Free Phishing Kits Come With A Cost For Beginner Cybercriminals
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
You are now subscribed
Your newsletter sign-up was successful
After analyzing over a thousand phishing kits, data security company Imperva released a new report on the impact of phishing on internet users. The report found that half of the phishing kits belong a single family of kits, and also that most report back to third-parties (likely their creators), even as they're sold or rented to other attackers. Imperva also discovered that the phishing kit authors don't always play nice with their "customers."
Phishing Industry
According to Verizon’s 2017 Data Breach Investigation, 81% of the enterprise data breaches are leveraged through stolen credentials and/or weak passwords. Imperva also noted that the once-relatively small phishing world of hackers has turned into a real industry.
Today, it’s much easier to build a phishing tool with "Do-It-Yourself" (DIY) kits. Furthermore, the business model of phishing kits has also evolved. Imperva discovered that in the underground cybercrime world, you can now find phishing kits for any purpose and for any cost.
Some of them are even distributed for free, but the security company learned that, perhaps ironically, many of these have built-in backdoors. This way, the original authors can also benefit from the information the kit user would then steal from companies and internet users. The kit authors reduce their risk and increase their ROI by harvesting the work of inexperienced hackers.
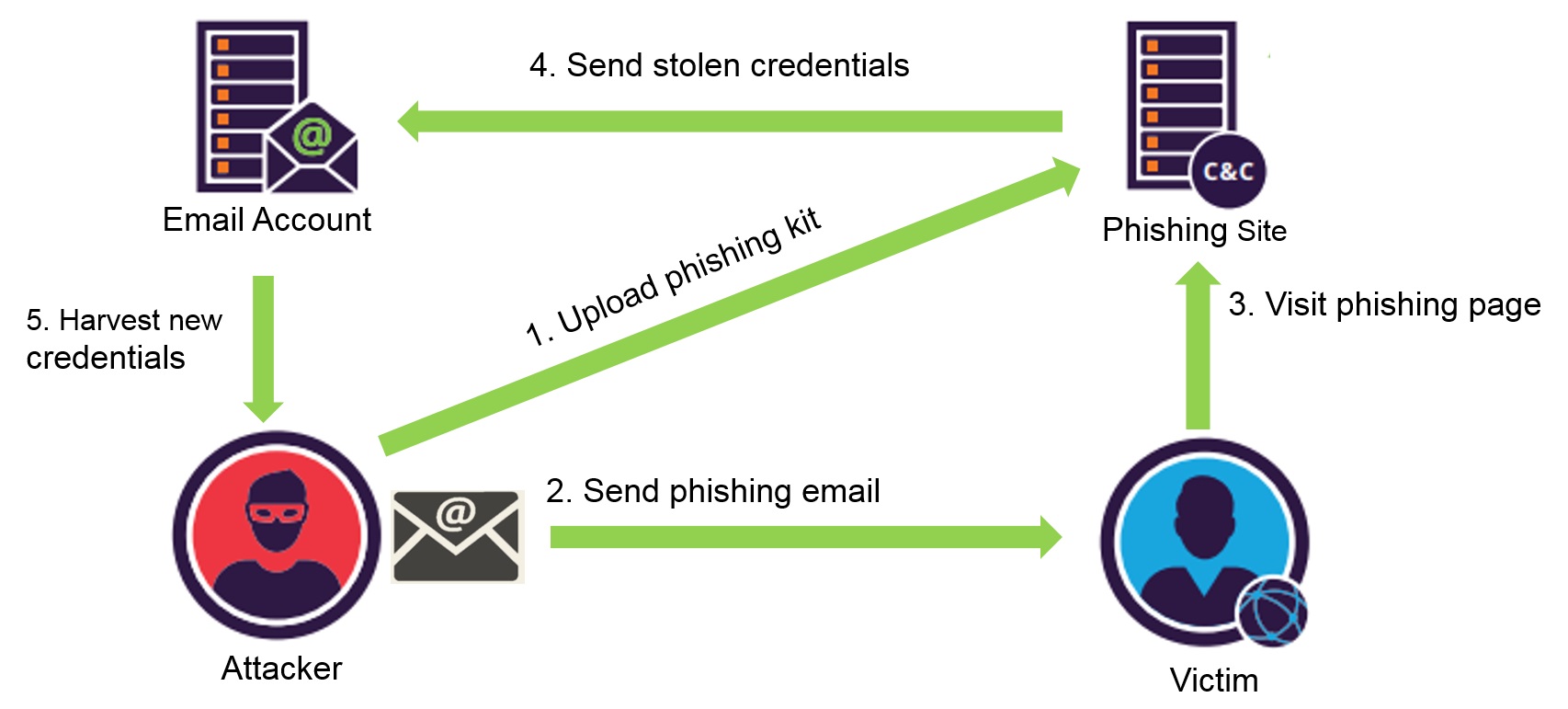
Phishing Attack Flow
A standard phishing attack would include the following:
- The attacker buys a compromised server and uploads the phishing tool there
- They then use a spam service to send a burst of phishing emails
- Some of the victims input their credentials on the login pages given by the attacker, not knowing it’s not a real page
- The phishing kit then sends the collected credentials to the attacker’s email address
- The attacker makes use of the stolen credentials
Phishing Kit Analysis
Imperva was able to analyze 1,019 phishing kits by collecting them from two sources: TechHelpList.com, from where it got a list of long-lived phishing kits, and the Open Phish feed, from where it got brand-new kits used in live campaigns. This was possible because the attackers often forget to remove their phishing kit from the server, after they’ve collected the victims' credentials.
The phishing kits are usually composed of two types of files: the resource files needed to clone the original pages, in order to trick the victims into believing they’re logging to their real accounts, and the scripts, which would collect the emails and passwords and then send them to the attackers.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
From its analysis, Imperva found that 98% of the attackers would send the collected credentials to email addresses belonging to 53 domains (Gmail being the most frequently used, by far), while the rest would save the credentials directly on their servers. What 25% of the attackers may have not known is that their stolen credentials were also being sent to some other predefined email addresses, which Imperva believed belonged to the phishing kit authors. These predefined email addresses were usually obfuscated.
Blocking Unwanted Visitors
Imperva found that many kits were using various techniques to hide that their servers were used for phishing, including IP blacklists, txt files that would block indexing from bots, and PHP scripts that would check if the remote IPs are allowed to visit the site.
The kits also included mechanisms to evade blacklists and were generating new random locations at which to send the victims. This method allows the attackers to hide their kits from being added to ISP or various services’ blacklists.
Role-Based Ecosystem
Imperva concluded its reported by saying that phishing has become much more profit-driven than in the past, with multiple actors occupying different roles in the industry.
The authors, who are generally veterans in the field, now tend to stick to creating the kits and selling them, or offering them for free, while making their money through other "business models." Meanwhile, the campaigners, or the ones who perform the attacks, focus on maximizing their phishing revenue and leave the technical details to the authors. However, as the up-and-coming cybercriminals leave the technical details to the phishing veterans, they also risk being cheated by them.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
JoeMomma Last month I had a moment of stupidity and fell for a phishing attack.Reply
It's been a major pain. Reporting it to the FBI, Google, ebay, Amazon, PayPal and CVS only made them mad and they stepped up their attacks.
Always look for https:\ on any site you visit. Hey Tom's, Why isn't your site secure? -
berezini I can see it now, "congratulations" the embedded videos filled on Tom's hardware have been injected with spyware or phishing kits enjoy your world crumbled"Reply