HDMI Firewall Protects Your Display Port (but Not your DisplayPort)
A dongle can keep your HDMI ports, and your network, safe.
Any device sporting a chip and some form of communications protocol can be hacked - that's almost as strong a law as those governing gravity. And sometimes, threats come from where you'd least suspect them. An electronics project by user kingkevin - uploaded on source code repository CuVoodoo git - now aims to help consumers and businesses to protect themselves from an attack vector that's frequently forgotten: a simple HDMI port. Enter the HDMI Firewall.
The HDMI firewall is little more than a physical dongle that can be directly connected to the HDMI port you want to secure. It works by blocking all data that's not related to video and audio streaming. One dongle is required per port to be protected, but they can be repurposed across different devices with a bit of work.
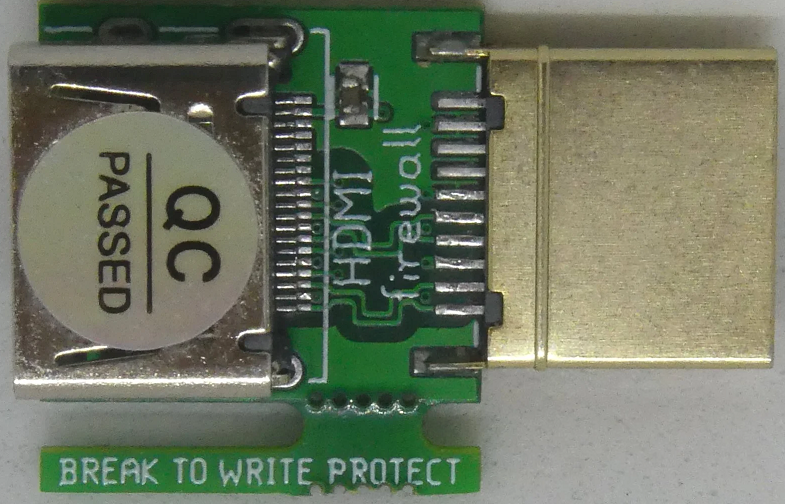
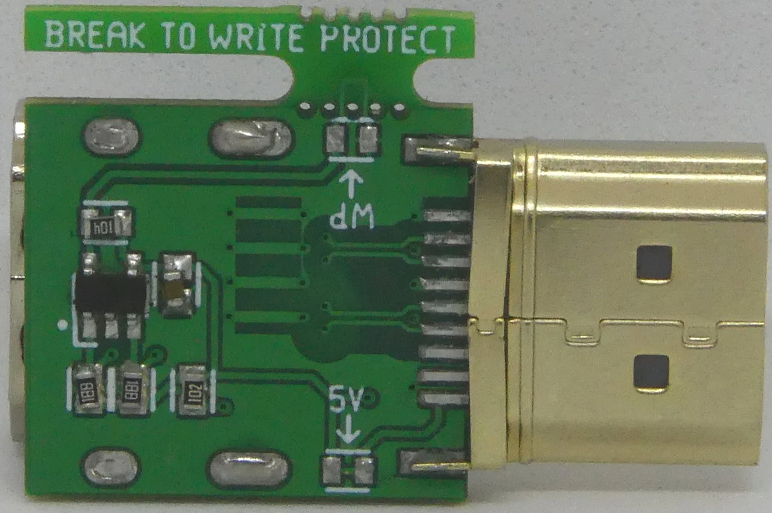
While we may think of HDMI connectors as mere passthroughs for audio and video data, there are a number of parallel protocols that transmit more information than we'd expect. One of the more obvious ones is the addition of HDCP (High-bandwidth Digital Content Protection), a DRM (Digital Rights Management) encryption solution that ensures the transmitted feed isn't copied as it travels towards its destination, and the main culprit of HDMI-related headaches.
Other essential yet often-forgotten HDMI features that aren't specifically related to video and audio include HPD (Hot-Plug Detection) and CEC (Consumer Electronics Control), the later of which allows HDMI devices to be controlled via your remote control - just to name a few.
Interestingly, HDMI also supports I2C - a synchronous, serial communication bus invented forty years ago by Philips Semiconductors. This particular protocol has been shown - time and again - to be vulnerable to intrusion. Programmable controller boards such as an Arduino or Raspberry Pi have been used as means to hack it. But in the HDMI Firewall, it's used to bolster your protection.
The HDMI Firewall needs to be programmed according to the device it's being installed on. Users will need to copy the Extended Display Identification Data (EDID) information of the equipment to protect, which includes information such as supported resolutions, for the passthrough to work. This data can be read by using the I2C-based Display Data Channel (DDC) interface from the device.
This EDID data is then written into the EEPROM of the HDMI firewall, which features a breakable write-protection tab that locks the connector's EEPROM from any further writes. If the Firewall needs to be moved to a new device, users can re-disable write protection by putting a solder blob across two pads on the device, rewrite it with the new devices' EDID data, and then re-enable protection by removing the solder connecting the two pads.
The original post by the creator features a pretty straightforward description of the methods used. Being in an open-source repository, users can freely inspect and fork the code. Healthy discussion on the topic is also taking place at HackerNews, if you're looking for further details on the project and the intricacies of HDMI vulnerabilities.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.

Francisco Pires is a freelance news writer for Tom's Hardware with a soft side for quantum computing.