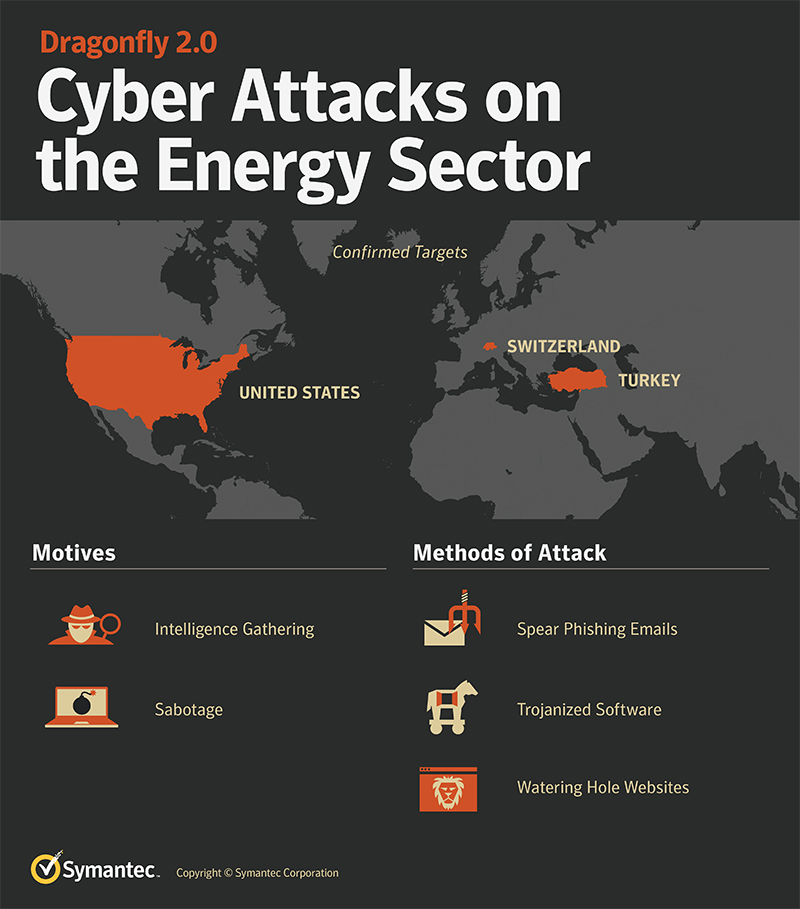
Symantec: 'Dragonfly' Attack Group Targets Energy Companies In US, Turkey, Switzerland
Symantec revealed that a group called Dragonfly has been targeting energy companies in the U.S., Turkey, and Switzerland since late 2015. So far the group has focused on gathering information, but the company warned that this could be a precursor to attacks on these countries' power grids. (Unless, of course, the energy companies use its security products, of course.) Attacks like that could result in serious physical and financial harm.
This isn't the first time Dragonfly's targeted energy companies; the group ran a similar campaign from 2011 to 2014. Symantec said in a blog post that the first campaign appears to "have been a more exploratory phase where the attackers were simply trying to gain access to the networks of targeted organizations." This new campaign, however, shows that Dragonfly "may be entering a new phase" of its attack.
Here's how Symantec attributed these recent espionage efforts to Dragonfly:
There are a number of indicators linking recent activity with earlier Dragonfly campaigns. In particular, the Heriplor and Karagany Trojans used in Dragonfly 2.0 were both also used in the earlier Dragonfly campaigns between 2011 and 2014.Trojan.Heriplor is a backdoor that appears to be exclusively used by Dragonfly, and is one of the strongest indications that the group that targeted the western energy sector between 2011 and 2014 is the same group that is behind the more recent attacks. This custom malware is not available on the black market, and has not been observed being used by any other known attack groups. It has only ever been seen being used in attacks against targets in the energy sector.
The company also said the attackers were careful to cover their tracks. Dragonfly is said to have relied on off-the-shelf malware anyone can use, to have avoided using zero-day exploits, and to have used both Russian and French in various code strings to avoid giving away the country of origin via the language used. All of these factors led Symantec to hold off on officially attributing Dragonfly's actions to a specific country.
Others haven't hesitated to call out Dragonfly's origins. The U.S. Department of Homeland Security and the FBI previously linked Dragonfly to Russian intelligence services. With that in mind, it makes sense for Symantec to notice an uptick in activity from the group in 2017. Relations between Russia and the West have grown increasingly strained recently.
Symantec has updated its products to defend against Dragonfly's snooping efforts. The company also outlined best practices for energy companies to follow, most of which are sound advice no matter how critical you are to a nation's infrastructure. Use strong, unique passwords. Learn how to identify spear-phishing campaigns. Encrypt sensitive data. These are all things you should be doing, too.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Campaigns like this are going to become more and more common. Cisco reported earlier this year, for example, that attackers were experimenting with fun new ways to spear-phish energy company employees. In Ukraine, attackers successfully caused a blackout using sophisticated malware. It's clear that energy companies are and will continue to be prime targets for ambitious hackers.

Nathaniel Mott is a freelance news and features writer for Tom's Hardware US, covering breaking news, security, and the silliest aspects of the tech industry.