Wi-Fi Security: Cracking WPA With CPUs, GPUs, And The Cloud
Securing Your WPA-Protected Network
Rest easy. From a practical standpoint, WPA is fairly safe. There are far too many salted key-derived hashes to process. The Wi-Fi Alliance got that portion of the protocol right. Even with a pair of Radeon HD 6990s, we're limited to about 200 000 passwords per second, and that means any alphanumeric password longer than seven characters is almost impossible to crack in under a year. That's a long time to wait for free Internet access from the guy next door (you'd be better off using social engineering to get the password from him; try a 12-pack of Newcastles). After adding a few special keystrokes, brute-force attacks look completely infeasible on passwords longer than six characters. Though, the point is kind of moot considering WPA/WPA2 requires a password longer than eight characters.
Unfortunately, most of us use passwords that include words. As such, those passwords are vulnerable to dictionary-based attacks. The number of words in conversational English is in the tens of thousands. A single GeForce GTX 590 can manage at least 50 000 passwords per second against a WPA-protected network. Even if you add a few variations, you really only need to spend a day or two crunching passwords to break the proverbial lock. Why? Because an entire word is functionally the same as a single letter, like "a." So searching for "thematrix" is treated the same as "12" in a brute-force attack.
Ideally, you should avoid the following if you are trying to make your network more secure:
- Avoid words from the dictionary. The Oxford English dictionary contains fewer than 300 000 entries if you count words currently in use, obsolete words, and derivative words. That's nothing for a GeForce GTX 590 or Radeon HD 6990.
- Avoid words with numbers appended at the end. Adding 1 to the end of password doesn't make it a more secure. We can still crunch the entire English dictionary and numbers in half a day with a pair of Radeon HD 6990s.
- Avoid double words or simple letter substitution. PasswordPassword only doubles the number of words that we have to search. That's still fairly easy, considering how fast we can scan words. Also, p@55w0rd isn't a much more secure password. Password crackers know all the usual shortcuts, so don't take that route.
- Avoid common sequences from your keyboard. Adding QWERTY to the dictionary of tested passwords isn’t hard work. That's another shortcut to avoid.
- Avoid common numerical sequences. 314159 may be easy to remember. It's Pi, after all. But it's also something that's easy to test for.
- Avoid anything personally related, such as your license plate, social security number, past telephone number, birthday, and so on. We live in a world where a lot of information is public domain. If you have a Facebook or Twitter account, the amount of information available keeps growing.
To the average hacker, WPA holds up remarkably well. Even if you're using a short, random password, the cracking speed we see from GPUs is simply too slow as a result of the high computational requirements for the key derivation function.
The real threat is distributed computing. Buying four Radeon HD 6990s help you reach close to half a million passwords per second. But the cards alone cost nearly $3000. If we went to the trouble of tweaking the Pyrit code, it would be possible to achieve the same performance for $8 by renting 10 EC2 Cluster GPU Instances. If you're unable to scale your code for automation, you can still achieve that level of performance by manually managing the workload across multiple servers.
The current distributed offerings might not offer impressive performance, but their speed isn't what worries us. It's their low price tag. Moxie Marlinspike, a hacker, runs a service called WPACracker, which can be used to crack the four-way handshake capture of WPA-PSK using 400 CPU clusters on Amazon's EC2 cloud. This scaling allows you to crunch through a 135 million word dictionary specifically created for WPA passwords in under 20 minutes. Even though that's ~112 500 passwords per second (equivalent to a single GeForce GTX 590), you only have to pay $17.
| Total Search Time Assuming 1 Million WPA Passwords/Second(Cost using EC2 Reserved Rate) | Passwords Between 1 and 4 Characters | Passwords Between 1 and 6 Characters | Passwords Between 1 and 8 Characters | Passwords Between 1 and 12 Characters |
|---|---|---|---|---|
| Numbers | InstantEstimated Cost: $0.74 | InstantEstimated Cost: $0.74 | 2 minutesEstimated Cost: $0.74 | 12.75 daysEstimated Cost: $226 |
| Lower-case | InstantEstimated Cost: $0.74 | 5 minutesEstimated Cost: $0.74 | 2.5 daysEstimated Cost: $44.40 | 3147 years |
| Alphanumeric (including Upper-case) | InstantEstimated Cost: $0.74 | 16 hoursEstimated Cost: $11.84 | 7 years | 103 981 388 years |
| All (Printable) ASCII characters | 2 minutesEstimated Cost: $0.74 | 9 daysEstimated Cost: $159.84 | 231 years | Next Big Bang |
Thomas Roth, a security expert who helped highlight the flaws of the Sony PlayStation Network, seems to be the only person that has publicly demonstrated a properly-scaled GPU distributed cracking network. His setup linearly scales the speed of individual EC2 Cluster GPU Instances by balancing the workload and reducing bottlenecks. So, even though we need about 10 Radeon HD 6990s split among three desktop systems to reach 1 million WPA passwords per second, we can do the same by spending $60 to rent 20 Cluster GPU Instances (the limit was recently increased to 64 servers). The only hurdle is optimizing code in Amazon's cloud. And no, we aren't going to share our code.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Computational clouds like Amazon's EC2 were originally intended to help developers and scientists solve complex mathematical problems without a heavy investment in building a server farm. I doubt that Amazon had hacking in mind, but the cat's out of the bag. The fact is that it can and will be done. If someone wants onto your network badly enough, your strong password might be the only thing stopping them.
