AMD Chipset Vulnerability Leaks Passwords, Patch Available
Apply this patch right away if you have an AMD CPU.
AMD has divulged details about a chipset driver vulnerability that can allow non-privileged users to read and dump some types of memory pages in Windows. This technique allows an attacker to steal passwords or enable other types of attacks, including circumventing standard KASLR exploitation (aka Spectre and Meltdown) mitigations (via TheRecord).
Word of the bug came as part of a coordinated disclosure with Kyriakos Economou, a security researcher and co-founder of ZeroPeril, who exploited the vulnerability to download several gigabytes of sensitive data from impacted AMD platforms — but as a non-admin user. AMD has prepared mitigations that can be downloaded either as part of its latest chipset drivers or by using Windows Update to update the AMD PSP driver (details of how to update are below).
AMD originally issued the patch several weeks ago, but without disclosing which vulnerabilities were addressed. This new disclosure answers those questions.
The security researcher first discovered the flaw with Ryzen 2000- and 3000-series platforms, but AMD initially listed only Ryzen 1000 and older chips in its advisory. The researcher noted the discrepancy in his report, and we followed up with AMD about the issue. AMD has since updated the page with a full list of impacted platforms that spans its entire modern consumer processor lineup as well as many older models (list below).
Economou attacked two separate issues with AMD's amdsps.sys driver for its Platform Security Processor (PSP), an embedded chip that manages chip security. The vulnerability allowed the researcher to extract multiple gigabytes of uninitialized physical memory pages. The full report goes deeper into the details of the vulnerability (PDF alert), but this passage summarizes the end result:
"During our tests we managed to leak several gigabytes of uninitialized physical pages by allocating and freeing blocks of 100 allocations continuously until the system was not able to return a contiguous physical page buffer.
The contents of those physical pages varied from kernel objects and arbitrary pool addresses that can be used to circumvent exploitation mitigations such as KASLR, and even registry key mappings of \Registry\Machine\SAM containing NTLM hashes of user authentication credentials that can be used in subsequent attack stages.
For example, these can be used to steal credentials of a user with administrative privilege and/or be used in pass-the-hash style attacks to gain further access inside a network."
AMD advises that impacted users update to AMD PSP driver 5.17.0.0 via Windows Update or to AMD Chipset Driver 3.08.17.735 (or newer in the future).
AMD's chipset driver vulnerability disclosure comes on the heels of news that all of its processors suffer from a Meltdown-like vulnerability that will require specific software optimizations to patch. However, AMD leaves that to software vendors to implement, meaning many types of software could simply go unpatched.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
AMD's processors have gained a reputation for being more secure than Intel's chips due to far fewer discovered vulnerabilities. However, as the smaller player with less overall x86 market share, it has long been opined that AMD's processors simply haven't been subject to as much poking and prodding from researchers. Now that AMD has taken a more significant portion of the market and continues to grow it is inevitable that researchers, and nefarious actors, will target the processors more frequently.
Here's a guide on how to update your system and a comprehensive list of affected processors, which includes all Ryzen CPUs and Threadrippers, along with dozens of other models .
How to Tell If You Have the Latest Drivers
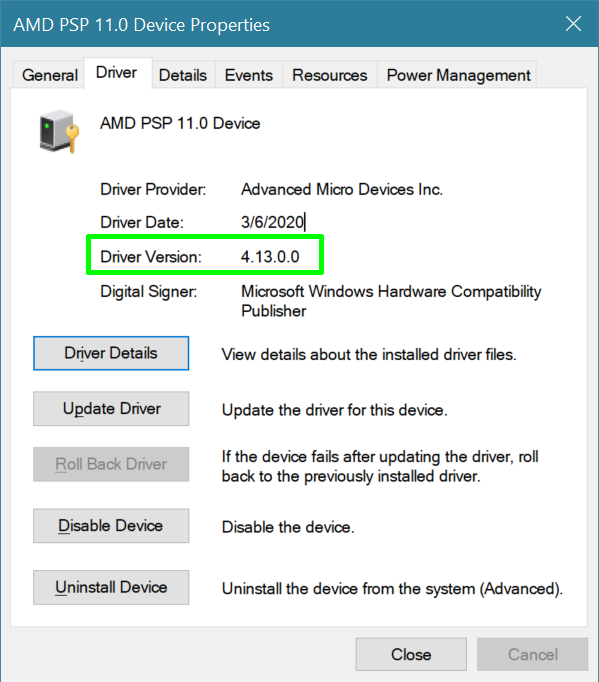
If you're wondering whether you already have the mitigations in place to protect your PC, you need to check to see if your AMD PSP driver is version 5.17.0.0 or higher. To do that:
