Spora Ransomware Spreads Via Fake 'Chrome Font Pack'
Palo Alto Networks threat intelligence analyst Brad Duncan discovered that Spora, a ransomware family that doesn’t require internet traffic to encrypt PC users’ files and doesn’t generate any traffic by connecting to its command-and-control servers, is spreading through fake “Chrome Font Pack” pop-ups.
Tricking Users Into Downloading The Spora Ransomware
Most ransomware spreads either through spam and email attachments or hacked ad networks and websites. That’s how attackers get internet users to click on something so they can download and install the ransomware.
Sometimes, if the users don’t have their browsers or operating systems up-to-date, the ransomware can also download or install automatically by taking advantage of unpatched software vulnerabilities.
Spora's creators have hacked multiple websites most likely via automated scripts that use known and unpatched server-side vulnerabilities. They use these to gain access and put their own files on those servers.
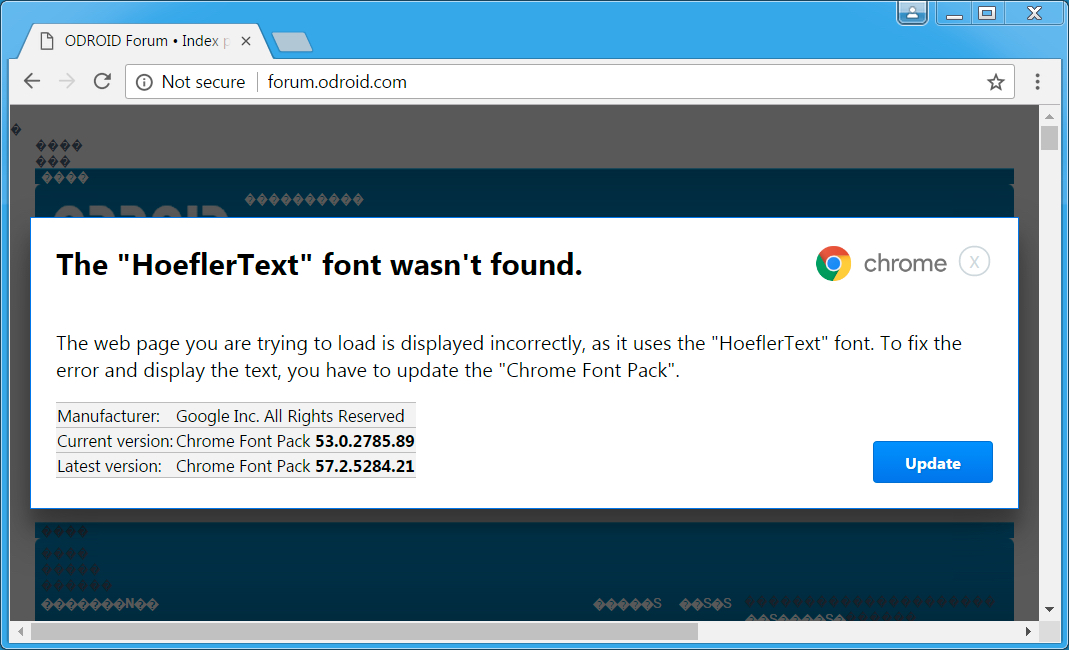
After that, they turn the websites’ pages into gibberish and tell visitors that the “HoeflerText” font is missing and that they can fix this by downloading a supposed "Chrome Font Pack."
