AMD Responds To CPU Security Flaw Report
AMD has finally issued a full response to CTS Labs’ report that Ryzen and EPYC processors contain a total of 13 security flaws. Here’s the short version of the chipmakers’ response:
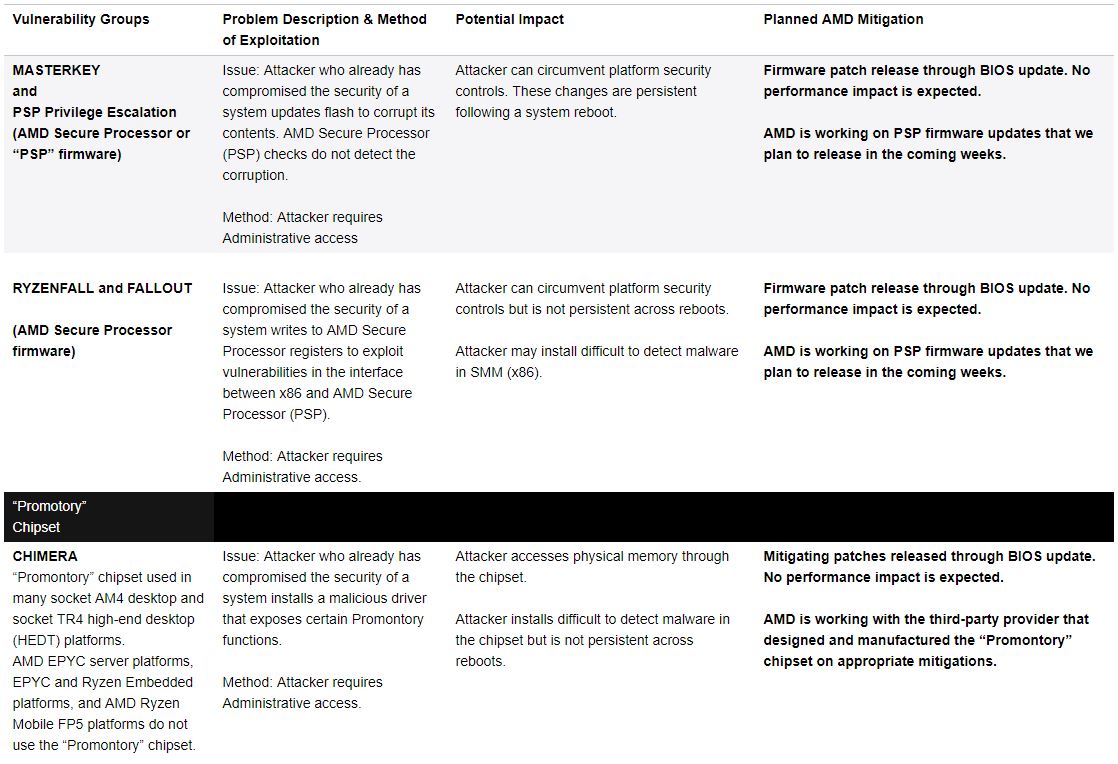
Exploitation of the vulnerabilities requires admin accessThe vulnerabilities have to do with firmware and chipsets, not the x86 architecturePatches are coming in the form of BIOS updates and firmware patches only--no microcode updates are required--via OEMs and ODMsAll issues will be addressed within “weeks,” but we strongly infer that AMD is aiming for 90 days or lessThere is no expected performance impact
The whole story was strange from the beginning. CTS Labs issued a red-alert type of report stating that AMD’s Ryzen and EPYC processors had numerous vulnerabilities, but it gave AMD just 24 hours to respond instead of the industry-norm 90 days. The firm also refused to release the full details of its findings, so only one entity--a security firm--was able to evaluate the assertions independently.
Some of the surrounding coverage that landed immediately after the report was issued made the whole thing feel like a hit piece on AMD’s stock price. Further, no one had ever heard of CTS Labs before. Subsequent interviews that CTS Labs gave the press (including Tom’s Hardware and AnandTech) seemed to cloud things even more.
Having only CTS Labs’ own whitepaper on the subject to work from, we broke down the security flaws as much as we could here.
Although we still do not have access to the actual details of the vulnerabilities, we now, at least, have AMD’s response. It’s short and to the point.
