Microsoft promises to nearly double Windows storage performance after forcing slow software-accelerated BitLocker on Windows — new CPU hardware-accelerated crypto will also improve battery life, but requires new CPUs
Hardware-accelerated BitLocker promises faster SSD speeds and lower CPU usage
Microsoft has introduced a new form of hardware-accelerated BitLocker encryption in Windows 11, offloading encryption and decryption to a purpose-built cryptography accelerator baked into future CPUs to improve performance and efficiency. First announced at Ignite 2025 in November, the feature has been added to the latest versions of Windows 11 (25H2) and Windows Server (2025 with the September Update), along with UFS (Universal Flash Storage) Inline Crypto Engine technology. This new tech will undo the performance penalties that Microsoft imposed on its users by forcing them to use software-based encryption by default, offering twice the storage performance in some types of workloads.
According to our testing and support documentation, software-based BitLocker encryption is enabled by default on new installs of Windows 11 Pro. It reduces SSD performance by up to 45%, as encryption and decryption are handled by software running on the CPU. Hardware-accelerated BitLocker is already available for storage devices, with the encryption offload being handled on the storage device itself, be it an SSD or HDD, as long as it is TCG Opal-compliant. Most modern SSDs include hardware-based encryption, in which all encryption/decryption processing occurs directly on the drive with no performance impact.
However, Microsoft, being Microsoft, opted to force-enable the software version of BitLocker for new Windows Pro installs, hurting performance and battery life — you can only use hardware-based SSD encryption if you jump through a complicated series of largely undocumented hoops.
The company now plans to use a new hardware-accelerated BitLocker CPU implementation to address the issue it created, but it will take time to even become available.
