Malicious Microsoft Word Files Use New Techniques To Evade Security Sandboxes
Zscaler security researchers uncovered new techniques that malware authors use to evade virtual machines and helps protect their code from analysis by security researchers.
The researchers noticed that a recent wave of malicious Microsoft Word documents were evading automatic analysis by using anti-virtual machine and anti-sandboxing techniques. Security researchers tend to use VMs or other types of sandboxes to protect their systems when analyzing files or malware code.
The attackers that created the malware in the first place would normally want their code to remain undetected, because then they can use it for longer periods of time and on more machines.
Malware Through Microsoft Word Macros
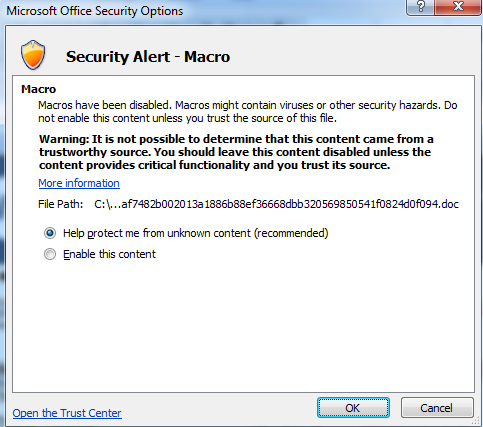
Using Word documents by taking advantage of “macro” scripting capabilities is a popular way to infect targets. Malware authors also obfuscate their code to bypass signature-based antivirus software and have implemented techniques that can evade virtual machines or other analysis tools.
These tests are written in macro scripts inside the download document. However, the user must first enable macros, as many years ago Microsoft disabled Word macros by default for obvious security reasons. Through social engineering techniques, the malware authors can get at least a portion of the users who download the file to activate macros.
Then, the script checks for standard virtual environment strings that may be present on the system. It also checks the Windows Management Instrumentation to see whether any analysis systems, virtual environments or popular analysis tools interact with it.
If any of these checks returns positive, then the macro code execution stops and the final malware payload, which was meant to infect the PC, is no longer downloaded. Otherwise, if the tests fail, then the malware will download on the computer.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Zscaler said that many types of malware families use Word documents as the initial vector for infection, including ransomware and banking and backdoor trojans.
New Anti-Sandboxing Techniques
The Zscaler researchers said that in May, they found that malware authors were using some new techniques to evade sandboxes. For instance, they use the Office “RecentFiles” property with a set value of 3 or larger, which would check to see whether the user had recently accessed three or more documents.
Typically, security researchers would use a clean operating system and Office installation, with no more than one or two Word documents opened for testing. Then, they would save a snapshot of that VM, so they can always revert back to that clean state when they test something new. Now, the malware authors try to take advantage of this typical behavior of security researchers to evade detection.
Another new evasion technique involves having the macro script check the user’s external IP address, and then comparing it to known server locations and data centers of multiple security vendors. If the user’s IP matches one of the vendor’s IP addresses, then the macro would not send the malware payload and it would terminate itself.
Although these sort of anti-sandboxing evasion techniques are becoming increasingly more popular with malware authors, it can also be used against them. For instance, HitManPro.Alert 3, an anti-exploit tool, has added exactly this kind of feature, called “Vaccination.” It gets sandbox-aware malware to self-terminate by fooling it into thinking that it’s inside a VM or that it’s being monitored for reverse engineering.
However, as usual, this will continue to be a cat and mouse game between black hats and white hats, with each trying to exploit each other’s code weaknesses. Malware authors will look for new ways to evade analysis tools, while anti-malware vendors will continue improving their products to catch them.
Lucian Armasu is a Contributing Writer for Tom's Hardware. You can follow him at @lucian_armasu.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
warezme Couldn't you use this to your advantage and run some bogus WMI analysis system to automatically disable scripted malware by their own hand.Reply -
Onus These time and money wasting games will continue until the last thing convicted malware authors hear is "Game Over," before someone ruins their day with a single large caliber round to the back of the head.Reply -
bit_user Reply
The article says HitManPro.Alert 3 does exactly this.18101746 said:Couldn't you use this to your advantage and run some bogus WMI analysis system to automatically disable scripted malware by their own hand.
I'd also tend to think that making any sort of checks for ones IP, recent file history, etc. could be used to detect suspicious malware. I think there are probably few or no legitimate docs which do those things.
After reading about the hastening decline of the PC market, I can say one thing we won't miss about PCs is malware. Sure, hackers will just focus more on the cloud, but at least that tends to be better secured than the typical home PC.
Keep dreaming. Most of these folks are operating in jurisdictions where their victims' governments can't touch them. And I'll bet a fair few are in organized crime syndicates that would protect them from any street justice people might try to carry out.18101854 said:These time and money wasting games will continue until the last thing convicted malware authors hear is "Game Over," before someone ruins their day with a single large caliber round to the back of the head.
But I do remember reading about a spammer who had been murdered, like 10 years ago...
-
Achoo22 It's further evidence that Microsoft operating systems are garbage. It should never be possible for a corrupted document to install a system backdoor.Reply -
alidan Reply18102593 said:It's further evidence that Microsoft operating systems are garbage. It should never be possible for a corrupted document to install a system backdoor.
i don't want to say garbage mainly because the only alternatives are so user unfriendly that they are not options for the vast majority or are apple which i view as worse then windows even though i hate windows 10, id rather use it then a mac. -
Kimonajane Maybe if Microsoft wasn't in bed with FED, working with the NSA on their software to put back doors in for them they would be able to make a better secure product. MS has been in bed with the Fascist FED since the XP days maybe even earlier.Reply
Before any MS fanboy says pfft it was leaked out a few years back that MS worked with the NSA on the Vista OS. -
f-14 KIMONAJANE the Fed mandated the open back doors policy since the pedophile serial rapist pot smoker days of slippery willy clinton and the digital millenium copy right act and other internet security laws passed back then it even limited dialup speed to 56k, something we can probably do away with nowdays. there were other laws passed before slippery willy clinton but the clinton era updated so much it made the obamacare bill look tiny.Reply