Microsoft Intros Pluton Processor, Intel and AMD To Use Xbox Security Approach for PCs
Follow the leader, the security edition
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
You are now subscribed
Your newsletter sign-up was successful
EDIT 11/17/2020 10:45am PT: The article has been corrected to clarify that the Pluton processor is separate from the AMD Secure Processor:
In response to a new wave of attacks that have compromised standard approaches to Windows security, Microsoft announced its Pluton security processor that will reside inside of future consumer chips from both AMD and Intel – but it's built using a technology that Microsoft and AMD pioneered with the custom processors for Xbox game consoles. It also leverages a standard feature found on AMD's EPYC server processor chips. Now Intel will adopt a similar approach to help secure PCs.
The new collaboration between Microsoft, AMD, Intel, and Qualcomm will enable more robust security that helps prevent physical attacks and encryption key theft while protecting against firmware attacks. Microsoft will also use the technology to streamline firmware updates via Windows Update.
The Pluton security processor comes as a result of recent new attack vectors that indirectly compromise the Trusted Platform Module (TPM), which has long been the preferred method of securing PCs from potential threats. The TPM, a small secondary chip inside the system that stores encryption keys for services like Bitlocker and Windows Hello, is still robust enough to protect encryption keys but malicious actors have learned how to penetrate the bus that connects the TPM to the CPU through physical attacks, thus compromising a system.
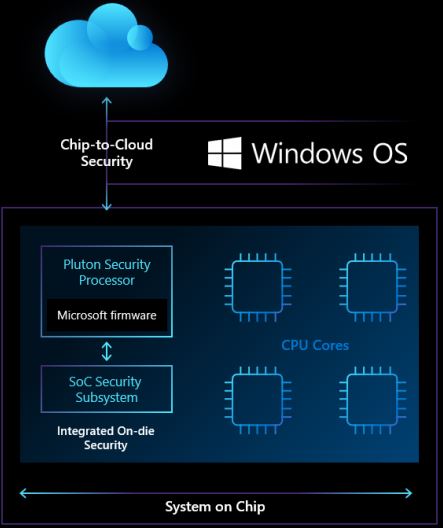
Microsoft says that security must be built directly into the processor to prevent those attacks, hence the Pluton security processor. The new approach to securing the system