Hardware-accelerated BitLocker will initially be available on Windows 11 devices with Intel vPro platforms based on upcoming Intel Core Ultra series 3 “Panther Lake” CPUs, with broader support planned. The latest version of BitLocker is expected to leverage new capabilities on upcoming chips, including crypto offloading, where the bulk of cryptographic operations will be moved from software running on the CPU to a dedicated fixed-function crypto engine. Additionally, BitLocker bulk encryption keys will be hardware-wrapped on select SoCs to improve security by reducing exposure to CPU and memory vulnerabilities.
Microsoft’s Rafal Sosnowski stated in a blog post, “When enabling BitLocker, supported devices with NVMe drives along with one of the new crypto offload capable SoCs will use hardware-accelerated BitLocker with the XTS-AES-256 algorithm by default. This includes automatic device encryption, manual BitLocker enablement, policy driven enablement, or script-based enablement with some exceptions.”
Microsoft claims that hardware-accelerated BitLocker can deliver performance improvements in storage and I/O metrics, such as sequential and random reads and writes, when compared with software BitLocker. Additionally, users can expect up to 70% reduction in CPU cycles required to process BitLocker workloads, thereby resulting in improved battery life.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
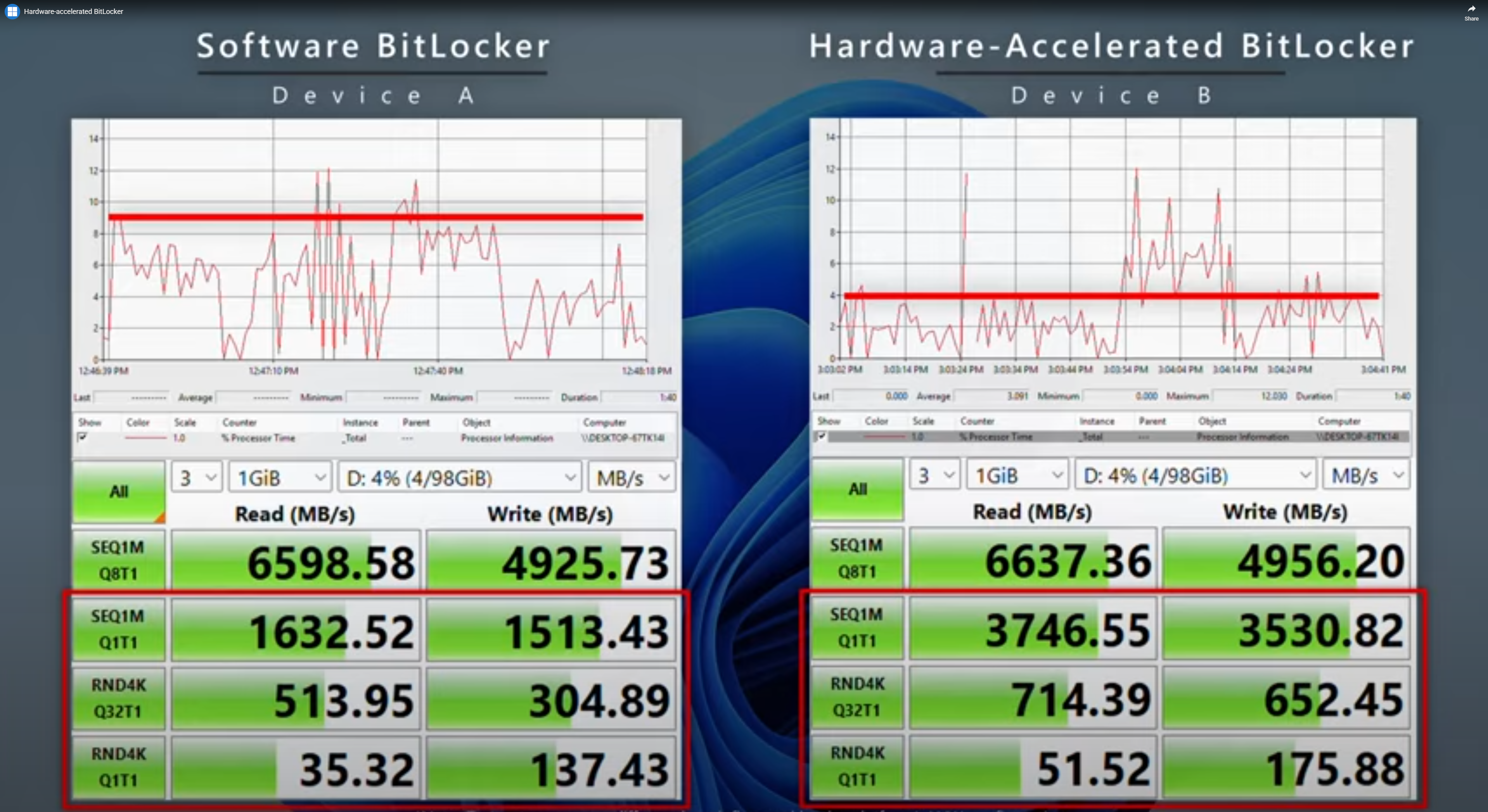
The company has also shared CrystalDiskMark performance test results in a video, showing that a drive with software-based BitLocker encryption achieved read speeds of 1632 MB/s on single-thread sequential workloads, compared with 3746 MB/s on a drive with hardware-based BitLocker enabled. Similarly, write speeds improved to 3530 MB/s from 1510 MB/s.
For now, hardware-accelerated BitLocker will be reserved for future Windows PCs, so widespread adoption will take time. That said, the feature's introduction indicates that Microsoft is finally rethinking how encryption should work on modern hardware.
Follow Tom's Hardware on Google News, or add us as a preferred source, to get our latest news, analysis, & reviews in your feeds.


Kunal Khullar is a contributing writer at Tom’s Hardware. He is a long time technology journalist and reviewer specializing in PC components and peripherals, and welcomes any and every question around building a PC.
-
Li Ken-un They didn’t show the latency. Since this still happens on the CPU, I assume there is some non-zero penalty for latency-sensitive workloads. OPAL would be zero penalty, which you could have yesterday.Reply