In the post, AMD’s Mark Papermaster wrote in part:
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
The security issues identified by the third-party researchers are not related to the AMD “Zen” CPU architecture or the Google Project Zero exploits made public Jan. 3, 2018. Instead, these issues are associated with the firmware managing the embedded security control processor in some of our products (AMD Secure Processor) and the chipset used in some socket AM4 and socket TR4 desktop platforms supporting AMD processors.
Papermaster also addressed the access issue--that is, in order for the vulnerabilities to be exploitable, one would need metal access. He stated:
Further, all modern operating systems and enterprise-quality hypervisors today have many effective security controls, such as Microsoft Windows Credential Guard in the Windows environment, in place to prevent unauthorized administrative access that would need to be overcome in order to affect these security issues.
CTS Labs has made it seem as though an enterprise-level threat is a real possibility, but when AnandTech pressed the issue, CTS Labs clarified:
To be honest with you, in that particular situation [running a virtual machine on a server], the vulnerabilities do not help you very much. However if a server gets compromised and the cloud provider is relying on secure virtualization to segregate customer data by encrypting memory, and someone runs an exploit on your server and breaks into the SP, they could tamper with this mechanism and this mechanism.
Note that in AMD’s response, it condensed CTS Labs’ four threat categories into three. In all three, AMD stated that admin access is required, and all the attacks would require that the system’s security has already been compromised.
Expect all patches to arrive via AMD’s ODM and OEM partners within the next 90 days.
Seth Colaner previously served as News Director at Tom's Hardware. He covered technology news, focusing on keyboards, virtual reality, and wearables.
-
redgarl 2 weeks... not 2 years like CTS-Labs was saying. We can now categorize these guys as clowns... and toms as an unreliable journalism source. At least anandtech and gamernexus did real journalism.Reply
https://www.youtube.com/watch?v=ZZ7H1WTqaeo -
clutchc So, what's the bottom line for the consumer? Update the board's BIOS when one comes available? Or will the patch come directly from AMD in the form of a download?Reply
Also, is this something older AMD processors are affected by? Phenoms, Athlons, FX? -
Druidsmark I for one am kinda glad CTS Labs did it this way as it forces AMD to react and fix the problems sooner.Reply
As my Asus computer is over to years old, I don't know if I will see an update for my M32BF A10-7800, hopefully they will update my motherboard once AMD start releasing the patches for these security vulnerabilities. -
Alerean You have nothing to worry about...someone who has your administrative privileges is going to have control of your system without these exploits anyway...Reply -
Ilya__ Reply20812420 said:You have nothing to worry about...someone who has your administrative privileges is going to have control of your system without these exploits anyway...
Exactly, if someone has your credentials you are screwed already. Open Chrome, then Cntrl+H...you are done for XD -
Gam3r01 Reply20812318 said:2 weeks... not 2 years like CTS-Labs was saying. We can now categorize these guys as clowns... and toms as an unreliable journalism source. At least anandtech and gamernexus did real journalism.
https://www.youtube.com/watch?v=ZZ7H1WTqaeo
Just to be clear, you are aware that TH and anandtech are sister sites right? -
SkyBill40 Reply20812319 said:Also, is this something older AMD processors are affected by? Phenoms, Athlons, FX?
Seeing that CTS has made no mention of the older lines and focused solely on Ryzen for what still amounts to rather sketchy targeting based on the upcoming refresh, I doubt it. While it is still a possibility, nothing is assured in any sense. While I applaud AMD for taking prompt and effective counters to the reported issues, I still feel this to be a stock shorting move and little else. It's all too convenient and stinks no matter how much they want to cover it up. -
nobspls Reply20812318 said:..... and toms as an unreliable journalism source. ....
Really skewering Tom's so quickly. What has Tom's done? Fool me once shame on you right? CTS fooled all sorts of people. Tom's is eager to report the news no doubt, and may have been quick on the trigger, but I'm pretty sure Tom's not falling for CTS shenanigans any time soon I would hope.
-
clutchc Reply20812538 said:20812319 said:Also, is this something older AMD processors are affected by? Phenoms, Athlons, FX?
Seeing that CTS has made no mention of the older lines and focused solely on Ryzen for what still amounts to rather sketchy targeting based on the upcoming refresh, I doubt it. While it is still a possibility, nothing is assured in any sense. While I applaud AMD for taking prompt and effective counters to the reported issues, I still feel this to be a stock shorting move and little else. It's all too convenient and stinks no matter how much they want to cover it up.
It does sound fishy since Intel is suffering right now with spectre and meltdown