ProtonMail Over Tor Can Now Increase Privacy, Security, And Censorship Resilience
ProtonMail, one of the more popular end-to-end encrypted email services to appear post-Snowden revelations, launched its own .onion address (protonirockerxow.onion) that can resist distributed denial of service (DDoS) attacks from governments or malicious hackers. The company said it expects some governments to start censoring its main web address this year.
ProtonMail's End-to-End Encryption
The service was started by former CERN scientists who wanted to make end-to-end encryption for emails easier than using regular PGP. ProtonMail accomplishes this by handling its users' public keys on its servers, which means people don't have to send each other their public keys like they would if they were just using PGP themselves, and thus removes what is perhaps the greatest obstacle preventing many people from encrypting their emails.
Tor Support
Back in 2015, the ProtonMail service experienced a DDoS attack from a group that blackmailed the team into paying $6,000 to stop the attack. Since then, the team said it's built a much more DDoS-resilient infrastructure that has stopped attacks twice as powerful. However, as we’ve seen recently, many companies may be surprised by the strength of future DDoS attacks due to the increasing popularity of insecure Internet of Things (IoT) devices.
One of the reasons ProtonMail will work over Tor is because the Tor .onion addresses can’t be easily located and are therefore more difficult to turned target with DDoS attacks. The physical location of the server that implements a “Tor hidden service” is unknown--ProtonMail implied the server it's using may not be in Switzerland, where the company is based.
Another reason to use a Tor hidden service is censorship resilience. ProtonMail could be censored not just through continuous DDoS attacks, but also through the blocking of the email service’s main web page. Countries such as Egypt--which have already tried to block the encrypted messaging app Signal--and even the United Kingdom may attempt to block access to ProtonMail to prevent their citizens from using its anti-snooping capabilities.
ProtonMail.com can normally be reached through the Tor browser as well, providing users anonymity when using the service and also allowing them to bypass country-level blocking. However, to benefit from the Tor network’s own end-to-end encryption, which also helps mitigate man-in-the-middle attacks, it’s better to use the protonirockerxow.onion address via the Tor browser.
Additional Protections
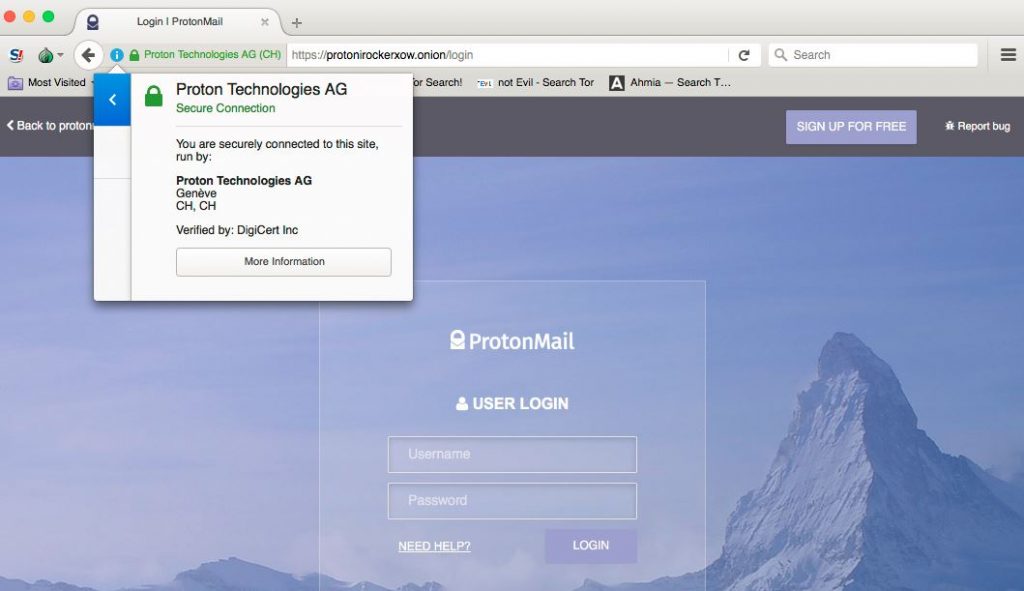
Beyond Tor’s end-to-end encryption, the protonirockerxow.onion will be served only via an HTTPS connection, further strengthening the encryption channels. This sort of implementation was done for the first time ever by Facebook with the help of the DigiCert Certificate Authority, which also issued the .onion TLS certificate for ProtonMail.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
The TLS encryption and the Extended Validation certificate obtained from DigiCert also helps against phishing attacks, because users should see the “Proton Technologies AG” name in the address bar in green, making harder (or more expensive) for an attacker to spoof it. If you want to be extra careful, you can also use the following SHA256 hash to verify the certificate for the protonirockerxow.onion address:
D6:D5:26:07:F9:5F:41:D3:92:AD:EE:59:CE:29:AB:E0:B3:E8:2F:30:EA:1E:6B:8F:9D:12:09:42:F0:35:BB:65
ProtonMail said it even chose the name of the .onion address carefully, to decrease the chance of a phishing attack. Because .onion address names are generated randomly when chosen, you have to expend significant amounts of computation to get a name that you want. ProtonMail used its spare CPU capacity to generate a more readable and more easily remembered .onion address such as protonirockerxow.onion, which could be remembered as “proton i rocker xow.”
Next Steps
ProtonMail said that in 2017, it will continue to add new security and anti-censorship features to its services, as well as provide the community with the tools to connect to ProtonMail securely even from compromised locations.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
DookieDraws Meh, I'll just stick with my Yahoo! email account for all of my super top secret, highly sensitive, emailing.Reply -
derekullo "ProtonMail used its spare CPU capacity to generate a more readable and more easily remembered .onion address such as protonirockerxow.onion, which could be remembered as “proton i rocker xow.”Reply
Proton i rocker xow does not really roll off the tongue.
Did they use spare pentium 2's cpu capacity to "think" of that name?
Maybe something like:
protonemail.onion
or
protonmail.com
Am I missing something? -
TechMivec "Because .onion address names are generated randomly when chosen, you have to expend significant amounts of computation to get a name that you want."Reply
It doesn't take any cpu cycles to think of protonmail or protonemail as a name if names weren't randomly generated. -
Tanyac Now, if only they'd provide pop/smtp access available, so we don't have to leave our email in the clouds...Reply