Wi-Fi Security: Cracking WPA With CPUs, GPUs, And The Cloud
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
You are now subscribed
Your newsletter sign-up was successful
Network Security: The First Line Of Defense
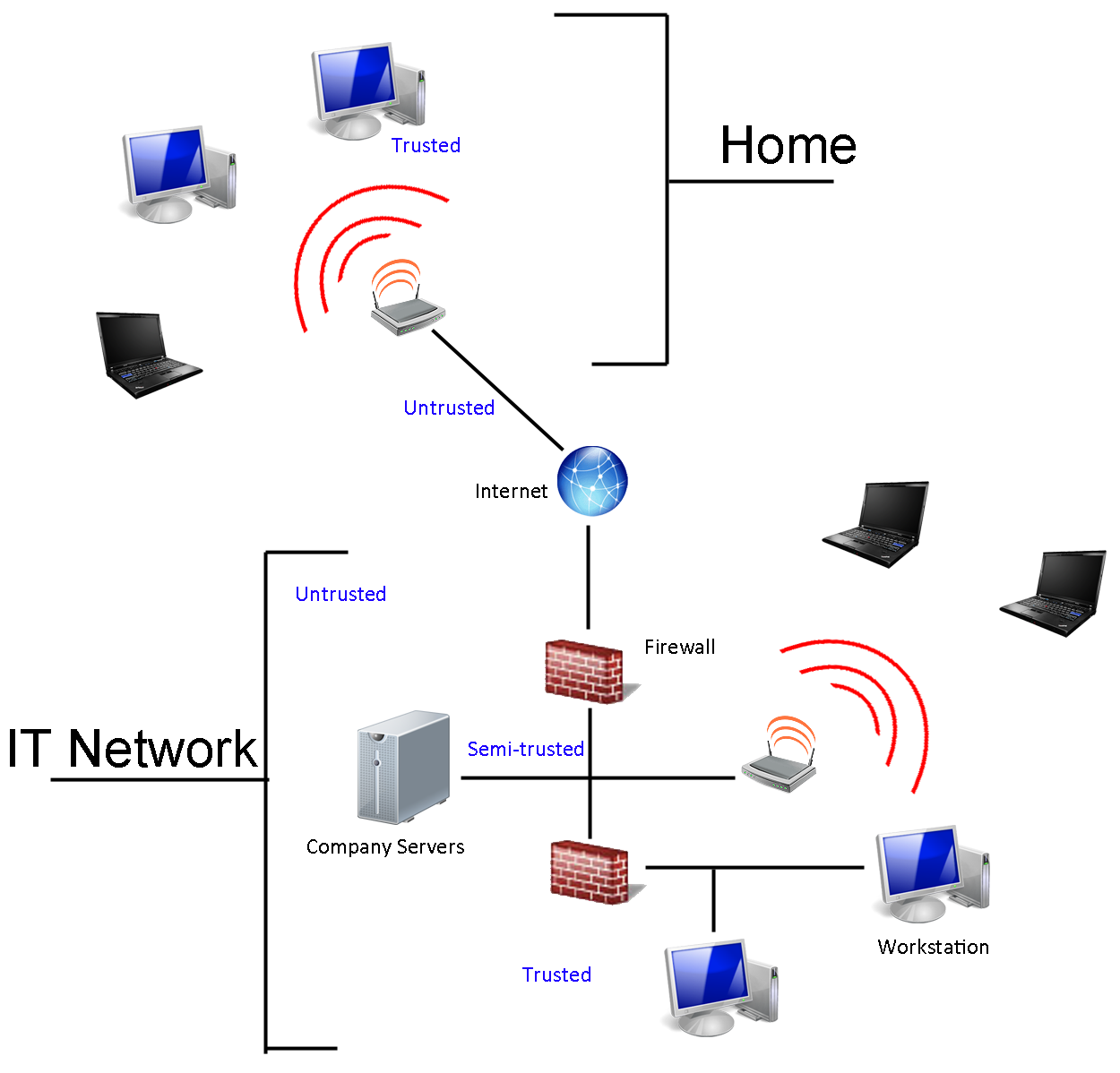
There's no such thing as guaranteed security for folks connected to the Internet. However, by adding additional layers of protection, it's possible to make a system increasingly difficult to compromise. Banks have multiple safeguards to prevent physical robberies, and well-built networks employ the same thinking to keep digital assets safe. You don't usually see the same thoroughness in home networks, though, because it costs a lot and requires a particular expertise in order to stay one step ahead of of the folks who'd like access to everything behind your firewall.
