Design Flaw May Have Allowed Attackers To Bypass LastPass Two-Factor Authentication
Triskel Security founder Martin Vigo found a vulnerability in the LastPass application that could have allowed an attacker to bypass the service’s two-factor authentication. The vulnerability seems to exist because of a bad design decision LastPass made earlier.
How Two-Factor Authentication Works
Two-factor authentication (2FA) is an additional layer of security that can protect your account when your password has already been stolen by malicious hackers.
Most internet services users tend to reuse their passwords on other websites. Therefore, when one of those websites is hacked, not only is that account compromised, but all of the user’s other accounts are exposed and vulnerable as well - unless you have 2FA enabled. However, when vulnerabilities exist that can bypass 2FA, too, and the attackers know about them, that once again puts the accounts at risk.
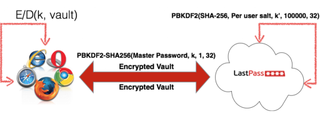
Two-factor authentication codes are generated based on several variables, including a secret seed and a timestamp. The seed is unique every time it’s generated, and the time variable creates a new seed generally every 30 seconds. In order for a 2FA code to be generated, the company’s server needs to share a secret seed with the user’s local application. This is usually done by encoding the seed in a QR code, which can then be captured by an authenticator app by scanning it.
Why LastPass’ 2FA Was At Risk
The main issue with LastPass’ 2FA system was that LastPass derived the encryption key that protects the vault from the master password (the password that protects all of your stored LastPass passwords). Considering the whole point of using 2FA is to protect against hackers who already have your password, this seems like a bad idea.
According to Vigo, this would be like wanting to use a safe in your home to securely store some items, but then using the same key for the safe that you would use for your doors. That would beat the point of using a safe, as a burglar that has your key can unlock both your doors and your safe.
Having the URL where LastPass stores the secret seed is not quite enough to exploit this vulnerability in LastPass’ 2FA process. The attackers would also need to get the user to request the QR code, too. This can be done by attacking one of the popular websites that the victim visits via a Cross-Site Request Forgery (CSRF) vulnerability.
Stay on the Cutting Edge
Join the experts who read Tom's Hardware for the inside track on enthusiast PC tech news — and have for over 25 years. We'll send breaking news and in-depth reviews of CPUs, GPUs, AI, maker hardware and more straight to your inbox.
Not all websites are vulnerable to CSRF, but it’s a common vulnerability. The attackers could also create their own websites that could obtain the QR code request from the victims by sending them a link in email or on social media.
Vigo also noticed other flaws in LastPass’ 2FA process, which he said can also be used to disable 2FA protection:
Regenerating the seed does not ask you to verify the setup by asking for a temp codeRegenerating the seed does automatically disable 2FA (instead of leaving it enabled but with the new seed)The request to regenerate the seed is vulnerable to CSRF
LastPass Fixes
Vigo disclosed the vulnerabilities to LastPass in February, so some of the vulnerabilities, such as disabling 2FA via CSRF, have been fixed, but the company is still looking for all requests that are vulnerable to CSRF.
As for the first vulnerability we discussed, which is actually a design vulnerability in the LastPass application, the company pushed an initial fix. The fix makes it so the QR codes can only be requested from LastPass.com. However, Vigo said that although this is a good intermediate fix, it doesn’t work on older browsers that don’t support the Origin header, which is what would ensure the request can only be made from LastPass.com.
LastPass also stopped deriving the secret seed from the master password, and will instead derive it from the User ID (UID). The company will store a hash of the value in its server’s database, so it can enforce an expiry and make it harder for potential attackers to pinpoint a victim’s UID.
LastPass’ Recent Security Issues
Multiple vulnerabilities have been found in LastPass’ password manager over the past year or so. It’s still unclear whether this is all because of bad design and coding practices, or mainly because it’s a popular password manager and more security experts have taken a look at it compared to competitors’ apps.
However, this latest vulnerability seems to exist because LastPass decided on a 2FA process that may have been easier to implement, but ultimately didn’t prove to be that secure. Perhaps the recently found vulnerabilities will push the company to do a more thorough review of its application’s architecture to ensure a more solid security foundation for the password manager.
-
randomizer The CSRF issue has been fixed and the QR code vulnerability is not exploitable. The researcher made a flawed POC that loads the QR code from his local machine. The source article has an update about this right at the bottom.Reply -
sewalk Why would anyone using Lastpass reuse account passwords or the master password? Common sense would dictate allowing Lastpass to generate unique and complex passwords for each account. This vulnerability seems to presuppose a great deal of stupidity on the part of someone smart enough to begin using Lastpass (or something like it) in the first place.Reply -
Christopher1 I do not understand this whole "Password Manager!" nonsense. I have used the same password on numerous websites (though none where I plan to use real money) and I have never gotten hit by one of these hackers except on websites where I used a very short one word password (which I then upgraded to little bit longer twoword+random symbol+Number and solved the issue).Reply
It seems to me that most of the problem is "Bad design choices!" on the part of the companies, such as allowing master lists of passwords to be downloaded off servers onto personal computers.
Most Popular