1. Open device manager. You can get there either by hitting Windows key + X and selecting it from the context menu.
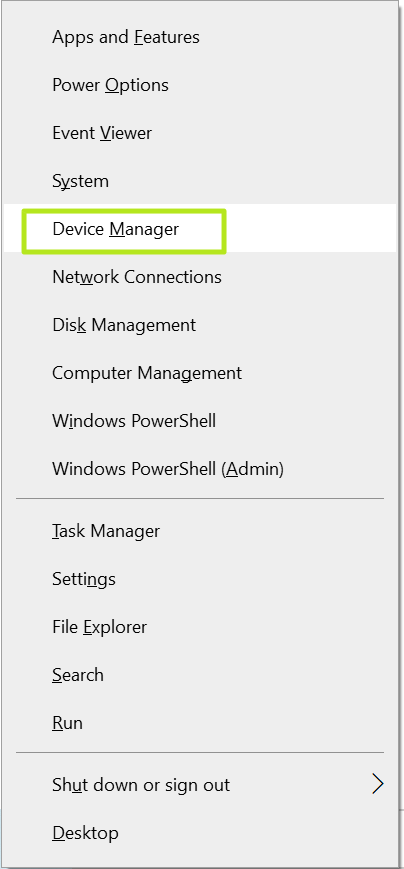
2. Open Security devices.
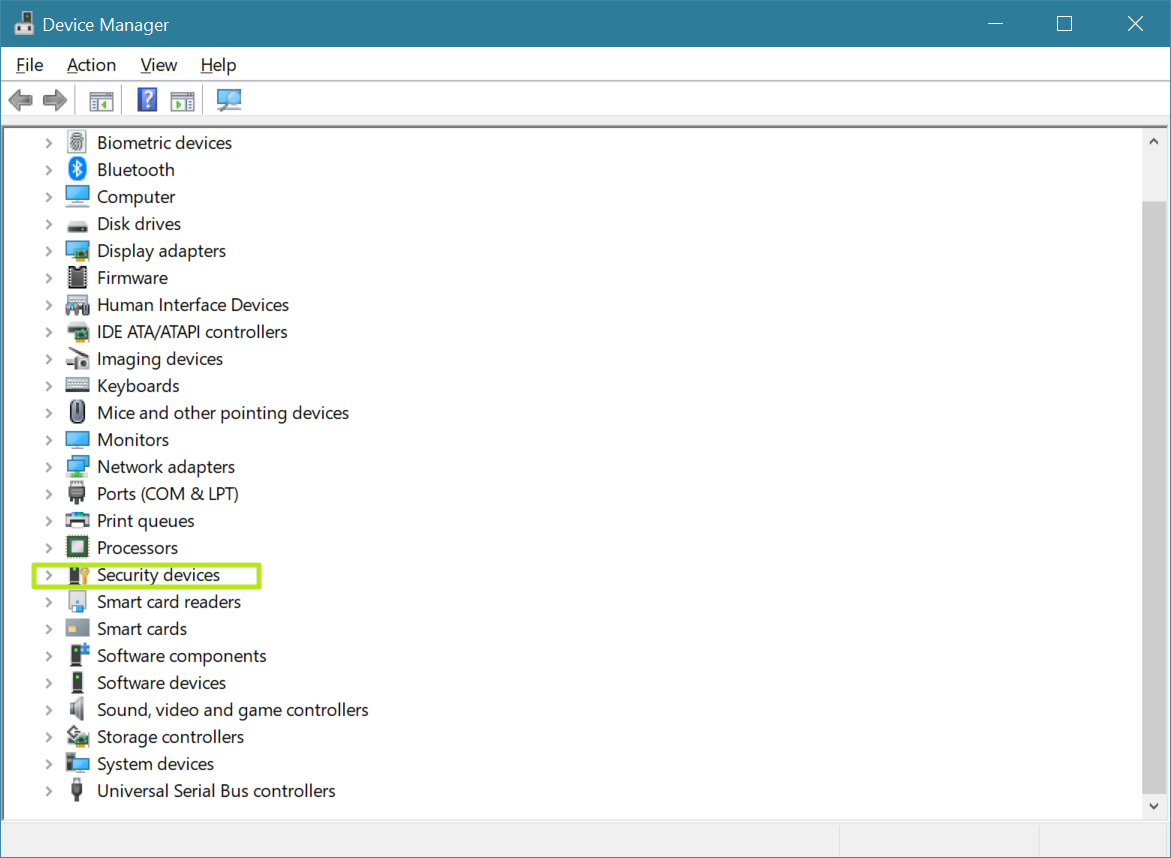