Installing The Spora Ransomware
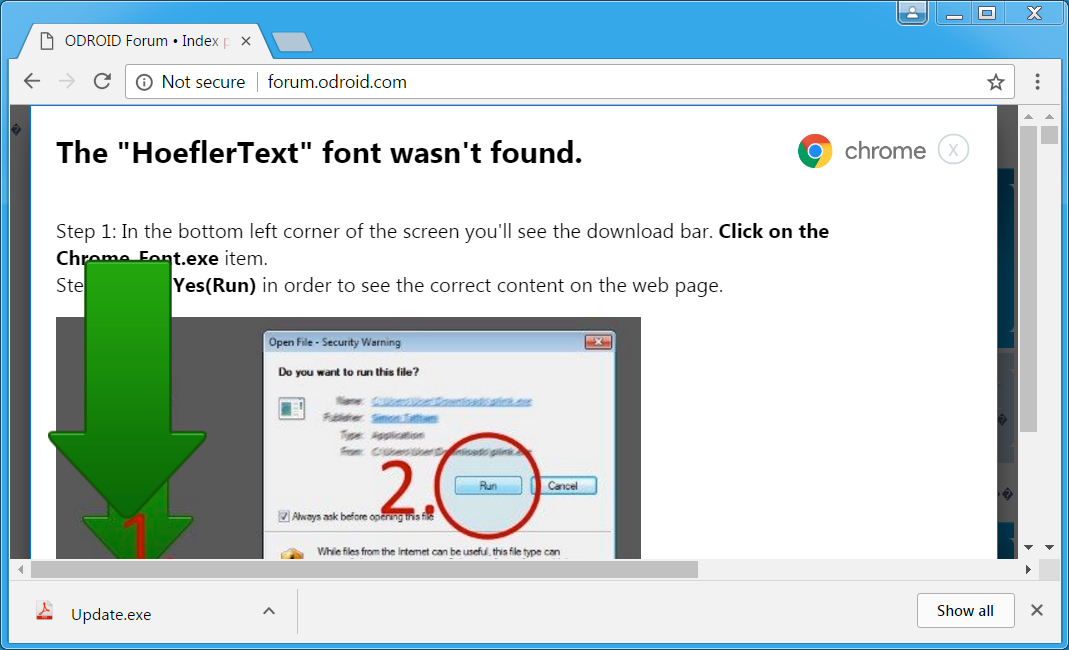
People accidentally download and install the ransomware when they click on the pop-up, thus locking their own files. The installation isn't automatic, so people still have to be tricked into installing the "update.exe" file that handles the malware's installation. However, if users download a fake Chrome font pack, chances are good that they'll also install it. Spora's creators are also being "helpful" by indicating where their victims can find the file to install.
Unlike other ransomware families, which tend to encrypt whole drives, Spora only seems to encrypt files with the following extensions:
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
.xls, .doc, .xlsx, .docx, .rtf, .odt, .pdf, .psd, .dwg, .cdr, .cd, .mdb, .1cd, .dbf, .sqlite, .accdb, .jpg, .jpeg, .tiff, .zip, .rar, .7z, .backup
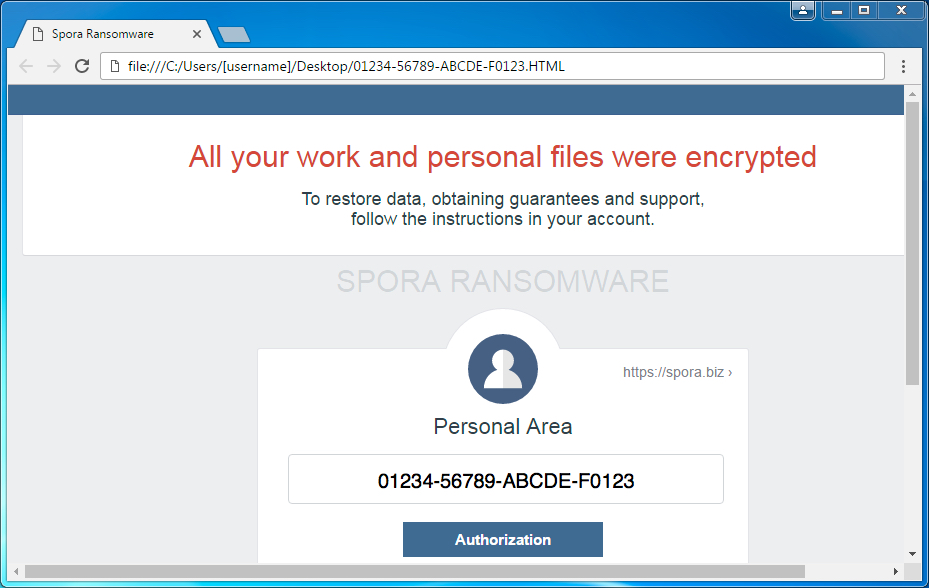
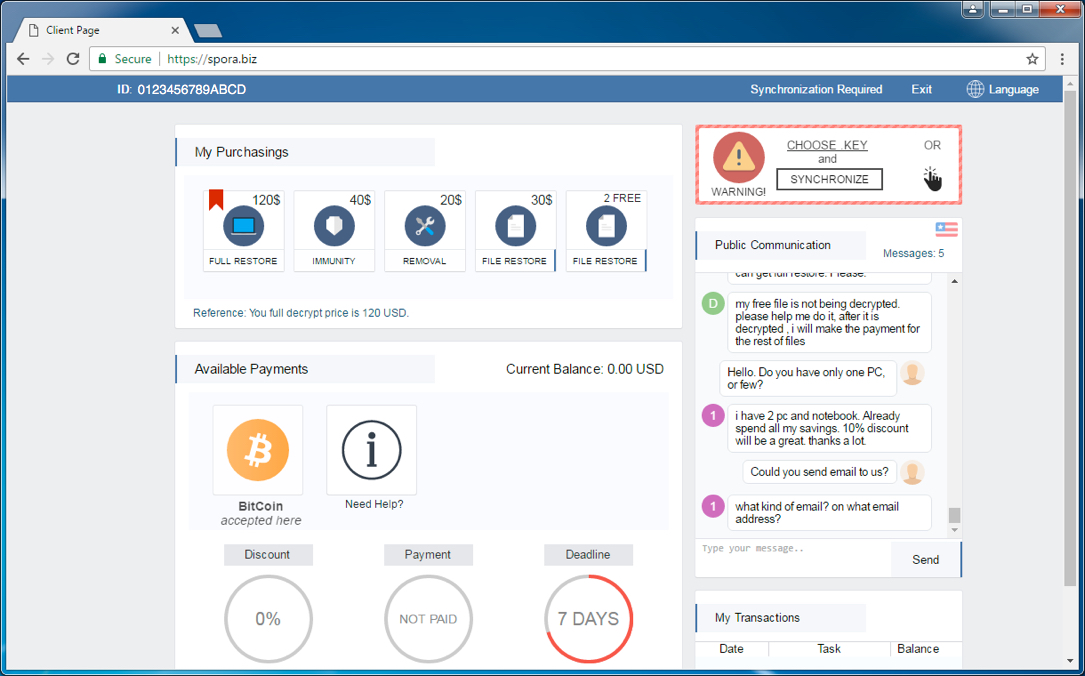
Afterwards, the PC users are prompted with a note that lets them know their files were encrypted and that they need to login to the Spora website to determine how much ransom needs to be paid.
As usual, people shouldn’t click on any pop-up they see on the web that suggests they install something. Even if the issue the pop-up warns about was real--like for instance, a missing Flash plugin--it's better to do your own research and install the necessary files from their source than from the pop-up.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
Harshil20 Ransomware is taking the world by a storm! With too many ways to get the malware's into users system, this Chrome version Ransomware is really going to be a difficult one! I had previously reported about http://ransomwares.net/netflix-ransomware-login-generator/ Netflix Ransomware where the users are given free access to Netflix (Fake access) to do the trick and install the malware!Reply -
xof1986 I had this pop up while browsing the ODROID forums.Reply
Every thread would prompt me with the error. I looked a bit in to it but ultimately opted to download the file. Once I saw the file name I decided not to run it.
I ended up disabling my ad-blocker and refreshed the page. No more pop up after that. In the end I re-enabled the ad-blocker but was no longer harassed about the font pack.
¯\_(?)_/¯ -
Rostox Try a previous version feature.Reply
https://www.virus-entferner.de/2017/01/15/spora-ransomware-virus-entfernen/ The Windows OS provides a built-in option of recovering previous versions of files. It can also be applied to folders. Just right-click on a file or folder, select Properties and hit the tab named Previous Versions. Within the versions area, you will see the list of backed up copies of the file / folder, with the respective time and date indication. Select the latest entry and click Copy if you wish to restore the object to a new location that you can specify. If you click the Restore button, the item will be restored to its original location.