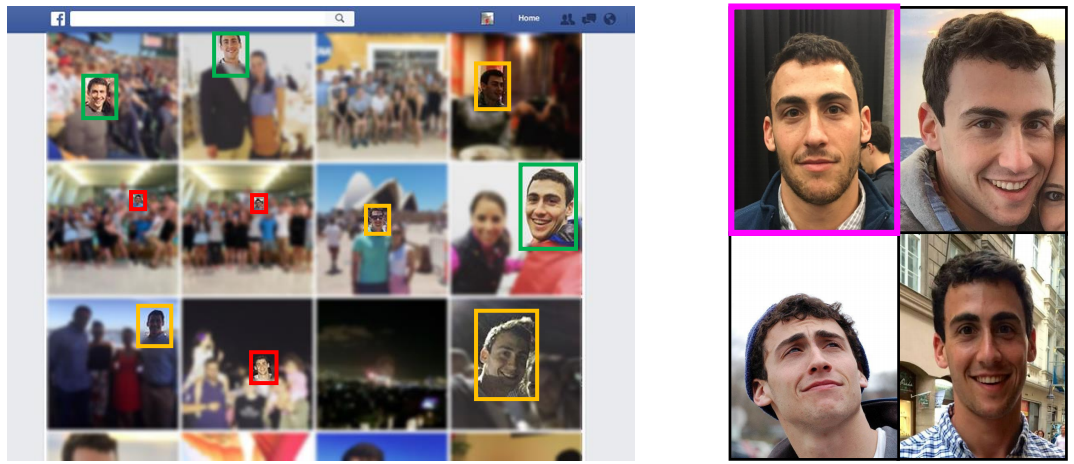
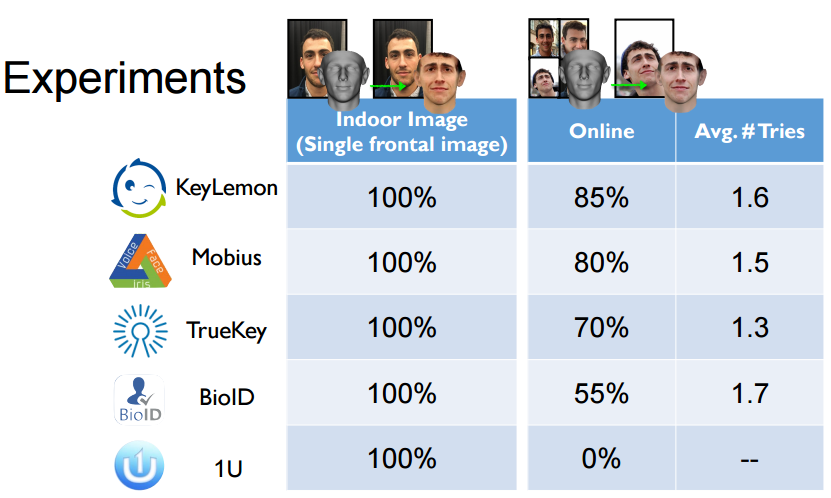
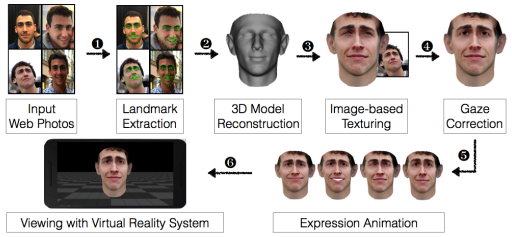
Most Face Authentication Systems Can Be Bypassed By 3D Models Of Facebook Photos; Now What?
Face authentication systems have long had a problem with being tricked by still images. However, as the authentication systems became smarter, so did the mechanisms to fool them. Security researchers from the University of North Carolina discovered that 3D models of faces made from Facebook photos can bypass the majority of face authentication systems in use today, with up to 100% success rate if the photos are taken indoors.
Bypassing Face Authentication With 3D Virtual Faces
Face authentication systems have always had a problem with being fooled by 2D photos. For instance, when Android 4.0 came out with face authentication, it was quickly proven afterwards that the system could be bypassed with a photo. Google later updated the system to require the subject to blink, but that solution was also easily bypassed: Two photos would be alternated, one with the subject having his eyes open and one with his eyes closed, thus fooling the system into thinking the subject was blinking.
Google, and other makers of face authentication systems, have kept improving these systems so it’s not as easy to bypass them as putting some photos in front of the camera anymore. However, this seems to be a cat and mouse game, as security researchers (or their adversaries) aren’t usually far behind in cracking new systems, too.
Adversaries and researchers have come up with solutions such as using videos of a person’s face or a 3D-printed mask to bypass modern face authentication systems. Now, even 3D virtual models can be made from Facebook photos that can bypass most face recognition systems. It’s likely that the technology companies will solve this problem, too, only for the new solutions to be bypassed yet again.
How The Researchers Did It
The researchers from the University of North Carolina used publicly available 3D face reconstruction methods from the field of computer vision in order to overcome limitations such as a potential victim not having enough photos publicly available or the photos being taken in environments with varying levels of lighting.
After the virtual face would be constructed, the researchers would use VR systems to fool the liveness detection of the face authentication system. The authentication system would present the virtual face in a VR world, and the face could be made to move in the same way humans would move their faces in front of a face authentication system. The fact that a VR world can be made to replicate the real world as much as possible with enough effort and hardware resources is also what makes defense against this type of attack rather difficult.
Mitigations Against The VR-Based Attacks
The researchers said there could be three types of technologies that could make it harder for this type of VR-based attack to work. One is using random projection of light patterns. The other is detecting minor skin tone fluctuations related to pulse, and the third is using illuminated infrared (IR) sensors (which is what Intel’s RealSense cameras use for Windows Hello authentication).
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Of the three, the researchers said the first two could still be bypassed with additional effort from the adversary, but a third would present more significant challenges. It could still bypassed if the adversary built specialized VR hardware with IR displays, which could be well within the reach of state-sponsored adversaries or even attackers with fewer resources.
The Future Of Biometric Authentication
The researchers said that mobile devices with IR front cameras for face authentication could still significantly improve the security of current face authentication technologies in smartphones today. However, given the fact that many people have high resolution photos of themselves all over the internet anymore, it’s still only a matter of time before any defensive technology for face authentication can be broken.
That’s why face authentication may be the weakest form of biometric authentication currently available. In ascendant order of strength, face authentication would be followed by iris authentication (which can still be extracted from photos, but the photos would need to be much higher resolution), voice authentication (extracted from insecure wireless communications), and then fingerprint authentication.
Although older fingerprint authentication systems could be bypassed with still images or molds of fingerprints, the new systems have gotten smarter. It’s also much harder to get a high-resolution photo of someone’s fingerprints than it is to get one of their face, and harder still to get a real fingerprint from which to make a mold.
However, fingerprint authentication systems have the same major weakness as all biometric authentication systems: If a fingerprint is stolen, the same way passwords are stolen by hackers all the time, then you can’t really replace it (or rather, your options become extremely limited). Meanwhile, if a password is stolen, you can replace it with virtually infinite options, and the same goes for chip and PIN smart cards or other similar hardware tokens.
The promise of simple yet secure authentication is still highly alluring to technology companies, as well as financial services companies, which is why there’s currently a significant effort to make biometric authentication ubiquitous. However, it would probably be best if biometrics are relegated to effectively being usernames (to identify the person more easily, which is why some countries require them for passports or national IDs), while still using some kind of password or smart card solution in combination with the biometric authentication system.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.