Apple's iCloud Keeps Forgetting To Delete Users' Synced Data
Users’ deleted notes should completely disappear from Apple’s servers after 30 days. However, ElcomSoft, a Russian company developing computer and mobile forensic tools, discovered that the deleted notes could still be extracted from Apple’s servers after the 30 days had passed, even though they were no longer visible to the users.
Deletes Notes Extracted From iCloud Servers
Apple’s Notes app automatically stores users’ notes in the cloud, when iCloud is enabled. Users can delete their notes, and they will remain in the app’s “Recently Deleted” folder for another 30 days, as expected.
However, ElcomSoft discovered that Apple was not deleting the notes once that 30-day period was over, even if the files were no longer in the Recently Deleted folder. Therefore, users would assume that the notes were permanently deleted when they actually weren’t.
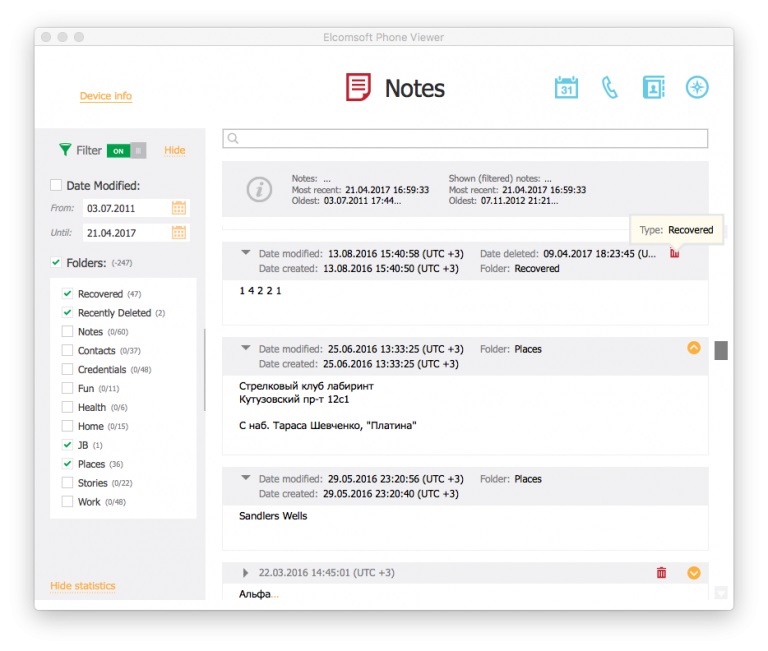
The company used its own Phone Breaker forensic app, which can extract sensitive information from a phone if the files are not well protected by the mobile platform. If a user’s credentials are used, the tool can also download whatever data is available in the user’s iCloud account, even if the data is not visible to the user anymore.
According to ElcomSoft, a user’s authentication token can also be extracted from the PC to bypass the iCloud authentication process, which sounds like another security design flaw Apple needs to fix.
The company demonstrated how out of the 334 notes extracted from a user’s (test) account, two were found in the Recently Deleted folder, but 47 notes were deleted more than 30 days earlier. These notes weren’t accessible to the user under any other means, but they were still there on Apple’s server.
Apple iCloud’s Privacy Issues
ElcomSoft’s recent discovery isn’t the only time Apple’s iCloud has had issues with previously deleted user data. Back in 2016, ElcomSoft discovered that users’ deleted photos were kept on Apple’s iCloud servers for years after the users had originally deleted them. After ElcomSoft’s public disclosure, Apple fixed the issue.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Earlier this year, ElcomSoft found another similar problem with iCloud: Deleted Safari browsing history also remained stored indefinitely on Apple’s servers. Users tend to delete their browsing history primarily for privacy reasons. Your browsing history can show your habits, what type of content you like to read, what videos you like to watch, your political affiliation, and so on. Few would like their browsing histories to be made public.
Last year, ElcomSoft also noticed that Apple was storing everyone’s call records on its servers by default, with no way to disable it. This is another privacy issue that Apple doesn’t seem willing to address, despite “taking privacy very seriously.”
This is a problem with Apple’s iMessage, too, which essentially nullifies whatever end-to-end encryption it may be using when iCloud is enabled. There’s no way to disable iMessage syncing alone. Therefore, if iCloud is enabled, your “end-to-end encrypted” messages will be stored on Apple’s servers, from which law enforcement or hackers can get them just like they could from any other chat application.
Apple could at least allow users to disable iMessage syncing when iCloud is enabled. The company should arguably have the syncing disabled by default, considering users expect them to be end-to-end encrypted and private.
ElcomSoft had previously suggested that Apple also reveals the following:
Provide full details what data do they store in the iCloudProvide information what data they reveal (well, MAY reveal) to law-enforcement, if different from the above. Yes, such document is already there on Apple’s web site, but now we know that it is not complete.Allow “opt-out” for all categories of data saved in the iCloud, and/or provide an ability to delete the particular category (anything from web history to the list of iTunes purchases). That is not only about the call logs only. We do know that Apple stores even more.
No Fix For Deleted Notes Yet
ElcomSoft said that Apple had fixed the previous deleted photos and browsing history issues, but it’s yet to fix this recent software flaw. However, the company wondered how many times this will keep happening to its iCloud service. The more it happens, the less users can trust that their files are actually deleted from Apple’s servers.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
lahma You mean Apple acts all high and mighty, suggesting they take their users' privacy and security much more seriously than other companies, yet they actually care so little about it, that even when researchers point out their blatant flaws, they don't even give their users the dignity of response? I gotta tell you... I'm shocked... Just shocked... Surely all the Apple fanboys out there will immediately sell their Apple devices and never purchase another one ever again. "No," I hear you say? Apple can do whatever they want and their loyal users will take it like champs and keep on purchasing Apple devices? Wow, what troopers.Reply -
hellwig Google's a lot simpler. Assume they keep everything and get on with your life.Reply
I think the discussion of end-to-end encrypted messaging might be misleading. Presumably Apple cannot store the un-encrypted messages, can it? I assume it has to be storing encrypted messages, and presumably that's just raw data Apple (and the FBI, hackers, etc...) will never be able to do anything with (without dedicating a lot of processing power to decrypt).
If Apple is storing un-encrypted messages, that's not end-to-end encryption. -
mrmez Sounds pretty dumb that they'd fix previous iCloud issues and just skip checking the rest.Reply
The iMessage thing is also concerning, but I wonder just how easily these can be exploited, given the article says "with users credentials", and the fact the FBI not so long ago went to extraordinary lengths to get access to a locked iphone.
LMAO at the Google comment. Even though they're all pretty much the same. -
therealduckofdeath Obviously they can't delete it before the NSA's confirmed that their backup is complete. Duh.Reply -
Reply
That's a weird statement. If Apple can't delete files without decrypting them first, how can Apple send those files back to the phone?19711508 said:I think the discussion of end-to-end encrypted messaging might be misleading. Presumably Apple cannot store the un-encrypted messages, can it? I assume it has to be storing encrypted messages, and presumably that's just raw data Apple (and the FBI, hackers, etc...) will never be able to do anything with (without dedicating a lot of processing power to decrypt).
I can only imagine how weird of an exchange that would be...
iPhone: "iCloud, give me file 42!"
iCloud: "Here you go, file 42."
iPhone: "iCloud, delete file 42!"
iCloud: "Ok, deleting file 42."
* 30 days later *
iPhone: "Well, did you delete it?"
iCloud: "Wait, I'm still decrypting it."