Duo Beyond Helps Other Companies Be As Secure As Google
Two years ago, Google published a paper describing a "zero-trust" security framework for its enterprise infrastructure that went beyond firewalls. Duo Security has taken that framework and packaged it into a complete security solution that it can now offer to its corporate customers that want to avoid data breaches seen at Sony and elsewhere.
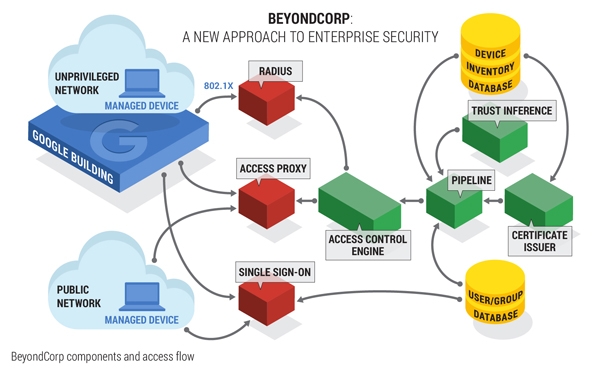
BeyondCorp Framework
Google said work started on the BeyondCorp security framework after it was attacked by an advanced persistent threat (APT) called Operation Aurora in 2009. It probably didn't implement much of the framework until years later, however, as Edward Snowden's 2013 revelations showed that the National Security Agency (NSA) gained access to all the data passing through Google's network by making its way past the company's perimeter defenses.
Afterwards, Google decided that it can’t rely only on firewalls or network isolation to secure its data. So it started to focus on tightening up device security and giving employees access only to the resources they need to do their jobs. That's what makes this model a “zero-trust” model. If you can’t trust anyone with access to the whole network, then it will be much more difficult for attackers to get free rein and steal whatever data they please.
This model is unlike the firewall-dependent security model that many corporations use today. In this older model, once attackers bypass the firewall, there is not much stopping them from gaining access to sensitive information.
‘Duo Beyond’
Duo Security is a fast-growing company that has doubled its user base every year for the past few years. You may know it for its two-factor authentication solutions. Duo is now also the first to package Google’s BeyondCorp framework and enterprise security philosophy into a commercial solution, Duo Beyond, that can be purchased by other companies to better secure their own IT infrastructures.
Duo Beyond shifts a company's security model from being firewall-based to being based on device information, device health, and the associated user. Because of this, companies can completely forego the use of a Virtual Private Network (VPN) when allowing users to access internal resources. Managers can also identify which devices are corporate or personal, control the apps to which users have access, and block untrusted endpoints.
According to Duo, deployment of its solution can be as fast as one hour. That’s how long it took Kayak, the travel company, to integrate the framework with its IT systems.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
"Duo Beyond is great for organizations with limited IT resources as it has a multiplier effect," said Steve Myers, Kayak Head of Security. "It allows one person to do the work of 10," he added.
Endpoint security is likely going to become increasingly important for both regular PC users and corporate users. Making devices more secure and restricting the default access a user has to a device makes sense if the goal is to maximize security. That's is why projects such as Qubes OS have also turned towards the enterprise environment, which shows that interest is growing for this type of solutions.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.