3. Right click on AMD PSP Device and select properties.
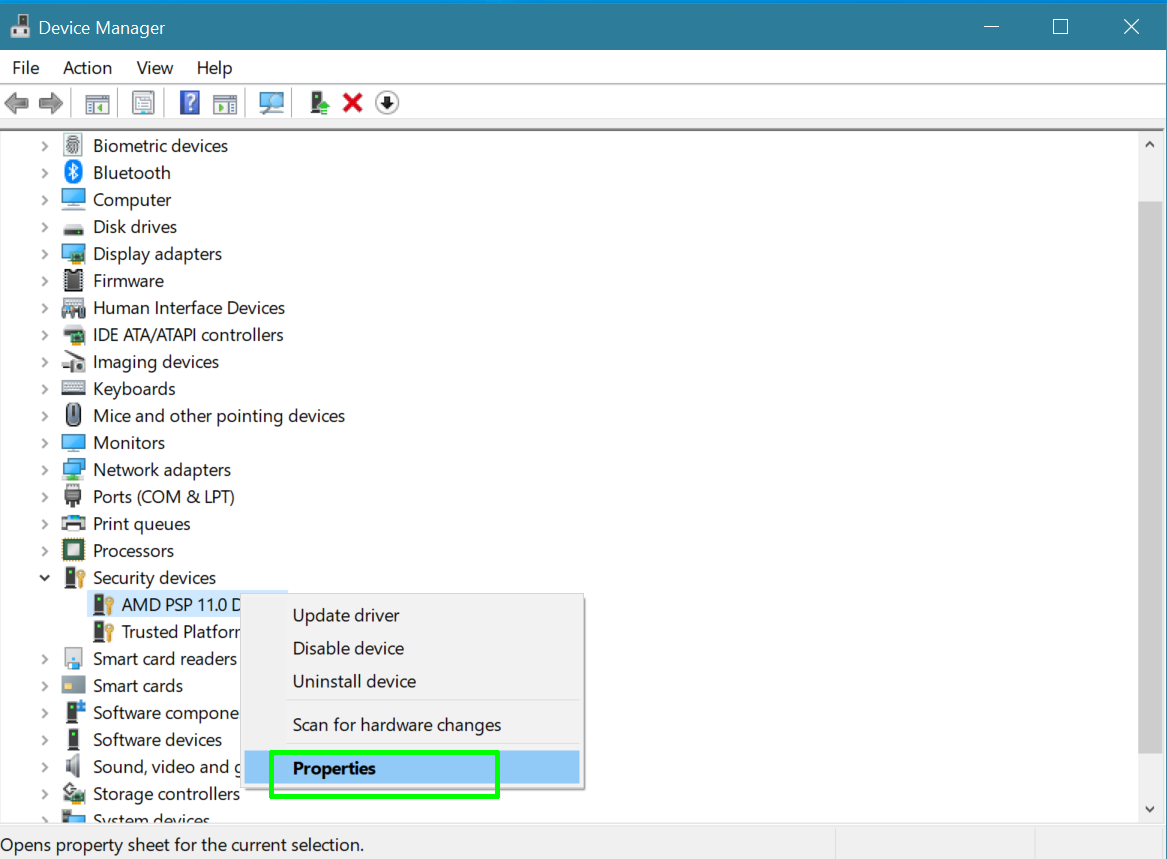
4. Click the Driver tab.
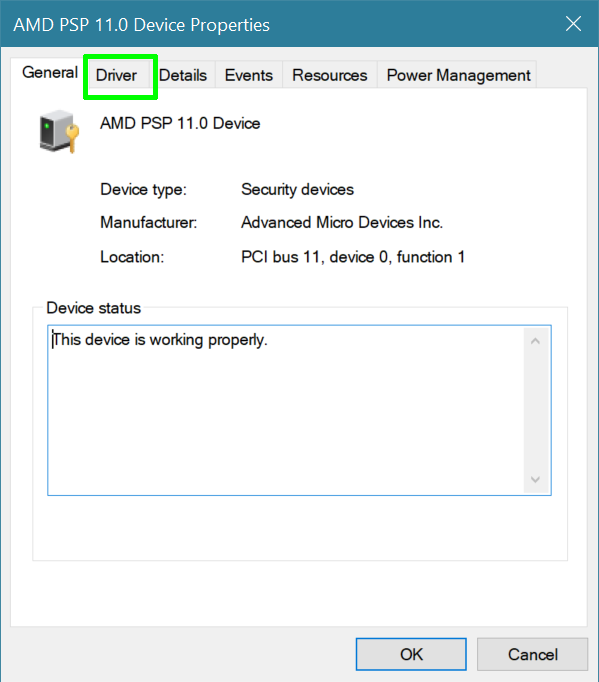
5. Look at the Driver Version number. If it's under 5.17.0.0 you need an update.
How to Update Your AMD Chipset Drivers
If you have one of the CPUS above, you're running Windows and your AMD PSP driver is lower than 5.17.0.0, follow these instructions.
