: Information leak in Kernel – A kernel base mapping vulnerability that leaks information to the attacker allowing him to calculate the kernel’s location in memory.CVE-2016-4656: Kernel Memory corruption leads to Jailbreak – 32 and 64 bit iOS kernel-level vulnerabilities that allow the attacker to silently jailbreak the device and install surveillance software.
Trident allows Pegasus to become, in essence, a one-click jailbreaking tool. The malware is first sent through a text message with a link. When the victim opens the link, it loads up the browser, and then it exploits the vulnerabilities in the Safari browser and the iOS kernel.
Apple has long refused to allow other JavaScript engines on iOS other than its own, fearing that they would allow for easier exploitation of the device. However, even Apple’s own browser doesn’t seem immune. Worse yet, at least one of the three main bugs seems to have existed in iOS since version 7.0, so NSO’s customers had quite a long window of opportunity to exploit them.
The Pegasus spyware installs silently on the device, without the victims realizing they’ve been compromised. Apple released an update today (iOS 9.3.5) that fixes the Trident flaws, but those who have been already compromised will remain vulnerable. The Pegasus spyware persists even after its exploits have been made obsolete by security patches. It can also update itself with new exploits that can take advantage of new zero-day vulnerabilities.
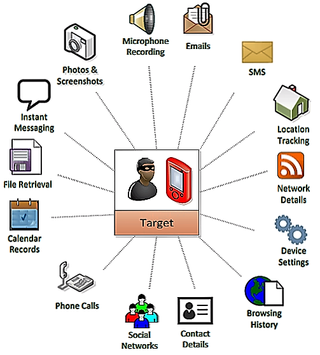
Depending on what governments or corporate customers want, Pegasus can be configured to access messages, calls, emails, and logs from apps such as Gmail, Facebook, Skype, WhatsApp, Viber, FaceTime, Calendar, Line, Mail.Ru, WeChat, SS, Tango and others.
All iOS users are recommended to upgrade immediately to version 9.3.5 by going to Settings -> General -> Software Update on their devices.
-
Achoo22 That's just the tip of the iceberg, though. Our own citizenry is being targeted every day. Try to buy a wireless security camera setup that can't be hacked and then look to our government that is, instead of passing stronger security and privacy legislation, manifestly waging war against closed systems and cryptography. It's a mess.Reply -
memadmax WHATEVER DUDE!Reply
I get emails EVERY DAY about someone whom has a million dollars somewhere that they inherited from their brothers sisters cousins second wife, and ALL THEY NEED for me to get a piece of the pie is bank account info/money order/etc etc etc...
This monsour guy is just looking for more 15 minutes of fame... There is NOTHING new about what he has received... And he should just stop being a cry baby... -
Kimonajane You want your conversation private you need to go old school and meet face to face but then need to be careful where you talk, cameras can capture you and the fascist FED hacks can lip read too.Reply -
lonewarder Please stay out of politics, Tom's. You guys have been, for over a decade, one of the few places one can go to escape the 'mainstream media' and read excellently written, unbiased articles.Reply -
bit_user Reply
How is this biased or political, exactly?18507223 said:Please stay out of politics, Tom's.
It's factual reporting about real security flaws and real exploits of them which put users of those products at risk. This is important tech journalism, and I support it.
-
Kimonajane Reply18507223 said:Please stay out of politics, Tom's. You guys have been, for over a decade, one of the few places one can go to escape the 'mainstream media' and read excellently written, unbiased articles.
No I'll say what I see happening by a fascist Federal big government when i Feel like it. Noobs like you just want to roll over and let them own you, FOOL.
-
srmojuze I highly commend Tom's for reporting on such key (pun unintended) information.Reply
Isn't it amazing how our governments are spending so much of ~our~ resources to compromise, infect, backdoor and damage our devices in the name of "protecting" us?
In regards to iOS: Interesting to learn how they jailbreaked iOS. Bet it whet the appetite of the waning iOS jailbreak community. In any case using Cyanogen Mod or dissecting Android ROMs and the popularity of Android in general is leaving iOS further behind. A closed ecosystem with zero access to source code (unlike Android, BTW yes, Google's no angel, I know)... Anyway, a closed ecosystem with zero access to source code, nice time to say bye bye to Apple.
As for Windows... darn it you can play nice games on it still!!! -
psiboy Good article! It's always nice to know just how vulnerable we are to our own shitty western governments! They should invest more in stopping guns and drugs.. seriously! Another article proving what I say every day! "If it's a connected device it's vulnerable, regardless of platform!"Reply -
bit_user Reply
So, what's with all this anti-US sentiment? Unless I missed something, the article describes bugs in Apple's products being exploited by private companies, who are selling their spy-ware to other governments.18514442 said:Isn't it amazing how our governments are spending so much of ~our~ resources to compromise, infect, backdoor and damage our devices in the name of "protecting" us?
At this point it time it can be clearly stated that the US Government is one of the biggest hacking operations on the planet. But that's old news by now, I guess.
I don't mean to defend the NSA, or anything - just try to comment on the actual article, at least. -
srmojuze Reply18518065 said:
So, what's with all this anti-US sentiment? Unless I missed something, the article describes bugs in Apple's products being exploited by private companies, who are selling their spy-ware to other governments.18514442 said:Isn't it amazing how our governments are spending so much of ~our~ resources to compromise, infect, backdoor and damage our devices in the name of "protecting" us?
At this point it time it can be clearly stated that the US Government is one of the biggest hacking operations on the planet. But that's old news by now, I guess.
I don't mean to defend the NSA, or anything - just try to comment on the actual article, at least.
Apologies, I jumped the gun in targeting the US specifically. In regards to the article:
"Mansoor was first targeted with the tools of two infamous hacking groups that tend to sell their spyware to governments around the world, such as Gamma International (in 2011), and Hacking Team (in 2012)."
So I would say, the US is most likely involved (due to various revelations recently eg. Snowden revelations, admissions by government agencies on record, fake cell towers used to illegally intercept user data, demand for more backdoors, iOS encryption battle, etc).
Of course the US is not the only government or group engaged is such illegal and nefarious activities. Five Eyes etc and Russia and China implicates a global hacking obsession.
What is concerning in regards to this article is how governments around the world are now clearly deeply in bed with blackhat hacking groups which such governments are supposed to be fighting against.
It also highlights the sheer irony of those in "authority" because blackhat hacking groups also are themselves or also in cahoots with terrorist organisations, again, which governments around the world are supposed to be battling.
In any case, cheers, I have edited my previous post accordingly.
Most Popular




