Keylogger Found In HP Audio Driver
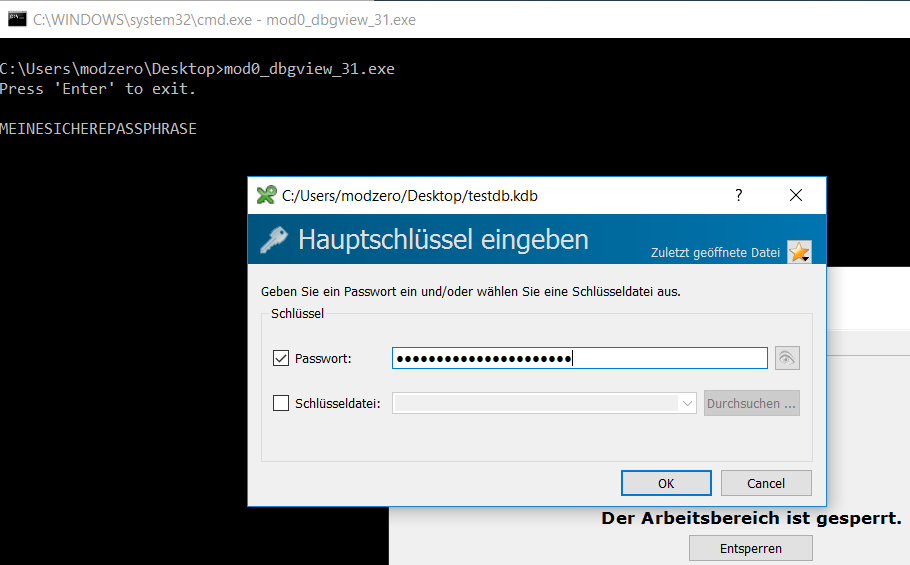
Swiss security researcher ModZero claims that it has discovered an audio driver installed on several HP laptops that contains a feature that secretly records every keystroke entered into the computer. The keylogger stores the keystrokes in an unencrypted file on the computer's hard drive.
The stored data includes sensitive personal information such as passwords and private messages. Making matters worse, anyone with access to the compromised computer would have access to the data collected by the keylogger. The audio driver, developed by Conextant, is found on dozens of HP laptops and tablets.
ModZero researchers wrote:
A keylogger is a piece of software for which the case of dual-use can rarely be claimed. This means there are very few situations where you would describe a keylogger that records all keystrokes as 'well-intended'. A keylogger records when a key is pressed, when it is released, and whether any shift or special keys have been pressed. It is also recorded if, for example, a password is entered even if it is not displayed on the screen.
The researchers went on to say that, based on the file meta-information, the keylogger has existed on HP computers since at least Christmas 2015. Making matters worse, even though the log file is overwritten each time the computer reboots, a history of all keystrokes over the last few years could also be found in system backups. ModZero advises affected HP users to delete the C:\Users\Public\MicTray.log file if it is present on the hard drive, as it can contain sensitive information such as login information and passwords.
ModZero said it was forced to go public with this information because neither HP nor Conexant have responded to their requests for comment.
Laptop Magazine, another publication in the stable of Purch Media (Tom's Hardware's parent company), dig some digging to confirm the issue.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Steven Lynch is a contributor for Tom’s Hardware, primarily covering case reviews and news.
-
SinxarKnights Not even slightly surprised. Well I take that back, I am surprised nobody caught it sooner. I wonder what prompted ModZero to even look at that or if they just happened to catch it by accident. It is weird that the driver would log every keystroke.Reply
I get it is listening for hotkey presses, but why log it? Seems like a super amateur way to listen for hotkeys. Like they couldn't figure it out so they said, oh well we should just write all the keystrokes to file then check the file for the proper combo of keystrokes because it is more secure than doing it in memory.
Or it could be as simple as they forgot to disable a hard coded debug mode before releasing it.
Genuinely curious how that slipped through as it is a major security issue that affects quite a few devices.
ed: Yeah the evidence supports the hard coded debug mode: http://www.laptopmag.com/articles/hp-keylogger-installed
the keylogging code was not supposed to be in laptops sold to the public, noting that it was mistakenly added to the drivers.
-
leoscott My wife has a laptop that has the log file created. However, I tested it and it does not appear to be logging the keys in the log file in C:\Users\Public. I wonder if HP had them fix it with a patch.Reply -
derekullo Reply19683041 said:My wife has a laptop that has the log file created. However, I tested it and it does not appear to be logging the keys in the log file in C:\Users\Public. I wonder if HP had them fix it with a patch.
That's what HP wants you to believe.
-
Mr5oh Perhaps if Tom's wasn't so busy harassing users to collect email addresses, they would know this is already old news. This has already been patched.Reply
https://yro.slashdot.org/story/17/05/12/090221/hp-issues-fix-for-keylogger-found-on-several-laptop-models
Not that the story isn't still important, but including there is a fix is equally important. -
SinxarKnights Reply19683276 said:Not that the story isn't still important, but including there is a fix is equally important.
That is true. It says that as well in the one linked in the article but not on tom's itself.
In your link the user "Megane" came to the same conclusion as I did. Debug code left in. Weird stuff because you would think a team would be writing the drivers where they can check over each others code but apparently this is not the case at Conexant. -
randomizer I wouldn't be surprised if this was a debugging feature that someone forgot to turn off.Reply -
chicofehr Is this for the manufactures driver or the repackaged HP bloatware driver? I always reinstall windows with plain copy and use drivers directly from manufacturers rather then the laptop makers if possible.Reply -
joshyboy82 Reply
Umm. Great solution. My HP has a bunch (9 and sliders) of touch controls. I know, from upgrading OS that they don't work without HP's software package. With a laptop being used as such, not a stand in for my desktop, I rarely plug in a mouse. Now, I could just use my touch pad to navigate through OS to control things like Wifi and Volume, but I prefer to just slide my finger across that lit up bar above my keyboard. I'll choose to embrace the bloatware, for it creates convenience.19684312 said:Is this for the manufactures driver or the repackaged HP bloatware driver? I always reinstall windows with plain copy and use drivers directly from manufacturers rather then the laptop makers if possible.