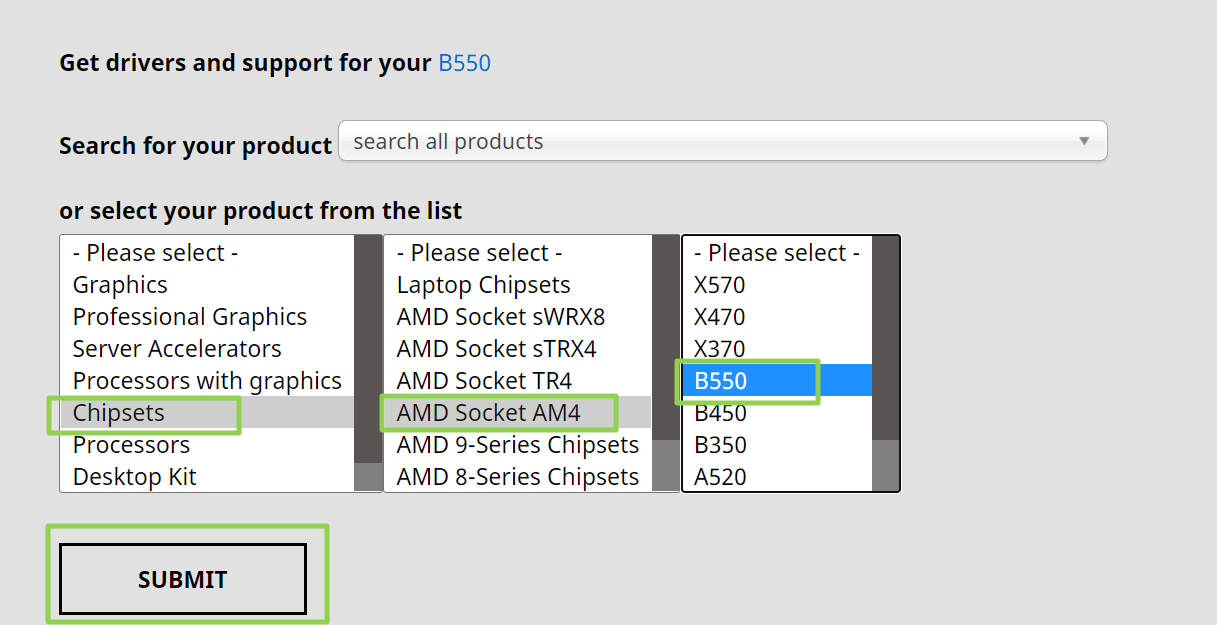
1. Navigate to AMD's Drivers and Support Page.
2. Select the chipset for your motherboard from the menu and click Submit. For Ryzen processors, you'll want to start by picking Chipsets->AMD Socket AM4 and then the chipset (ex: B550).
3. Click the Download button beneath "AMD Chipset Drivers." A zip file will download.
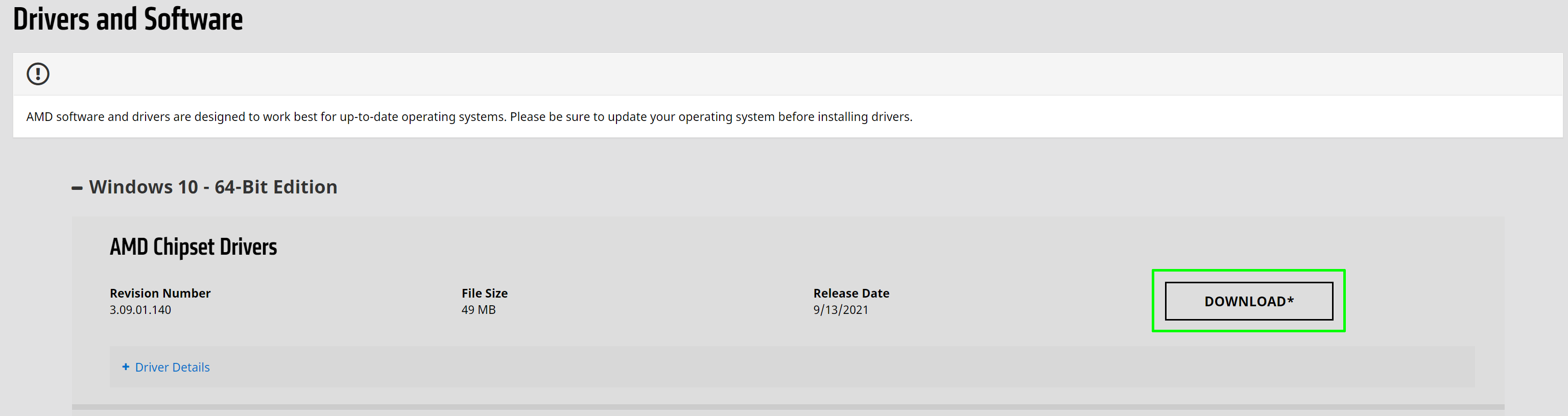
4. Open the zip file, extract the installer and run it. Be patient, because the software can take a few minutes to detect what you have and appear to be frozen. Don't click out of the window or, as per our experience, it may freeze.
