Staying In Control With Trusted Platform Modules
How Does The TPM Actually Work?
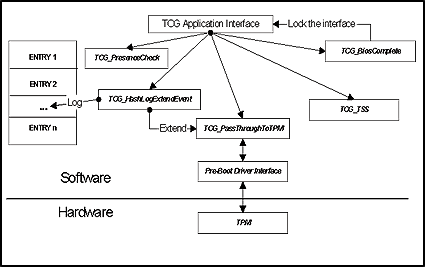
This is a schematic function table of a TCG system.
Trusted Platform Modules (current version 1.2) provide a so-called hash value for the complete system by using SHA1 (Secure Hash Algorithm). This value is assembled from information gathered from all key hardware elements, such as the video card and processor, in combination with software elements (the operating system, among others).
The computer will only start into an authorized condition if the TPM recognizes the correct hash. In this authorized condition, the operating system gets access to the encrypted root key, which is needed to run trusted computing protected applications and access trusted computing secured data. In the event of an incorrect hash value the starting condition will be untrusted, and access can be only granted to free files or programs.
Current manufacturers of Trusted Platform Modules are Infineon, National Semiconductor (though in the meantime, its trusted computing division was sold to Winbond) and Atmel. Additionally, there are TPM integrated chips from Phoenix/Award, processors by Transmeta, and network controllers from Broadcom, which used by Hewlett-Packard. Seagate has announced hard disk controllers with integrated TP functionality.
In the area of trusted computing software or software using installed TPMs, Wave Systems offers the Embassy Security center, the complete Embassy Trust Suite (document management, digital signatures) and its CSP Toolkit (Cryptographic Service Provider) for Windows programmers. IBM offers the ThinkVantage software (primarily with its own TPM Thinkpads), and Ultimaco provides the data encoding program SafeGuard Easy. Checkpoint sells security products for a whole number of tasks in the IT infrastructure, and Adobe pepped up its Acrobat version 6, making TPM supported control of PDF files possible.
Meanwhile, there are spin-offs and enhancements whose security characteristics were embedded even more strictly. Examples are Intel's LaGrande Technology, ARM's TrustZone, and starting in 2006, AMD's Presidio is expected to hit the market. Here, the decoupled security kernel of the operating system (Nexus in case of Microsoft's Vista) communicates between the TP module and the security components of trusted computing applications. Thus the user can verify that all hardware elements are recognized as TCG authorized, all installed software components are signed, and that no component bears a flawed serial number.
Should changes in the hardware configuration be detected, the TPM has to re-certify these via an online connection. An operating system based on Nexus operates with memory areas secured by the CPU - remember Data Execution Protection? - leaving trusted computing application data unchangeable from outside.
Stay on the Cutting Edge
Join the experts who read Tom's Hardware for the inside track on enthusiast PC tech news — and have for over 25 years. We'll send breaking news and in-depth reviews of CPUs, GPUs, AI, maker hardware and more straight to your inbox.
The current version 1.2 TPMs come with some nice features. Direct Anonymous Attestation (DAA) provides improved communication to other secured clients. "Locality" introduces different security levels to the TPM. "Delegation" differentiates the security characteristics from different users. "NV Storage" provides better use of non volatile storage media. "Transport protection" improves data transfer to non-TPM systems, and "Monotonic Counters" make it possible to retrace single steps in your work to resist so-called "replay attacks".
Current page: How Does The TPM Actually Work?
Prev Page Steps Of Development Next Page How Does This Compare To Intel's AMT?-
jimmy99099099 Could you give some detailed information about this board? i was given one a few weeks back and i have been trying to find out the information. (Decent selling price, How much RAM it supports, The best CPU for it (Currently a intel pentium 4,) and the basic conclusion of being able to use this as a standalone PC motherboard?) Also a wiring diagram would be appreciated as i have had no luck in wiring the thing up.Reply
Most Popular

