SMS Phishing Campaign Targets Brazilian Bank Customers
Renato Marinho, the Director of Research of a Brazilian security company called Morphus, identified a new phishing campaign in Brazil that targets bank customers via SMS messages.
Some bank customers in Brazil started getting SMS messages asking them to update their registration details through the given URL. Failure to do so would result in the blocking of the customers’ accounts, the message warned.
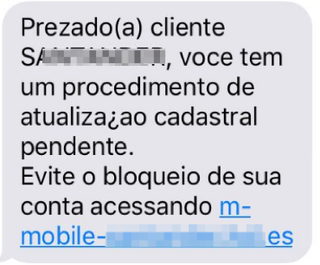
Once someone clicked on the link, a page would appear where they could enter their CPF (Brazil's equivalent to a Social Security number) and a password. To ensure that people type their information correctly, the attackers wrote rules into their code that would only accept the correct CPF format. As a side effect, this validation process also served to increase the credibility of the page and the message itself.
Afterward, the next page asked users to authorize their devices with a PIN and then upload a picture of their analog token card, which contains all the second-factor authentication codes, as seen in the image below.
Once someone finalizes the whole process, the attackers will have access to all the login details they need to start making fraudulent transactions on the bank customers’ behalf. The customers are then also forwarded to their banks’ real login pages, which may leave some of them puzzled, as they had already entered their login details on the fake web pages.

Phishing attacks are not new, and although the ultimate responsibility lies with the users to verify that the messages they received actually come from their banks, in the real world not everyone ends up doing that. This is why it’s important for banks to use systems and tools that are resilient to such attacks by design.
In this case, the bank or banks in question also seem at least partly responsible for the attacks’ effectiveness because they gave their customers hardcoded two-factor authentication codes inscripted on their analog token cards. If the banks had delivered digital token devices with codes that disappear in 30 seconds, as other, more modern banks have done, the attackers wouldn’t have been able to exploit the system so easily via phishing techniques.
Stay on the Cutting Edge
Join the experts who read Tom's Hardware for the inside track on enthusiast PC tech news — and have for over 25 years. We'll send breaking news and in-depth reviews of CPUs, GPUs, AI, maker hardware and more straight to your inbox.
-
derekullo I can't see any bank you use regularly closing your account due to not updating your "registration details".Reply
Maybe an account with a zero balance that hasn't been using in 10 years, but even then I'm sure they would at least give you a phone call / certified mail before doing so.
An easy way to avoid this would be to simply call your bank and ask if this is real.
Hopefully the banks of the affected customers put a notice on their website warning of the scam.
Assuming the site only recorded numbers and wasn't able to validate your number you probably could have just typed in any number, as long as it was in correct CPF format, 123.456.789-10
If the site accepted that it would be a red flag that it wasn't a legitimate. -
Flyingfenix The bank in question is SANTANDER (no point in hiding it!). Most brazilian users ALREADY know they should NEVER use more than a single on code from the token card. And, if the associated PIN is incorrect, the bank's systems always request the SAME code.Reply
The banks (Santander, Bradesco, Banco do Brasil and Itaú from my personal experience) all repeatedly warn users to never click links in SMSs, emails, and to always initiate transactions from the bank's website.
Unfortunately, "most users" do not equal to "all users" so there's always someone ready to fall for this scam.
About the CPF format, it is made from 9 digits, plus two checking digits, calculated from the previous ones. The formula is very simple (you could calculate them by hand if you wished to), but again, simply filling in the punctuation for a random number would not work unless by pure luck (1% chance).
About the "token card", if the user keeps it secret, and doesn't do stupid things like taking a freaking photo of the card and sending it to complete strangers, it is a surprisingly rugged, low cost and efficient solution. For customers with higher balances/incomes/investments, most banks operating in Brazil (Santander included) will "upgrade" you to a electronic token, or at least a smartphone token. For a small monthly fee, of course.
Finally, I already lost count of the times similar scam came and went. In the past, they were very easy to spot as scams because of glaring typos, grammar errors, bad imagery, etc. but lately they became much harder to spot.
Most Popular