isn't really new at all, though - AMD pioneered the in-built security processor approach with the AMD Security Processor (ASP) in the Xbox game console back in 2013. This in-built 32-bit ARM Cortex-A5 processor is sandboxed from the rest of the processor, thus protecting it from attacks with exploits like Spectre, and provides secure encryption key generation and management to enable a hardware root of trust.

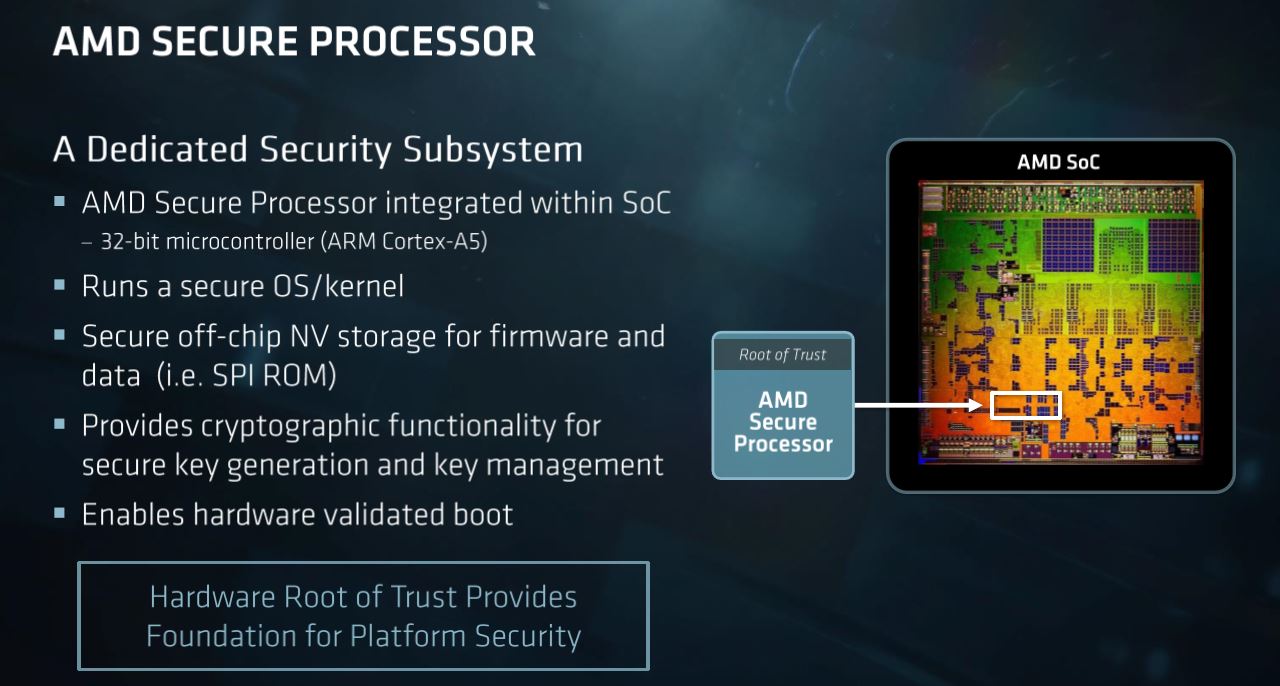
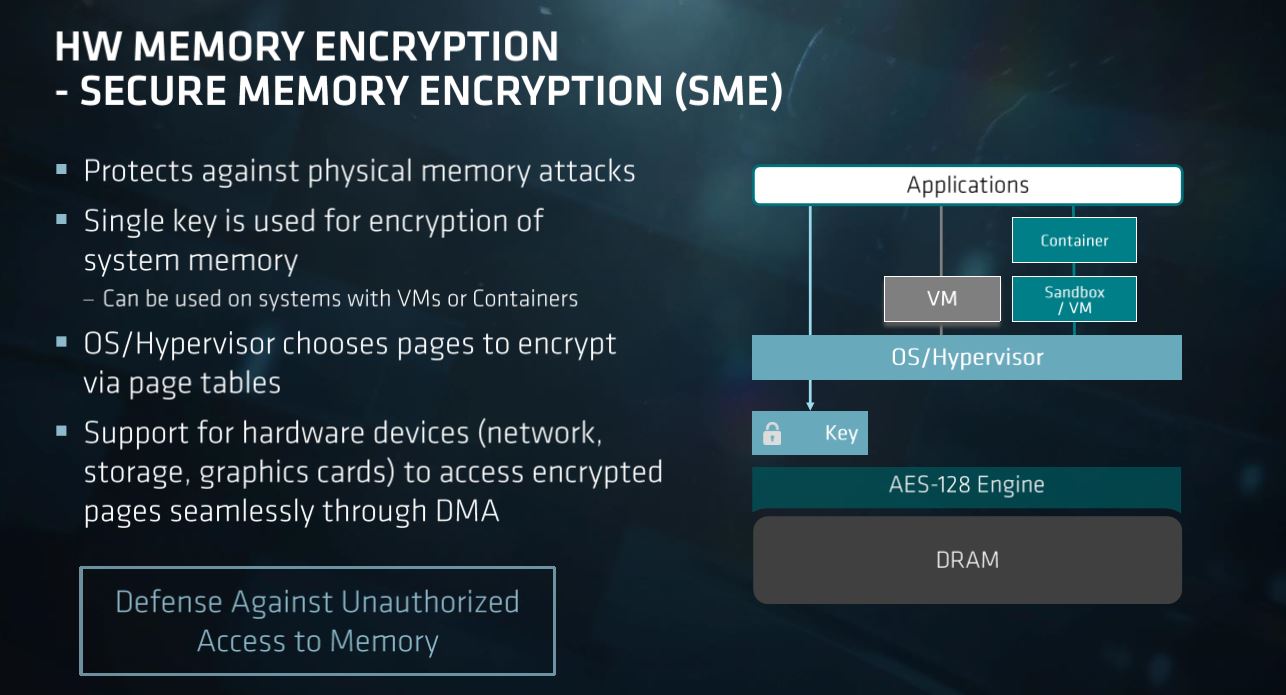
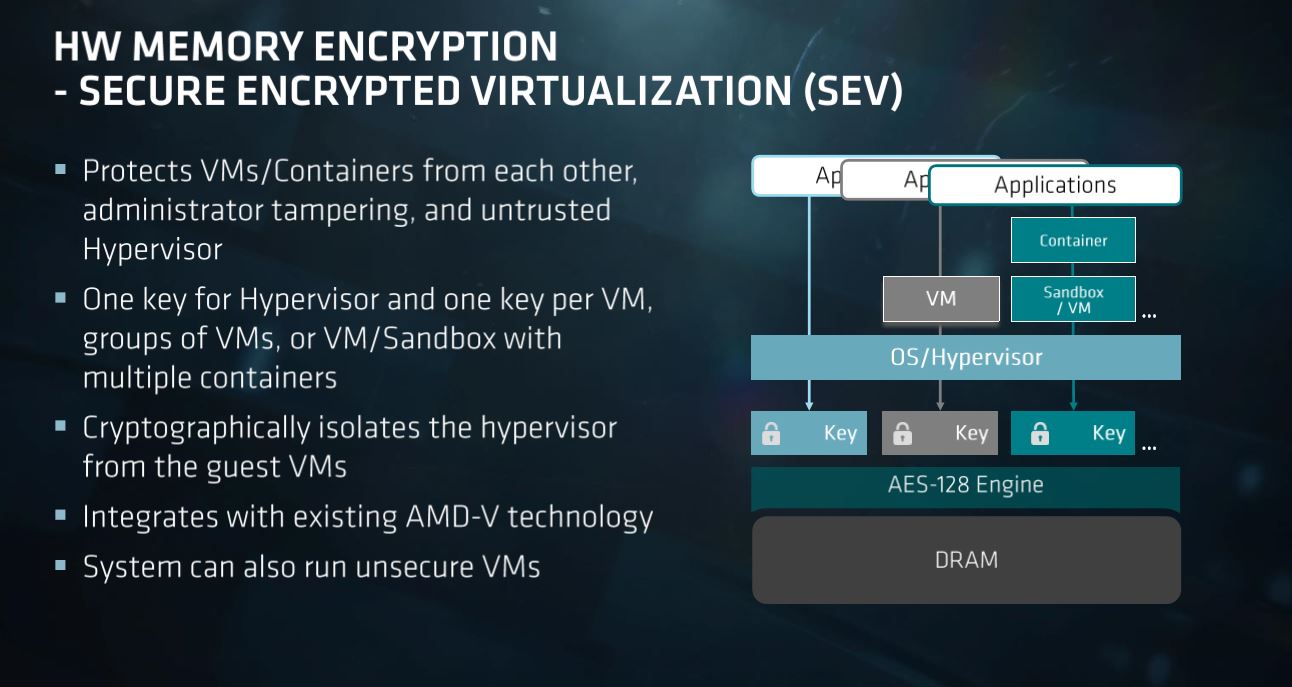
AMD uses this same approach for its EPYC server chips and its commercial processors. For the Xbox, AMD's secure processor communicates with Microsoft's Pluton Security Processor to enable tight integration between Microsoft's software and AMD's security hardware. AMD says it will be first to enable the same feature on all of its future client CPUs and APUs, though it hasn't provided a specific timeline for the release.