And that's ultimately why you need to change your password strategy. The fact that that most of us use alphanumeric passwords to lock our Wi-Fi networks only serves to weaken them. How many of us know friends or family who never changed their default router passwords, either? We know that AT&T's U-verse routers (identified with SSIDs like 2Wirexxx, where x is a number) come with default passwords limited to numbers and are only 10 characters in length. Using a pair of Radeon HD 6990s, you can mow through every possibility in under 14 hours.
Besides using a unique SSID, a WPA password should follow the following rules:
- Fully random
- At least eight characters in length.
- Contain at least one upper-case letter
- Contain at least one lower-case letter
- Contain at least one special character, such as @ or !
- Contain at least one number
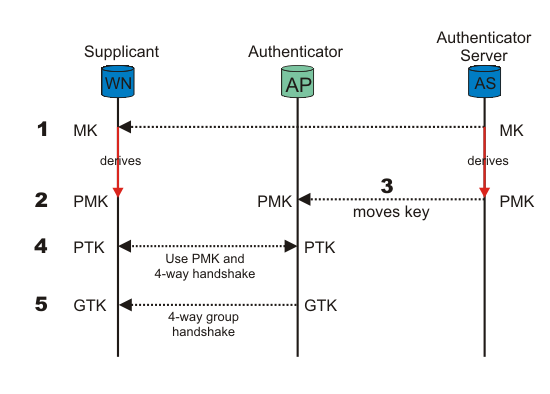
For those of you in IT, you're better off investing in an authentication server, which adds another layer of wireless security since the master key is hidden from the user and generated dynamically. This means that the PMK is a fresh symmetric key particular to the session between the client and AP. It infinitesimally increases the complexity of a brute-force attack. In fact, as an IT professional, you should worry more about someone bribing an employee or stealing an unencrypted laptop.
Keeping Perspective
Whenever someone talks about security, it's easy to go overboard. We get so caught up in locking down our information that we forget to ask ourselves if we have anything worth stealing.
To some degree, everyone has information they'd prefer stayed private, which is why we think everyone should be putting some effort into keeping intruders out. And the fact of the matter is that most troublemakers will see your locked access point and simply move on. Users in the Netstumbler forums estimate that 10-20% of networks still use WEP encryption. If someone really wants to hijack a network, they'll likely look for a WEP-protected target first. Whether someone is willing to spend hours, days, or even years banging on your WPA-secured fortress will depend on the state secrets hiding on the other side.
The fact of the matter is that most of us aren't high-profile enough to attack, so long as the right protocol is in place. It's often said that a pump-action shotgun is the best tool for home defense, not because it's any scarier than a handgun or rifle, but because the sound of a shell cycling is enough to make any intruder turn and flee. Well, consider WPA your pump-action.
Of course, not everyone agrees that security is necessary. In fact, many people purposely run open Wi-Fi networks. According to a post at TorrentFreak, the legality of holding a network owner responsible for the actions of users remains in doubt. One defendant writes, "Not all unsecured networks are due to a lack of technical knowledge. Some of us leave them open to friends and others out of a sense of community." That's super-generous and all, but if you're using one of those networks, just be aware that you're already rubbing shoulders with the bad guys.
Current page: Securing Your WPA-Protected Network
Prev Page Nvidia's Tesla And Amazon's EC2: Hacking In The Cloud-
fstrthnu Well it's good to see that WPA(2) is still going to hold out as a reliable security measure for years to come.Reply -
runswindows95 The 12 pack of Newcastles works for me! Give that to me, and I will set you up on my wifi! Free beer for free wifi!Reply -
Pyree runswindows95The 12 pack of Newcastles works for me! Give that to me, and I will set you up on my wifi! Free beer for free wifi!Reply
Then either beer at your place is really expensive or internet is really cheap. Need 6x12 pack for me. -
compton Thanks for another article that obviously took a lot of work to put together. The last couple of articles on WiFi and archive cracking were all excellent reads, and this is a welcome addition.Reply -
mikaelgrev "Why? Because an entire word is functionally the same as a single letter, like "a." So searching for "thematrix" is treated the same as "12" in a brute-force attack."Reply
This is an extremely wrong conclusion. Extremely wrong. -
What about the permutations of the words?Reply
i.e ape can be written:
ape, Ape, aPe, apE, APe, aPE, ApE, APE.
Thats 2^3=8 permutations. Add a number after and you get (2^3)*(10^1)=80 permutations.
You can write PasswordPassword in 2^16=65536 ways.
How about using a long sentence as a password?
i.e MyCatIsSuperCuteAndCuddly, thats 2^25 permutations :) -
molo9000 Any word on MAC address filtering?Reply
Can you scan for the MAC addresses? It's probably easy to get and fake MAC adresses, or it would have been mentioned.
*scans networks*
12 networks here,
1 still using WEP
10 allowing WPA with TKIP
only 1 using WPA2 with AES only (my network) -
agnickolov Considering my WPA password is over 20 characters long I should be safe for the foreseeable future...Reply -
aaron88_7 "12345, that's amazing, I've got the same combination on my luggage!"Still makes me laugh every time!Reply