5. Make sure AMD PSP Driver is checked and click Install.
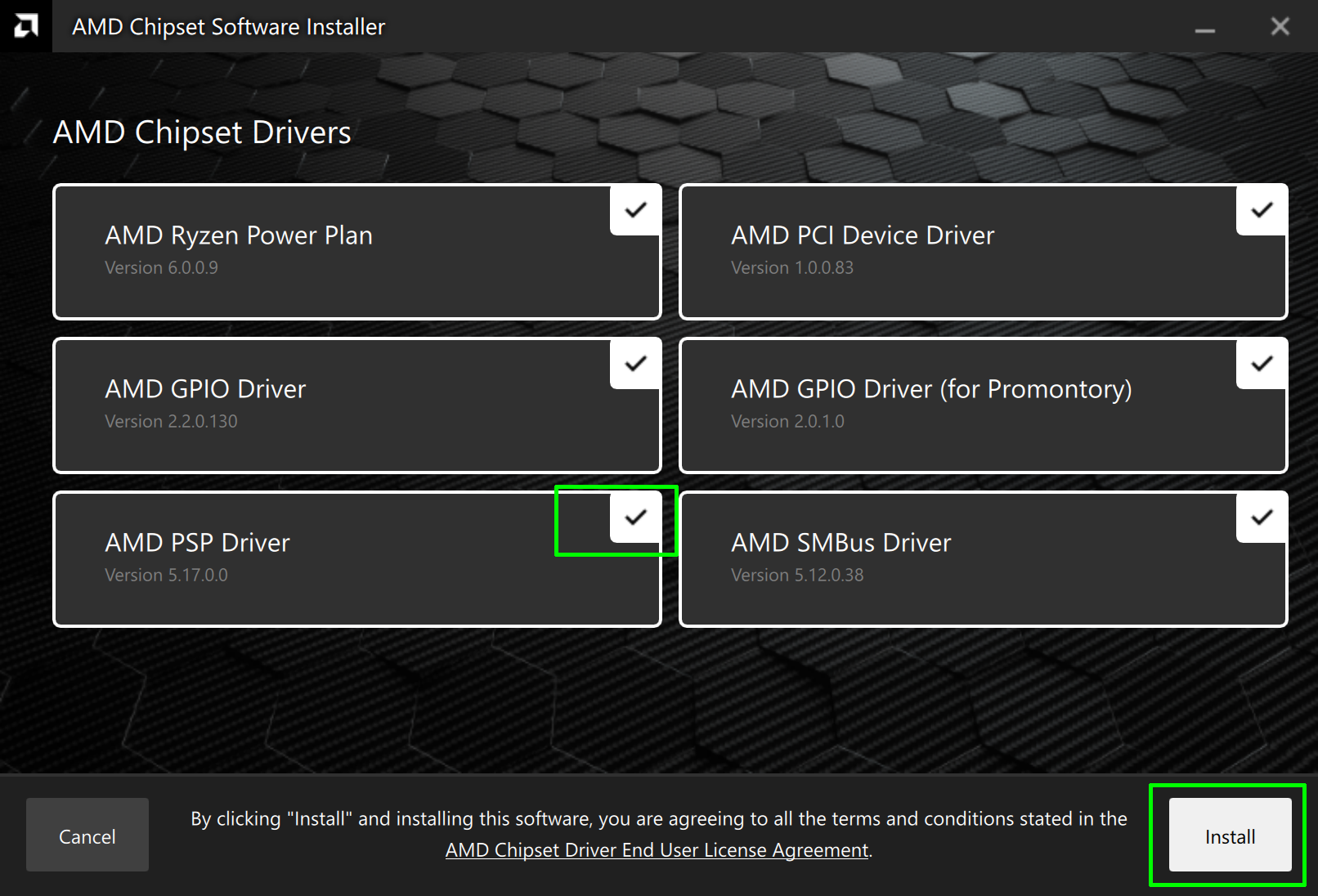
Again, you will need to be patient as the system will take several minutes downloading and installing updates.

6. Click Restart when the process is completed.
Your computer will reboot and you should have the updated AMD PSP driver now.
