WinRAR Vulnerability Opens Up Users To Remote Code Execution
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
You are now subscribed
Your newsletter sign-up was successful
A vulnerability found in the latest stable version of WinRAR, a file archiving software tool, could pose a security risk for people who create and use self-extracting (SFX) executables.
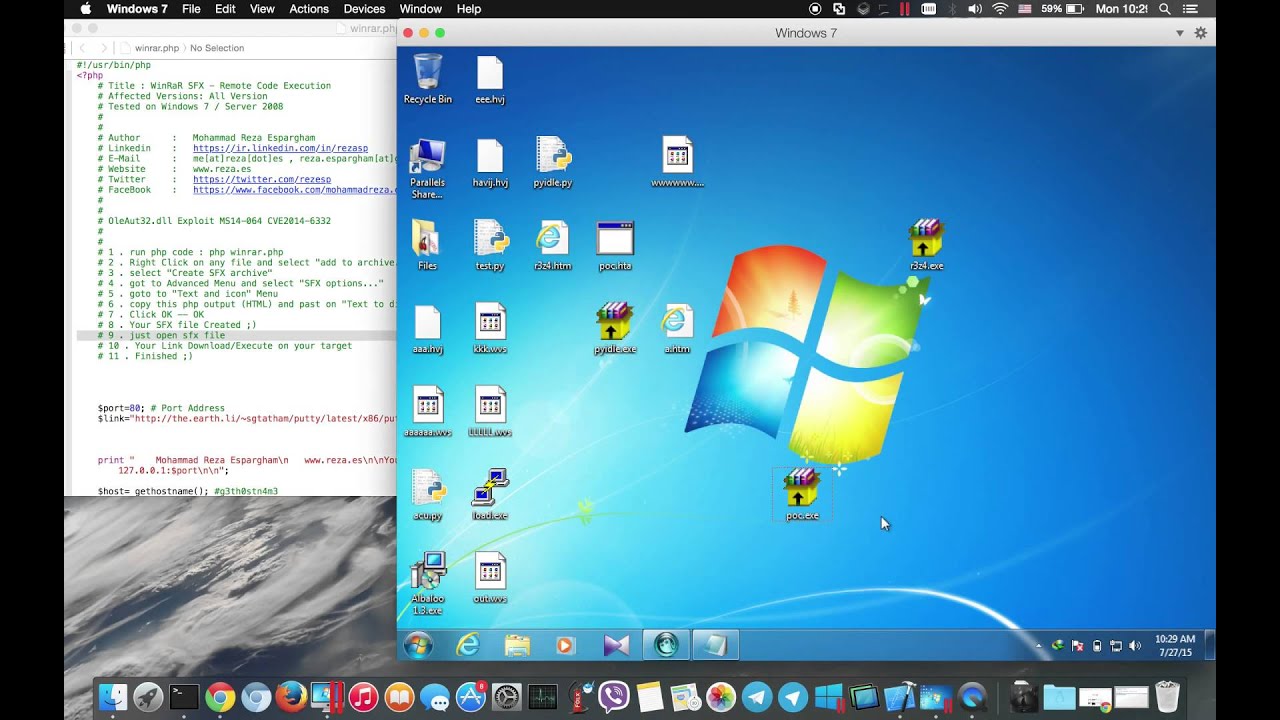
In a recent report by Vulnerability Lab, a vulnerability research company, a code execution bug was discovered in the official version of WinRAR SFX 5.21, which allows attackers to compromise a system remotely.
The attackers can inject malicious HTML code into a self-extracting executable, which then results in system takeover when the targets try to open the archived file. The vulnerability requires initial user action and it also requires for the account to be an unprivileged one (Administrator) and without any other restrictions (UAC). However, it likely wouldn't matter if UAC and a limited account were being used, because if the users intend to open the file, then they would just click to bypass those restrictions; unless of course the PC users don't know the Administrator passwords on their PCs, which could be the case in enterprise environments.
The way Windows security works (for legacy programs) is that if a user wants to open or install something, then that file would essentially get access to the whole system anyway, and it's not further restricted in a significant way besides the initial UAC/Administrator prompt. That's why after the initial opening of the file by the user, the malicious HTML code embedded into the SFX archive can download an executable from the Internet, as shown in a proof of concept by the Vulnerability Lab, and then run on the system without any other action from the user.
Users are recommended to be careful when opening self-extracting WinRAR files, especially if they're using WinRAR 5.21 to do it, and they should update to the newest version as soon as a patch is made available.
The makers of WinRAR have also responded, essentially saying that because of how Windows security and executables work, it would be just as easy to embed a malicious file within a self-extracting archive and send it to unsuspecting targets.
"User is not able to easily verify if executable part is a genuine WinRAR SFX module or some other code, so any malicious code can be included immediately to executable module of SFX archive. Malicious hacker can take any executable, prepend it to archive and distribute to users. This fact alone makes discussing vulnerabilities in SFX archives useless," according to the description in WinRAR's response.
Follow us @tomshardware, on Facebook and on Google+.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
Vistouf Well, at least you linked to WinRAR's response. But still, why didn't you report that their reply amounts to "it's not a bug, it's a feature"? Heck, they even gave MORE ways to silently run an executable from an SFX archive!Reply
Your article is disappointingly misleading. -
sergeyn Can anyone explain why is this considered a vulnerability ?Reply
If I understand correctly - a hacker creates an executable which can download and run another executable which will require admin rights when run by the end user ??? In addition a hacker needs to find such an end user who doesn't ask himself "why a does self-extracting archive file want to modify my system" and blindly presses "yes" when UAC pops ????
And all this bullshit about "the way windows security works"...
The way Windows security works (for legacy programs) is that if a user wants to open or install something, then that file would essentially get access to the whole system anyway, and it's not further restricted in a significant way besides the initial UAC/Administrator prompt
Okay - I open a lot of "something" every day, windows paint and calculator are one of them, and I don't get UAC prompt, - is my system broken ?
I also wonder why people don't complain that on linux/unix applications are not further restricted in a significant way besides the initial root access ?
(Edits: grammar) -
diddo Seems more an exe format fault (allowing to execute code where icon and text data should be, as for the vulnerability description) rather than a WinRar vulnerability, anyway it is quite worrying to know your software can be associated to an easy way to create forged exe with hidden executable instructions where data should be.Reply
7-Zip and PeaZip sfx procedure, while more spartan, seems not having this issue, I'll not be surprised if it is unique to WinRar's procedure in building the self-extraction archives. -
bloc97 The problem with this isn't the EXE, its the exe that is downloaded afterwards. You already gave permission to modify your system, so anyone who wants to bypass the Anti-Virus easily could use WinRAR. Antiviruses do not detect this vulnerability and do not warn the user of an potential virus. Either treat WinRAR as a virus or patch the vulnerability, simple.Reply