Backdoor uncovered in China-made patient monitors — Contec CMS8000 raises questions about healthcare device security
US security agency reports that China-made hospital patient monitors contain a backdoor that sends confidential monitoring data to a third-party university.
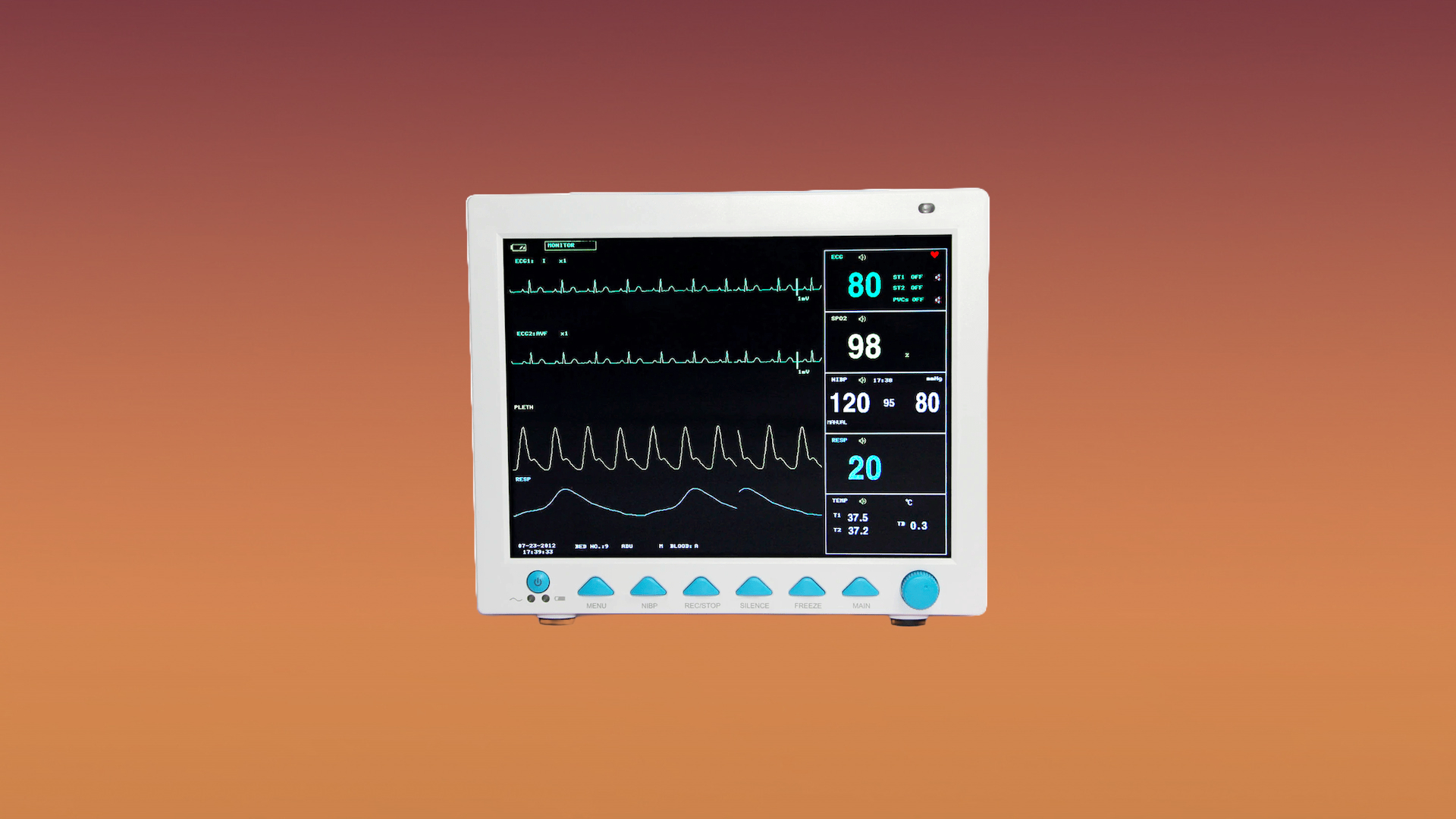
The US-based Cybersecurity & Infrastructure Security Agency recently released an investigation report involving three firmware versions used in a patient monitoring system called Contec CMS8000, used in hospitals and healthcare facilities. It was discovered that these devices had a backdoor with a hard-coded IP address, allowing the patient data to be transmitted. This is possible as the devices will enable a connection to a central monitoring system via a wired or wireless network, according to the product description.
The agency revealed the codes that transmit data to a particular IP address. This decoded data contains detailed information, such as the doctor's name, patients, hospital department, admission date, date of birth, and other information about the people who used this device. This vulnerability is filed under CVE-2025-0626 with a CVSS v4 score of 7.7 out of 10. Two other vulnerabilities were filed under CVE-2024- 12248, which indicates that it could allow an attacker to write data remotely to execute a code, and CVE-2025-0683, which relates to privacy vulnerability.