Meanwhile, Intel says that it will continue to leverage its Hardware Shield feature in vPro, which only comes with specific commercial SKUs, but now also enable the Microsoft Pluton security processor to provide multiple root of trust options. Intel hasn't provided a timeline for its adoption of the feature but says that "Intel plans to work with Microsoft to bring Pluton to these customers, as a choice, at scale." It's a bit unclear if Intel means the company will not enable the feature on all chips, thus providing customers with the choice to purchase more expensive processors with the feature – much like with its vPro-enabled chips.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
The Pluton processor will emulate a TPM to maintain broad compatibility with APIs like BitLocker and System Guard. Pluton also uses a Secure Hardware Cryptography Key (SHACK) technology that prevents exposing cryptographic keys, even to the Pluton firmware itself, which will ultimately protect user information from physical attacks.
Finally, the Pluton processor secures the firmware updating process, streamlining the Windows Update process to provide a more unified and consistent method to update system firmware. This has become more important as a slew of security vulnerabilities have necessitated a rapid cadence of new firmwares to plug security holes like Meltdown and Spectre, but the current delivery system is fragmented. By building this functionality into the processor and using it to enable Windows Update to update firmware securely, Microsoft hopes that it, and the silicon vendors, can react to vulnerabilities quicker.

Paul Alcorn is the Editor-in-Chief for Tom's Hardware US. He also writes news and reviews on CPUs, storage, and enterprise hardware.
-
JfromNucleon The title is somewhat misleading, it implies that Intel is copying it when it isn't but is rather in a "partnership".Reply -
jkflipflop98 It won't take long for this to become a vulnerability itself. It's just adding a whole bunch more points of failure into the system to be attacked. Someone somewhere is going to figure out some edge-case vector and then you're fried.Reply -
Paul Alcorn ReplyJfromNucleon said:The title is somewhat misleading, it implies that Intel is copying it when it isn't but is rather in a "partnership".
A "partnership" to adopt a security technique that AMD developed and has used since 2013 - and currently uses in several of its shipping lines of processors. Fair to say Intel is adopting the same approach - the title does not state 'copying.' -
JfromNucleon Reply
Oh wait, seems the title changed or something cause when I came to this article it said something like "Intel copies AMD" but yeah ok I get that argument, didn't realize AMD used it for that longPaulAlcorn said:A "partnership" to adopt a security technique that AMD developed and has used since 2013 - and currently uses in several of its shipping lines of processors. Fair to say Intel is adopting the same approach - the title does not state 'copying.' -
eye4bear Am I the only one who DOES NOT want Microsoft software controlling their PC processor which is running a Linux operating system because they do not trust Windows on their PC?Reply -
setx Reply
Exactly. It's a joke to trust your system security to MS. I hope that this "security" co-processor can be completely disabled by BIOS (some hardware kill switch would be better, but little hope there).eye4bear said:Am I the only one who DOES NOT want Microsoft software controlling their PC processor which is running a Linux operating system because they do not trust Windows on their PC? -
kal326 Reply
There will have to be something available to either bypass when using other OSes or support within other OSes.setx said:Exactly. It's a joke to trust your system security to MS. I hope that this "security" co-processor can be completely disabled by BIOS (some hardware kill switch would be better, but little hope there).
AMD has been using something similar in Epyc for a while and DC gear and other OS support is widespread. -
neojack so it's like a v2 of the existing TPM chip ? (that is disabled anyways if secure boot is disabled) am i right ?Reply -
d0x360 So they could block unproved programs or modification to programs if the publisher says no.. Yeah it would actually fix cheating in games on pc but it would also probably block mods for tons of games.Reply
Gta online as an example... There are mods that don't help rockstar make money and they are roleplay servers which use a mod to allow private servers. That could be easily banned by this chip
Anyone remember palidum? They tried to do this with Intel like 17 years ago or so and people revolted. Haven't heard a peep about this. -
d0x360 Replyeye4bear said:Am I the only one who DOES NOT want Microsoft software controlling their PC processor which is running a Linux operating system because they do not trust Windows on their PC?
No but considering you can remove anything you want via powershell your lack of trust makes little sense.