Researchers Intercept Typed Mobile Payments PIN Through Wi-Fi Signals
According to a new research paper written by academics at Shanghai Jiao Tong University, the University of Massachusetts at Boston, and the University of South Florida, attackers could analyze interruptions in Wi-Fi signals that are caused by users moving their fingers on a touchscreen smartphone. The paper said that this way, the attackers could accurately reverse engineer what the user was typing on the device’s virtual keyboard.
WindTalker - Intercepting Typed Characters Wi-Fi Signals
Lately, we’ve seen more and more research that uses attacks via radio signals, a device’s microphone, motion sensors, and even visible light from a camera, and every time, these sort of attacks seem to be getting easier and more practical. In previous research, the attackers would still need to be in close proximity to the user's device, or they needed to control the device. The new type of attack, called WindTalker, can succeed if the attacker merely tricks the user into connecting to a rogue free Wi-Fi hotspot.
How The Attack Works
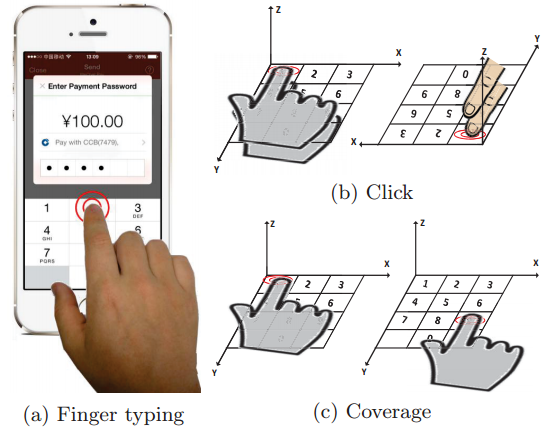
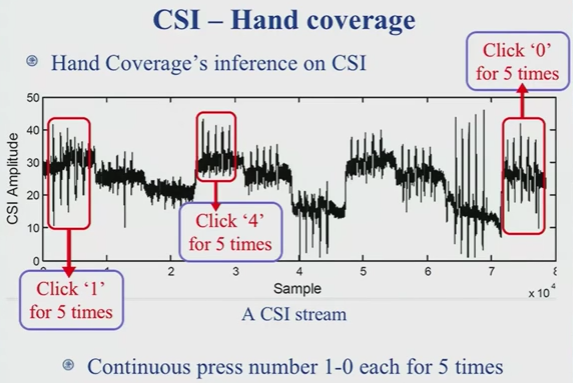
The attack utilizes radio signals called Channel State Information (CSI), which is part of the Wi-Fi protocol. When a user’s fingers move across a touchscreen, the Wi-Fi signal’s CSI properties are altered. These alterations can later be decoded by an attacker who controls the Wi-Fi hotspot.
The attacker can identify a user’s typed characters with an average accuracy of 68.3%. The accuracy can vary based on the smartphone model being used. However, the more the user types, and the more data the attacker can collect, and therefore the greater the accuracy.
The researchers tested WindTalker in a real-world scenario and were able to recover a user’s mobile payment PIN when the user tried to create an Alipay mobile transaction. According to the researchers, the Alipay servers used a fixed range of IPs, which made it easier for them to collect the user’s PIN when the user tried to contact the servers.
WindTalker can succeed even if the user’s connection uses HTTPS, because the user’s characters are recorded as they are typed on the device. Therefore, the connection between the device and a server being encrypted is completely irrelevant.
Defensive Strategies
Researchers presented several methods to defend against this type of attack. The simplest would be for users to not connect to open Wi-Fi hotspots, as there is a high chance they could be controlled by random attackers. Another would be to randomize the PIN keypad so that it’s more difficult to identify what numbers make up a PIN.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
OS and device vendors will also need to better prepare for such types of attacks and develop technologies against them so that all of their users are protected by default.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
Daekar3 You know... I'm starting to think we're better off with gold coins or something. The security issues that spider across the entire financial and payment infrastructure are just getting ridiculous.Reply