Zimperium Releases Stagefright Vulnerability Detector
Zimperium, the security company that discovered the vulnerabilities in Android's Stagefright media library, released an app on the Play Store that can check whether your phone is vulnerable to this type of exploit or not.
The researchers at Zimperium presented how the Stagefright vulnerabilities worked at the Black Hat conference. This should put more pressure on Android OEMs and carriers to send patches for their devices.
The company also announced the "Zimperium Handset Alliance," which seems to be a play on the "Open Handset Alliance" that manages the open source Android project, in order to share threat information and accelerate the patching of Android devices. The company claimed that 25 of the largest handset makers and carriers have joined the alliance.
Zimperium also worked with Samsung's Knox team to create an app that can disable MMS automatic retrieval on older devices.
Zimperium has its own app called zIPS that protects against the Stagefright vulnerabilities, but it's targeted only at enterprise customers. The company also said it's working with carriers and device vendors to come up with a protective solution for those who don't have the app installed.
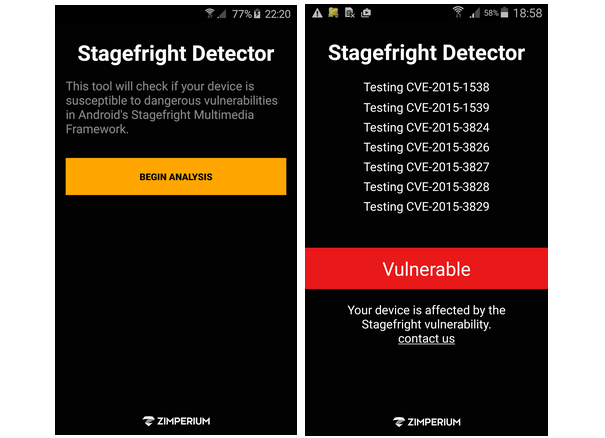
In the meantime, all users can download Zimperium's Stagefright Detector app (which only detects the vulnerability, as the name implies, but doesn't protect against it). The app can at least tell users if they're still vulnerable after they take the previously recommended measure to disable the automatic retrieval of MMS messages. Once users disable that feature, they can check again to see if they're still vulnerable and look for other installed apps in their phones that retrieve MMS messages.
Nexus handset owners as well as those who have a Galaxy S5, S6, S6 Edge or Note Edge can also check to see if they've received an OS update, which contains the Stagefright patch that should completely fix the issue.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Follow us @tomshardware, on Facebook and on Google+.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.