Instead of a tiered approach to security, most of us are only protected by our routers. That's what separates the local network from the Internet. It prevents strangers from using an IP address to access your system directly. And the router represents the first security layer in your network.
But it isn't just your first line of defense; it's also the most important. Why? Most people believe that you can enhance data security by installing a software firewall and a data encryption scheme like TruCrypt. However, most of us also make at least some of our data available to other users on our networks as a matter of convenience and easy accessibility. Perhaps we do this without even thinking that it could be seen by someone else. Regardless, when we do this, the integrity of our wireless network, protected by certain authentication technologies, is all that keeps our precious information safe from anyone in range and able to circumvent our safeguards. Adding additional security measures to keep Internet-based traffic out doesn't change that fact.
So, sure, streaming a high-def movie from your NAS to an HTPC in the living room might be easier as a result of wireless access. But anyone able to breach those invisible walls can do the same thing. And that doesn't even take into account the damage they can do on the Internet from an address that'd appear to be coming from your own little network.
In the early days of home networking, you could rely on the physicality of wired networking to restrict access. Now, with wireless technology, you have to worry about attacks coming from the Internet (hopefully being stymied by your firewall) and breaches closer to home that might allow an unsavory character right onto your network alongside other trusted devices. There is where stronger wireless security comes into play. That's the easiest way to protect your network from intrusion.
Now, we're assuming that most Tom's Hardware readers aren't setting up their access points and leaving them wide open to the pillaging of neighbors. You're using some sort of security protocol to at least discourage casual Web browsers looking to bum a ride on your bandwidth or amateur script kiddies testing their mettle.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Current page: Network Security: The First Line Of Defense
Prev Page Test Setup Next Page WEP Is Dead, Haven't You Heard?-
fstrthnu Well it's good to see that WPA(2) is still going to hold out as a reliable security measure for years to come.Reply -
runswindows95 The 12 pack of Newcastles works for me! Give that to me, and I will set you up on my wifi! Free beer for free wifi!Reply -
Pyree runswindows95The 12 pack of Newcastles works for me! Give that to me, and I will set you up on my wifi! Free beer for free wifi!Reply
Then either beer at your place is really expensive or internet is really cheap. Need 6x12 pack for me. -
compton Thanks for another article that obviously took a lot of work to put together. The last couple of articles on WiFi and archive cracking were all excellent reads, and this is a welcome addition.Reply -
mikaelgrev "Why? Because an entire word is functionally the same as a single letter, like "a." So searching for "thematrix" is treated the same as "12" in a brute-force attack."Reply
This is an extremely wrong conclusion. Extremely wrong. -
What about the permutations of the words?Reply
i.e ape can be written:
ape, Ape, aPe, apE, APe, aPE, ApE, APE.
Thats 2^3=8 permutations. Add a number after and you get (2^3)*(10^1)=80 permutations.
You can write PasswordPassword in 2^16=65536 ways.
How about using a long sentence as a password?
i.e MyCatIsSuperCuteAndCuddly, thats 2^25 permutations :) -
molo9000 Any word on MAC address filtering?Reply
Can you scan for the MAC addresses? It's probably easy to get and fake MAC adresses, or it would have been mentioned.
*scans networks*
12 networks here,
1 still using WEP
10 allowing WPA with TKIP
only 1 using WPA2 with AES only (my network) -
agnickolov Considering my WPA password is over 20 characters long I should be safe for the foreseeable future...Reply -
aaron88_7 "12345, that's amazing, I've got the same combination on my luggage!"Still makes me laugh every time!Reply