Report: Security Of U.S. Agencies In Dire State, Employee Logins Widely Leaked
A CIA and Google Ventures-backed private company called Recorded Future released a report today that unveiled that login credentials of government employees from 47 agencies have been leaking everywhere on the Web for more than a year.
The data was gathered through publicly available "open source intelligence" for a one year period up until November 2014. The company managed to collect this information from 17 "paste" websites such as Pastebin.com, as well as other public sources.
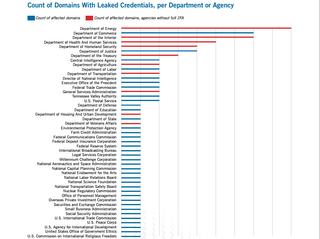
When Recorded Future was doing its intelligence analysis over this period, it found that the Department of Energy (which also handles nuclear safety) and the Department of Commerce were hit the hardest.
In February of this year, the Office of Management and Budget (the same one pushing all federal websites to adopt HTTPS right now) found that 12 agencies weren't using any form of two-factor authentication. Those 12 agencies include departments that should have the highest security standards, such as the departments of Health and Human Services, Treasury and Homeland Security.
Recent Senate testimony on the OPM breach that exposed the data of over 4 million government employees, even more government contractors, and potentially 18 million social security numbers, suggested that the lack of two-factor authentication as well as the lack of encryption directly affected the success of the hack.
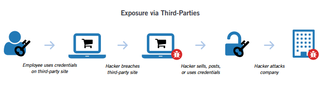
Recorded Future also found that many government employees have used their government emails to log in to third-party Web services. When those services got hacked, it also exposed the federal employees' emails, which made it easier to then log in to government systems, as well.
Recorded Future analyzed over 660,000 open web sources but focused on the small subset of paste sites where such information is often shared. However, that also means the government employees' exposure could be much bigger than Recorded Future's small analysis sample.
Stay on the Cutting Edge
Join the experts who read Tom's Hardware for the inside track on enthusiast PC tech news — and have for over 25 years. We'll send breaking news and in-depth reviews of CPUs, GPUs, AI, maker hardware and more straight to your inbox.
Right now, the U.S. government doesn't seem to have a strong strategy for defending against such large-scale attacks. Many federal agencies, including those that deal with highly sensitive information, use security measures that would be considered subpar today.
It's becoming clear that the U.S. government needs to drastically increase the security of its digital properties before any more data is stolen. It also needs to do so quickly, before those who have already pilfered sensitive data in the recent hacks can start using it against the very systems the government is trying to secure.
Follow us @tomshardware, on Facebook and on Google+.
-
alidan i believe the government is letting this happen or even faking it to grab more power or retain power it was already given.Reply -
Alec Mowat In other news, NATO announced planes to bolster it's network security defense.Reply
If you are young and looking for a well paid career, you may want to start in Network Security now, it's going to get big. -
clonazepam Replyi believe the government is letting this happen or even faking it to grab more power or retain power it was already given.
We're slowly being disarmed and prepared (TSA patdowns but someday everywhere) for the keys to the kingdom to be handed over to China. One or two more generations for the majority of the most lethal firearms to be phased out. The plans for the railway are already in the works. ;)
I would say we should all just move to Australia, but those Aussies censor all the best video games. :( -
clonazepam As a veteran of the US Army, I cannot even remember how many letters I received from my government between the years of 2001-present that notified me that all of my personal information had been lost or stolen.Reply
It was kind of funny. Many of them even included an explanation. One of them was because of an unsecured laptop being stolen. There was a hijacked truck traveling from a social security office in California carrying the old computers to somewhere, assuming they were on their way to be destroyed.
None of this information surprises me in the least. Old office computers aren't destroyed on the spot. They are transported somewhere. Being computers, the hardware has value. Being from the government, their data has value. It's all just too tempting for the average people that might be in the know, from the trucking company employees, to the people hired from resume websites, to come in and dismantle the old, and install the new systems.
Yeah, I was actually hired off monster.com to show up at a social security office and install all of the new computer systems throughout the entire building. 3 of us were overseen by a single lady after hours, off in a completely different part of the building. Of course, with practices like this, this sort of stuff is going to happen. -
cats_Paw Replyi believe the government is letting this happen or even faking it to grab more power or retain power it was already given.
i believe the government is letting this happen or even faking it to grab more power or retain power it was already given.
We're slowly being disarmed and prepared (TSA patdowns but someday everywhere) for the keys to the kingdom to be handed over to China. One or two more generations for the majority of the most lethal firearms to be phased out. The plans for the railway are already in the works. ;)
I would say we should all just move to Australia, but those Aussies censor all the best video games. :(
In our time the world is so screwed up that you actually have to keep moving from country to country.
Yesterday I received a notification that my passport will lose its validity in a short period of time, and that If I do not update it, I will lose access to my account (they wont close it, I just wont be able to get anything from it).
The reason: Anti-terrorist law number ******
So, in short, a bank can size your money (not a law enforcement agency, the bank) if you do not keep your information up to date for them based on a security law.
Its interesting that the beneficiary is the bank in this case...
So, its time to start looking for another country to live in? -
bourgeoisdude It is amazing to me that HHS, which rains fire upon unsuspecting violators of HIPAA and similar laws, don't even use two-factor authentication themselves. Oh, and they haven't notified their employees within 30 days of a breach. So who is it THEY are going to pay more than $2,500,000.00 in fines to?Reply
There really should be an amendment to the constitution that lawmakers and agencies that implement such rules must be subjected to the same rules, and any "fines" they have to pay would be in the form of tax rebates to their constituents who pay their IT departments' salaries. -
dgingeri It's the government. What else would you expect? They're incompetent at everything else except war.Reply -
coolitic ReplyIt's the government. What else would you expect? They're incompetent at everything else except war.
No they're incompetent with war too.
Most Popular