"These cybersecurity vulnerabilities can allow unauthorized actors to bypass cybersecurity controls, gaining access to and potentially manipulating the device," the FDA said, adding it's "not aware of any cybersecurity incidents, injuries, or deaths related to these cybersecurity vulnerabilities at this time."
The agency mentioned that Contec Medical Systems is a medical device manufacturer based in China whose products are in hospitals, clinics, and other healthcare facilities in the European Union and the United States. However, a quick search revealed that these can also be purchased via eBay for $599. These devices are also relabelled as Epsimed MN-120, according to the FDA. Contec is a major manufacturer of medical devices that are sold in over 130 countries and are FDA-approved. The CISA research team recently discovered this vulnerability as a part of its coordinated vulnerability disclosure process.
The agency mentions the IP address is not associated with any medical device manufacturer. Still, it is a third-party university, though it doesn't mention the university, the IP address, or the country it is sending data to. The CISA also ruled out this coding was meant to be an alternative update system as it does not contain standard update procedures such as tracking updated versions or doing integrity checks. Instead, it has the remote file shared and transmitted to the IP address. As a solution for such a networked device, the FDA strongly recommends disconnecting the monitoring device from its network and monitoring the patient's vital stats and physical condition.
Breach of Privacy and Confidential Information
The Contec CMS8000 explicitly monitors a patient's vital signs while storing its data in great detail, including electrocardiogram, heart rate, blood oxygen, blood pressure, respiration rate, and many others. This will raise privacy concerns since the FDA released a notice implying that they and medical facilities are unaware of its purpose. According to the report, Contec has not addressed the matter yet and has not released any firmware to fix this.
Many networked devices have been reported to have vulnerabilities, not exclusively being from a Chinese-based company. However, given the key role of such devices, due diligence, checks, and disclosures will be vital. Even if the data is transmitted to the university irrespective of its location, and since the report implies neither the FDA nor the hospitals are aware of this backdoor, it violates the privacy of every patient and doctor, not limited to one region. There have been multiple cyber attacks from China since January and concerns involving TP-Link, which would naturally heighten the problem with these devices.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.

Roshan Ashraf Shaikh has been in the Indian PC hardware community since the early 2000s and has been building PCs, contributing to many Indian tech forums, & blogs. He operated Hardware BBQ for 11 years and wrote news for eTeknix & TweakTown before joining Tom's Hardware team. Besides tech, he is interested in fighting games, movies, anime, and mechanical watches.
-
Dr3ams I think any computer hardware, no matter where it's made, has the potential for "backdoors". Most governments wouldn't be able to resist the temptation. For consumers, there is no way of getting around it.Reply -
KennyRedSocks "it doesn't mention the university, the IP address, or the country it is sending data to"Reply
It doesn't sound like they're too sure of their findings. -
JTWrenn Reply
That selective quotation really makes you look like you have an agenda here. Here is the part you cut out with that quotingKennyRedSocks said:"it doesn't mention the university, the IP address, or the country it is sending data to"
It doesn't sound like they're too sure of their findings.
"The agency mentions the IP address is not associated with any medical device manufacturer. Still, it is a third-party university, though it doesn't mention the university, the IP address, or the country it is sending data to. The CISA also ruled out this coding was meant to be an alternative update system as it does not contain standard update procedures such as tracking updated versions or doing integrity checks. Instead, it has the remote file shared and transmitted to the IP address."
They know what it is but have not shared it. Stop it. -
ezst036 Of course they found a back door. They'll find others.Reply
We live in an age where information is more valuable than money and China knows they need to have all the information. -
mitch074 Reply
The fact that it's using a fixed IP address to a university smells like 2 possibilities :ezst036 said:Of course they found a back door. They'll find others.
We live in an age where information is more valuable than money and China knows they need to have all the information.
1- early debug/qualification code that wasn't removed at the end of the qualification program (any code modification requires validation when it's for medical devices - that enables deactivating such remote access)
2- cheap way for a university to get samples data.
If it were a real back door, it would have been obfuscated, and if it were for a state agency, it would not point to a public facility.
Also, this kind of 'attack' is easy to circumvent : block non-approved IP addresses in outbound traffic. -
USAFRet Reply
For reliable devices, that should net be needed.mitch074 said:Also, this kind of 'attack' is easy to circumvent : block non-approved IP addresses in outbound traffic.
Whatever the reason, why is it there?
Just like with inexpensive security camera things...a hardcoded admin pwd, that you, the buyer, has no influence over.
Left there by clueless/incompetent devs, or on purpose to extract data. -
King_V Reply
It's only pathetic if it doesn't work. Otherwise, it's a bargain way to get data that would otherwise be far more expensive to acquire.P.Amini said:What China is doing is really pathetic.. -
Vanderlindemedia ReplyDr3ams said:I think any computer hardware, no matter where it's made, has the potential for "backdoors". Most governments wouldn't be able to resist the temptation. For consumers, there is no way of getting around it.
Yep but this actually, contains a backdoor. Sending private or confidential information, such as name of the doctor, the patient and all that, to a unknown source.
Company's need to double packet sniff check all the outgoing data from such places. -
NinoPino Reply
Also if the IP is that of a USA University ?P.Amini said:What China is doing is really pathetic..