Affected AMD Processors
- 2nd Gen AMD Ryzen Mobile Processor with Radeon Graphics
- 2nd Gen AMD Ryzen Threadripper processor
- 3rd Gen AMD Ryzen™ Threadripper™ Processors
- 6th Generation AMD A series CPU with Radeon™ Graphics
- 6th Generation AMD A-Series Mobile Processor
- 6th Generation AMD FX APU with Radeon™ R7 Graphics
- 7th Generation AMD A-Series APUs
- 7th Generation AMD A-Series Mobile Processor
- 7th Generation AMD E-Series Mobile Processor
- AMD A4-Series APU with Radeon Graphics
- AMD A6 APU with Radeon R5 Graphics
- AMD A8 APU with Radeon R6 Graphics
- AMD A10 APU with Radeon R6 Graphics
- AMD 3000 Series Mobile Processors with Radeon™ Graphics
- AMD Athlon 3000 Series Mobile Processors with Radeon™ Graphics
- AMD Athlon Mobile Processors with Radeon™ Graphics
- AMD Athlon X4 Processor
- AMD Athlon™ 3000 Series Mobile Processors with Radeon™ Graphics
- AMD Athlon™ X4 Processor
- AMD E1-Series APU with Radeon Graphics
- AMD Ryzen™ 1000 series Processor
- AMD Ryzen™ 2000 series Desktop Processor
- AMD Ryzen™ 2000 series Mobile Processor
- AMD Ryzen™ 3000 Series Desktop Processor
- AMD Ryzen™ 3000 series Mobile Processor with Radeon™ Graphics
- AMD Ryzen™ 3000 series Mobile Processor
- AMD Ryzen™ 4000 Series Desktop Processor with Radeon™ Graphics
- AMD Ryzen™ 5000 Series Desktop Processor
- AMD Ryzen™ 5000 Series Desktop Processor with Radeon™ Graphics
- AMD Ryzen™ 5000 Series Mobile Processors with Radeon™ Graphics
- AMD Ryzen™ Threadripper™ PRO Processor
- AMD Ryzen™ Threadripper™ Processor

Paul Alcorn is the Editor-in-Chief for Tom's Hardware US. He also writes news and reviews on CPUs, storage, and enterprise hardware.
-
Wolfshadw Didn't see in the article where to check for your version of the AMD PSP Driver, so I found it under Device Manager --> Security Devices --> AMD PSP 3.0 Device.Reply
I'm running a Ryzen 5 2600 on a B450 chipset.
-Wolf sends -
dehjomz Ouch. Glad they fixed the problem but that’s a pretty severe bug for admin access to be granted to a non-admin user. So much for Intel being the x86 vendor with security problems…Reply -
Makaveli Seems THG is reporting this late?Reply
I'm already on this based on the previous chipset driver.
They just released a newer version last week that has windows 11 support.
version 3.09.01.140 -
InvalidError Reply
AMD likely has every bit as many security issues. Most of the flaws found in AMD CPUs were simply researchers checking whether AMD CPUs were vulnerable to the same or similar things Intel CPUs were after finding a new class of flaws on Intel chips, often finding out that ARM and other CPUs are also vulnerable to similar things.dehjomz said:Ouch. Glad they fixed the problem but that’s a pretty severe bug for admin access to be granted to a non-admin user. So much for Intel being the x86 vendor with security problems…
With AMD gaining more market share, you can expect more researchers to focus on AMD first and find more AMD-specific flaws. -
hotaru.hino Replydehjomz said:Ouch. Glad they fixed the problem but that’s a pretty severe bug for admin access to be granted to a non-admin user. So much for Intel being the x86 vendor with security problems…
This doesn't appear to be a hardware issue, just how the driver was implemented in Windows.ezst036 said:Linux unaffected? -
Giroro I can't find AMD PSP in my device manager or my bios, is that bad?Reply
Running 3700X on a MSI x570 BIOS ver E7C37AMS.F10 -
InvalidError Reply
The PSP handles things like firmware-based TPM functions, you probably need to enable TPM or whatever alternative name it may have in BIOS.Giroro said:I can't find AMD PSP in my device manager or my bios, is that bad? -
gdmaclew I followed all the instructions and it was successfulReply
Why, then, does my General Tab show no driver installed instead of This device is working properly?
Granted I am running a one year old BIOS (1407).
a/IAfcYWDView: https://imgur.com/a/IAfcYWD