Windows Pre-Boot Malware Puts Financial Industry At Risk
Security researchers from FireEye discovered Windows pre-boot malware (or bootkit) on the machines of a customer from the financial transactions market. FireEye believes the malware belongs to a financial crime group from Russia, called FIN1.
“We identified the presence of a financially motivated threat group that we track as FIN1, whose activity at the organisation dated back several years,” FireEye reported. ”The threat group deployed numerous malicious files and utilities, all of which were part of a malware ecosystem referred to as ‘Nemesis’ by the malware developer(s).”
A “bootkit” can infect lower-level system components, which makes identifying it quite difficult. It’s also highly persistent and will not be removed by re-installing the Windows operating system. The malware supports a wide array of backdoors and capabilities, which include file transfer, screen capture, keystroke logging, process injection, process manipulation, and task scheduling support.
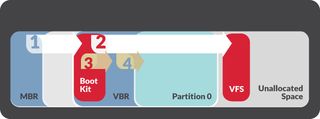
Once a target computer is infected with the Nemesis malware, it can be further updated to include more hacking tools and functionality. In early 2015, the FIN1 group updated Nemesis to include a utility that modifies the Volume Boot Record (VBR) and hijacks the system boot process to begin loading malware components before Windows system code. FireEye called this utility BOOTRASH.
BOOTRASH hijacks the boot system through a multi-step process, in which it creates a virtual file system in the unallocated drive space between partitions. It then hijacks the original VBR code with its own infected code. The malicious code then injects 32- or 64-bit versions of the Nemesis components into the Windows kernel.
The BOOTRASH installer will work with any drive that has a Master Boot Record (MBR) boot partition, but it will not work with the GUID Partition Table (GPT) disk architecture. It’s also unlikely that it will work with Windows machines that use Secure Boot, which is meant to protect against this type of bootkit and uses GPT as a requirement, as well.
Interestingly enough, the malware also needs the .NET 3.5 or later framework to work; otherwise, it will quit working. This seems like a considerable weakness in the portability of the malware. However, most Windows machines, especially from enterprise customers, should also have the .NET framework installed for use with other applications.
Stay on the Cutting Edge
Join the experts who read Tom's Hardware for the inside track on enthusiast PC tech news — and have for over 25 years. We'll send breaking news and in-depth reviews of CPUs, GPUs, AI, maker hardware and more straight to your inbox.
According to FireEye, bootkits aren’t that common, but there have been reports of such malware in the past. The bootkits have usually targeted the financial industry, but other industries have been affected as well. Their pre-boot persistence in enterprise computers makes them appealing to attackers. They also seem to be used when other techniques don’t work so well or when the targeted data is of high value.
FireEye suggested that re-installing the operating system is no longer a sufficient method of getting rid of certain types of malware. The solution against this type of threat is to use tools that can access and search raw disks at scale for evidence of bootkits, or the disks should be physically wiped before installing the operating system.
______________________________________________________________________

Lucian Armasu joined Tom’s Hardware in early 2014. He writes news stories on mobile, chipsets, security, privacy, and anything else that might be of interest to him from the technology world. Outside of Tom’s Hardware, he dreams of becoming an entrepreneur.
You can follow him at @lucian_armasu. Follow us on Facebook, Google+, RSS, Twitter and YouTube.
-
10tacle "FireEye suggested that re-installing the operating system is no longer a sufficient method of getting rid of certain types of malware. The solution against this type of threat is to use tools that can access and search raw disks at scale for evidence of bootkits, or the disks should be physically wiped before installing the operating system."Reply
Who would ever just reinstall the OS thinking that would take care of any virus, especially one buried deep in the MBR? Paying money for a good anti-virus and anti-malware program is worth it for we users who care about our personal data protection.
Of course, the corporate bean counters do not see the budget of their IT departments as high priority. Used to drive me nuts when I worked in one. Talk about having a hand tied behind your back when employees would constantly complain about slow computers and whatnot. -
Alec Mowat ReplyWho would ever just reinstall the OS thinking that would take care of any virus, especially one buried deep in the MBR? Paying money for a good anti-virus and anti-malware program is worth it for we users who care about our personal data protection.
Most people.
Most people won't even update their Windows from 7 to 10 because they're afraid it's not compatible with ancient software programs. -
kenjitamura I thought it was common sense for people to use DBAN or Killdisk between OS installs. I do it even when re-installing the same OS.Reply -
DrakeFS ReplyMost people.
Most people won't even update their Windows from 7 to 10 because they're afraid it's not compatible with ancient software programs.
This is more about enterprise PCs and not personal PCs. I could care less if family member, friend, random stranger, etc.. got this virus. However, I would like to know what finical company does not have a wipe apart of the image process... that way I know what finical company to avoid. -
mrjhh I doubt that the GPT limitation will last long. Secure boot isn't a panacea, the firmware can also be replaced with interesting code in the ACPI code running at the highest trust level, whether it's UEFI or BIOS. While UEFI is required for secure boot, there isn't much to prevent bad firmware from being installed with just Secure boot. A TPM can provide more security, but almost nothing has a TPM installed. But even that requires external verification of TPM signatures, and that external verification becomes the next weak link in the chain. But, a TPM doesn't prevent installation of buggy firmware or OS, it only verifies that the expected firmware/OS is installed. When new firmware/OS is approved and installed, the old signatures have to be removed to prevent the old/buggy firmware/OS from being allowed.Reply -
warezme ReplyMost people.
Most people won't even update their Windows from 7 to 10 because they're afraid it's not compatible with ancient software programs.
That's where you would be mistaken. Up until a week or so ago Enterprise version of Symantec antivirus suite was not compatible with Windows 10. Some specialty educational very necessary programs like Examsoft took a long time to become compatible, causing students who updated right away or buy a new laptop to have to blue-book early exams. These are all examples of current software and I'm sure there are many such examples in the corporate world.
Sure if all people do is internet and facebook then sure Windows 10 is no problem.
-
jimmysmitty Reply17084885 said:"FireEye suggested that re-installing the operating system is no longer a sufficient method of getting rid of certain types of malware. The solution against this type of threat is to use tools that can access and search raw disks at scale for evidence of bootkits, or the disks should be physically wiped before installing the operating system."
Who would ever just reinstall the OS thinking that would take care of any virus, especially one buried deep in the MBR? Paying money for a good anti-virus and anti-malware program is worth it for we users who care about our personal data protection.
Of course, the corporate bean counters do not see the budget of their IT departments as high priority. Used to drive me nuts when I worked in one. Talk about having a hand tied behind your back when employees would constantly complain about slow computers and whatnot.
A proper reinstall deletes the old MBR and re-partitions the HDD anyways. That is how I do my "clean" installs. Any other way is not a "clean" install.
-
corbeau ReplyI thought it was common sense for people to use DBAN or Killdisk between OS installs. I do it even when re-installing the same OS.
Not on an SSD you don't.
Most Popular


