Locking up Linux: Creating a Cryptobook
Encryption Products For Linux, Continued
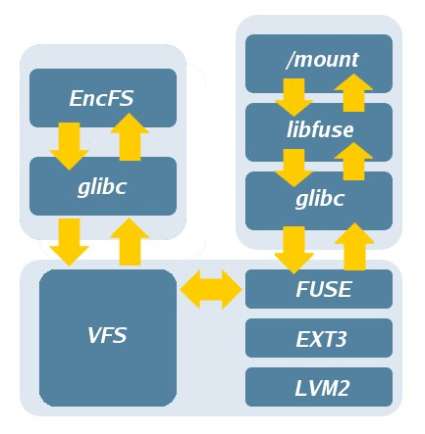
Userspace overlay illustrating FUSE and EncFS interoperation.
Underneath the file system abstraction layer you'll find block-level encryption schemes, such as the one employed by LUKS. This sort of scheme works on a disk block at a time, completely oblivious to any higher-level file system abstractions. It can thus be used for swap space, containers, or entire raw drive volumes, including a completely encrypted root partition.
LUKS operates without explicit knowledge of file system format.
LUKS is designed according to the Trusted Key Setup #1 (TKS1) and is compatible with Windows using a sharable file system format. It is secure against low-entropy attacks (ideal for mobile users), supports the issuance and revocation of Gnu Privacy Guard (GPG) keys, and is completely free of charge. LUKS does much more than any other implementation covered in this article, and also provides a number of facilities for creating and managing LUKS-encrypted block devices.
CryptoFS accepts only a single password for usage, while a LUKS-encrypted volume can be keyed with any number of Pretty Good Privacy (PGP) keys and additional passphrases for each key. EncFS also uses a password to protect files, and retains a volume key in the parent directory to which the password corresponds.
One telling distinction between a block-level implementation and a userspace implementation is in its practical application. At the lower level, data can be seamlessly transmitted to the file system, which in turn handles read and write operations more efficiently.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Current page: Encryption Products For Linux, Continued
Prev Page Technical Discussion On Encryption Next Page Test Setup